难度和祥云杯差不多,都挺难的(我菜)
队伍成绩:1118pt/11kill/33名/1154有解/1560登录/2157报名
个人成绩:503pt/5kill/57名/1465有解/5405登录/7967报名/1二血
Misc
签到 [9pt 1139killed]
题目
[0146, 0154, 0141, 0147, 0173, 0167, 063, 0154, 0143, 0157, 0155, 0145, 0137, 0164, 0157, 0137, 062, 0157, 0156, 0147, 0137, 0150, 063, 0156, 0147, 0137, 0142, 0145, 061, 0175]
WriteUp
直接八进制转文本,得到flag。
flag
flag{w3lcome_to_2ong_h3ng_be1}
马赛克 [47pt 197killed]
题目

WriteUp
这题第一反应是上周的Github热门项目利用,后来也证实确实没错。(因为对这个项目印象深刻,所以拿了个二血)
项目的具体原理其实并不太复杂,就是把所有可能的字符组合像素给打码然后比对色块相似度,但是能想到这个思路的人属实牛逼。
命令:python depix.py -p mosaic.png -s images/searchimages/debruinseq_notepad_Windows10_close.png -o output.png
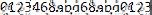
flag
flag{0123468abd68abd0123}
babymaze1 [68pt 130killed]
题目
大概就是netcat连上去走迷宫,一次性把路径输入然后依次走成21*11、41*21、61*31、81*41、101*51即可得到flag。
WriteUp
没啥好说的,就是个解析地图然后规划路径的ACM经典寻路问题。
exp
from v0lt import Netcat
def fuck(maze, x, y, bx, by, road):
if maze[x][y] == '$':
return road
if maze[x][y + 1] != '#' and (x != bx or y + 1 != by):
troad = fuck(maze, x, y + 1, x, y, road + "d") # d
if troad != "":
return troad
if maze[x + 1][y] != '#' and (x + 1 != bx or y != by):
troad = fuck(maze, x + 1, y, x, y, road + "s") # s
if troad != "":
return troad
if maze[x][y - 1] != '#' and (x != bx or y - 1 != by):
troad = fuck(maze, x, y - 1, x, y, road + "a") # a
if troad != "":
return troad
if maze[x - 1][y] != '#' and (x - 1 != bx or y != by):
troad = fuck(maze, x - 1, y, x, y, road + "w") # w
if troad != "":
return troad
return ""
nc = Netcat("182.92.203.154", 11001)
nc.read_until("Please press any key to start.")
nc.writeln("")
maze = nc.read_until(">")
maze = maze[maze.find("#"):-2]
print(maze)
line = maze.splitlines()
maze = [["#" for i in range(21)] for j in range(11)]
x = 0
for i in line:
y = 0
for j in i:
if j != "\0":
maze[x][y] = j
y += 1
x += 1
print(maze)
road = fuck(maze, 1, 1, 0, 0, "")
print(road)
nc.writeln(road)
maze = nc.read_until(">")
maze = maze[maze.find("#"):-2]
print(maze)
line = maze.splitlines()
maze = [["#" for i in range(41)] for j in range(21)]
x = 0
for i in line:
y = 0
for j in i:
if j != "\0":
maze[x][y] = j
y += 1
x += 1
print(maze)
road = fuck(maze, 1, 1, 0, 0, "")
print(road)
nc.writeln(road)
maze = nc.read_until(">")
maze = maze[maze.find("#"):-2]
print(maze)
line = maze.splitlines()
maze = [["#" for i in range(61)] for j in range(31)]
x = 0
for i in line:
y = 0
for j in i:
if j != "\0":
maze[x][y] = j
y += 1
x += 1
print(maze)
road = fuck(maze, 1, 1, 0, 0, "")
print(road)
nc.writeln(road)
maze = nc.read_until(">")
maze = maze[maze.find("#"):-2]
print(maze)
line = maze.splitlines()
maze = [["#" for i in range(81)] for j in range(41)]
x = 0
for i in line:
y = 0
for j in i:
if j != "\0":
maze[x][y] = j
y += 1
x += 1
print(maze)
road = fuck(maze, 1, 1, 0, 0, "")
print(road)
nc.writeln(road)
maze = nc.read_until(">")
maze = maze[maze.find("#"):-2]
print(maze)
line = maze.splitlines()
maze = [["#" for i in range(101)] for j in range(51)]
x = 0
for i in line:
y = 0
for j in i:
if j != "\0":
maze[x][y] = j
y += 1
x += 1
print(maze)
road = fuck(maze, 1, 1, 0, 0, "")
print(road)
nc.writeln(road)
print(nc.read())
print(nc.read())
print(nc.read())
print(nc.read())
print(nc.read())
print(nc.read())flag
flag{abaa5d766ea947b2b09c551f5e865d20}
babymaze2_beta [170pt 40killed]
题目
和上题基本上一样,不过没有多地图了,就一张61*31的图,但是有视野限制,只能看到3*3的范围。
WriteUp
刚开始是打算把上一题的脚本改成实时规划的,后来改出来也确实能走通,但是因为远程的网络io流交互耽误了时间,导致题目限制解题时间,没成功拿到flag。
后来队友表示这和今年国赛的题基本上一样,都是用python的input函数命令执行漏洞做的。
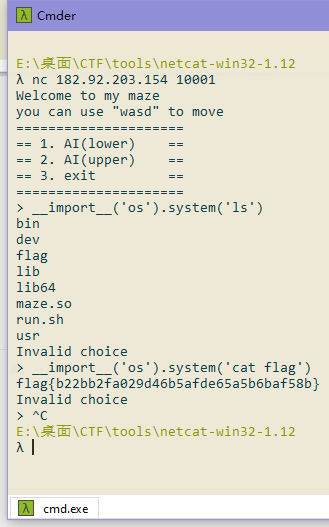
payload
__import__('os').system('ls')
__import__('os').system('cat flag')
exp
import time
from v0lt import Netcat
def fuck(nc, x, y, bx, by):
if x == 29 and y == 59:
print(nc.read())
print(nc.read())
print(nc.read())
print(nc.read())
print(nc.read())
print(nc.read())
return "true"
maze = nc.read_until(">")
maze = maze[-14:-3]
#print(maze)
if maze[9] != '#' and (x + 1 != bx or y != by):
nc.writeln("s")
ret = fuck(nc, x + 1, y, x, y)
if ret == "true":
return ret
else:
nc.writeln("w")
nc.read_until(">")
if maze[6] != '#' and (x != bx or y + 1 != by):
nc.writeln("d")
ret = fuck(nc, x, y + 1, x, y)
if ret == "true":
return ret
else:
nc.writeln("a")
nc.read_until(">")
if maze[1] != '#' and (x - 1 != bx or y != by):
nc.writeln("w")
ret = fuck(nc, x - 1, y, x, y)
if ret == "true":
return ret
else:
nc.writeln("s")
nc.read_until(">")
if maze[4] != '#' and (x != bx or y - 1 != by):
nc.writeln("a")
ret = fuck(nc, x, y - 1, x, y)
if ret == "true":
return ret
else:
nc.writeln("d")
nc.read_until(">")
return ""
nc = Netcat("182.92.203.154", 10001)
nc.read_until(">")
nc.writeln("2")
fuck(nc, 1, 1, 0, 0)flag
flag{b22bb2fa029d46b5afde65a5b6baf58b}
Crypto
common [209pt 29killed]
题目
from Crypto.Util.number import *
e1 = 28720970875923431651096339432854172528258265954461865674640550905460254396153781189674547341687577425387833579798322688436040388359600753225864838008717449960738481507237546818409576080342018413998438508242156786918906491731633276138883100372823397583184685654971806498370497526719232024164841910708290088581
e2 = 131021266002802786854388653080729140273443902141665778170604465113620346076511262124829371838724811039714548987535108721308165699613894661841484523537507024099679248417817366537529114819815251239300463529072042548335699747397368129995809673969216724195536938971493436488732311727298655252602350061303755611563
N = 159077408219654697980513139040067154659570696914750036579069691821723381989448459903137588324720148582015228465959976312274055844998506120677137485805781117564072817251103154968492955749973403646311198170703330345340987100788144707482536112028286039187104750378366564167383729662815980782817121382587188922253
flag = b"flag{xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx}"
f1 = bytes_to_long(flag[:21])
f2 = bytes_to_long(flag[21:])
c1 = pow(f1, e1, N)
c2 = pow(f2, e2, N)
print("e1 = ", e1)
print("e2 = ", e2)
print("N = ", N)
print("c1 = ", c1)
print("c2 = ", c2)
#e1 = 28720970875923431651096339432854172528258265954461865674640550905460254396153781189674547341687577425387833579798322688436040388359600753225864838008717449960738481507237546818409576080342018413998438508242156786918906491731633276138883100372823397583184685654971806498370497526719232024164841910708290088581
#e2 = 131021266002802786854388653080729140273443902141665778170604465113620346076511262124829371838724811039714548987535108721308165699613894661841484523537507024099679248417817366537529114819815251239300463529072042548335699747397368129995809673969216724195536938971493436488732311727298655252602350061303755611563
#N = 159077408219654697980513139040067154659570696914750036579069691821723381989448459903137588324720148582015228465959976312274055844998506120677137485805781117564072817251103154968492955749973403646311198170703330345340987100788144707482536112028286039187104750378366564167383729662815980782817121382587188922253
#c1 = 125774545911886560112703402972153322080506025378797523936708278181480201146872577291738201370911792392950418121767343486509724963000477466590009600240375221563806039364611362947152096656513910712238094956240996452246301471555709823003175801134035094856941903678067489942047840663479442285170087613352040341832
#c2 = 125874844114757588984441500491946737723620819049276461078841545869549114013042058416210220287667061892072831243333341942699313440553285306436999725802970995457080384300690875762412008576026273931144721166609563493297003298586115510199518494430188305644317422640652955882264990001338974742192006748451975507803WriteUp
这题是看着Lazzaro大佬的博客做的,具体原理没看明白,就不分析了,直接贴exp吧。
sage跑的结果是得到phi1和phi2,然后大部分情况下这两个值都没变,所以直接套脚本就能得到flag。
exp
exp.sage
n = 159077408219654697980513139040067154659570696914750036579069691821723381989448459903137588324720148582015228465959976312274055844998506120677137485805781117564072817251103154968492955749973403646311198170703330345340987100788144707482536112028286039187104750378366564167383729662815980782817121382587188922253
e1 = 28720970875923431651096339432854172528258265954461865674640550905460254396153781189674547341687577425387833579798322688436040388359600753225864838008717449960738481507237546818409576080342018413998438508242156786918906491731633276138883100372823397583184685654971806498370497526719232024164841910708290088581
e2 = 131021266002802786854388653080729140273443902141665778170604465113620346076511262124829371838724811039714548987535108721308165699613894661841484523537507024099679248417817366537529114819815251239300463529072042548335699747397368129995809673969216724195536938971493436488732311727298655252602350061303755611563
for i in range(731, 682, -1):
#print(i)
alpha2 = i / 2048
M1 = round(n ^ 0.5)
M2 = round(n ^ (1 + alpha2))
A = Matrix(ZZ, [
[n, -M1*n, 0, n^2],
[0, M1*e1, -M2*e1, -e1*n],
[0, 0, M2*e2, -e2*n],
[0, 0, 0, e1*e2]
])
AL = A.LLL()
C = Matrix(ZZ, AL[0])
B = A.solve_left(C)[0]
phi1 = floor(e1 * B[1] / B[0])
phi2 = floor(e2 * B[2] / B[0])
print("phi1 =", phi1)
print("phi2 =", phi2)
print()exp.py
n = 159077408219654697980513139040067154659570696914750036579069691821723381989448459903137588324720148582015228465959976312274055844998506120677137485805781117564072817251103154968492955749973403646311198170703330345340987100788144707482536112028286039187104750378366564167383729662815980782817121382587188922253
e1 = 28720970875923431651096339432854172528258265954461865674640550905460254396153781189674547341687577425387833579798322688436040388359600753225864838008717449960738481507237546818409576080342018413998438508242156786918906491731633276138883100372823397583184685654971806498370497526719232024164841910708290088581
e2 = 131021266002802786854388653080729140273443902141665778170604465113620346076511262124829371838724811039714548987535108721308165699613894661841484523537507024099679248417817366537529114819815251239300463529072042548335699747397368129995809673969216724195536938971493436488732311727298655252602350061303755611563
c1 = 125774545911886560112703402972153322080506025378797523936708278181480201146872577291738201370911792392950418121767343486509724963000477466590009600240375221563806039364611362947152096656513910712238094956240996452246301471555709823003175801134035094856941903678067489942047840663479442285170087613352040341832
c2 = 125874844114757588984441500491946737723620819049276461078841545869549114013042058416210220287667061892072831243333341942699313440553285306436999725802970995457080384300690875762412008576026273931144721166609563493297003298586115510199518494430188305644317422640652955882264990001338974742192006748451975507803
from Crypto.Util.number import long_to_bytes
from gmpy2 import invert
phi1 = 159077408219654697980513139040067154659570696914750036579069691821723381989448459903137588324720148582015228465959976312274055844998506120677137485805781092330556185082570865052488981154655643850588559740031994465378408628749828052127213663711396922494795088638471519778995496857305118321851028470398469453660
phi2 = 159077408219654697980513139040067154659570696914750036579069691821723381989448459903137588324720148582015228465959976312274055844998506120677137485805781092330556185082570865052488981154655643850588559740031994465378408628749828052127213663711396922494795088638471519778995496857305118321851028470398469453660
d1 = invert(e1, phi1)
d2 = invert(e2, phi2)
m1 = long_to_bytes(pow(c1, d1, n))
m2 = long_to_bytes(pow(c2, d2, n))
print(m1 + m2)flag
flag{c844b604-8801-402b-92c1-09388fa92095}





Comments 2 条评论
想请教一下密码
@过客 密码我也没咋看明白,直接照抄的exp改了一下参数就能用,大佬原博:多组低解密指数攻击 - RSA | Lazzaro