未分类
逆向签到题
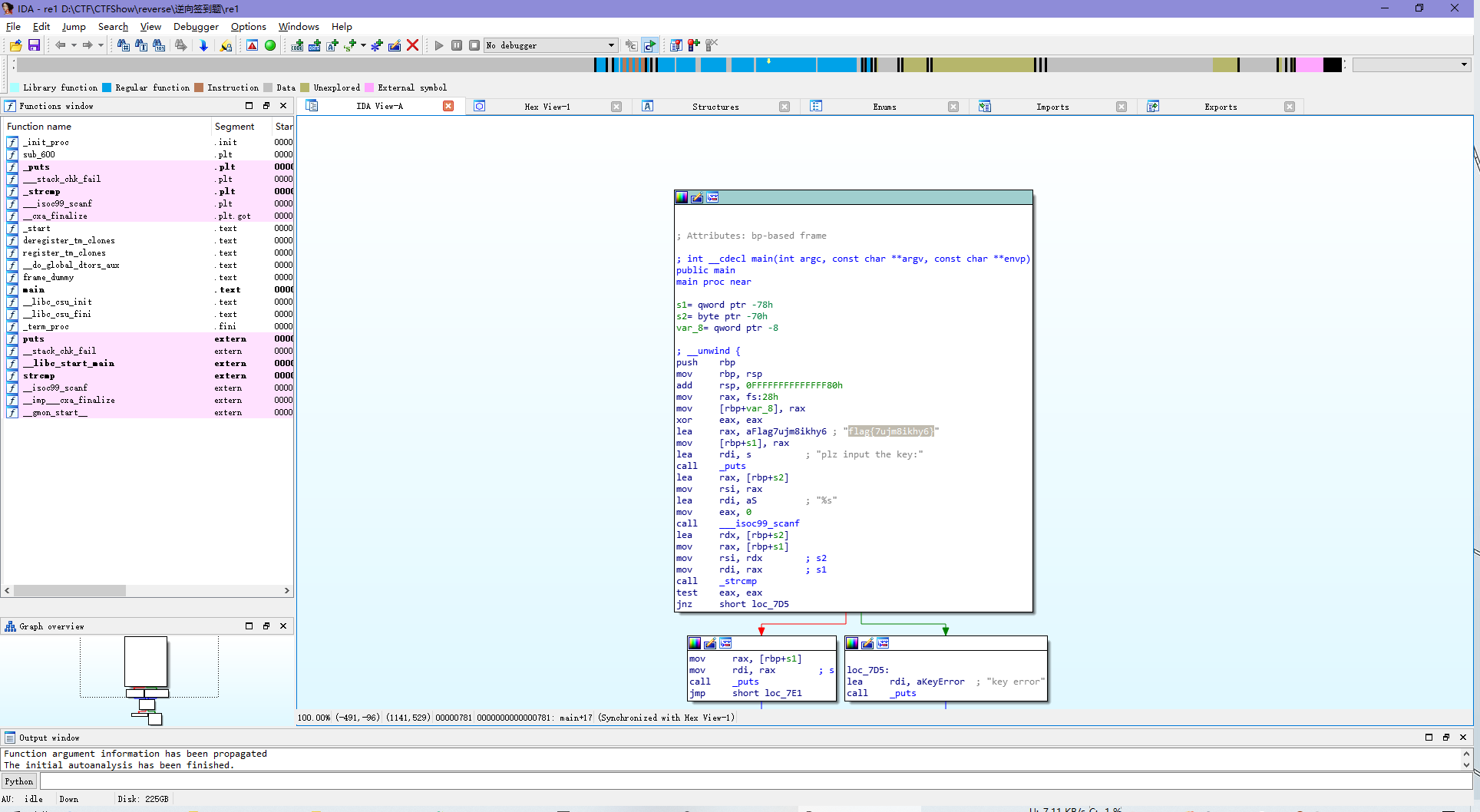
flag
flag{7ujm8ikhy6}
re2
这题我先x32dbg动态了一下找到了main在401DE8。
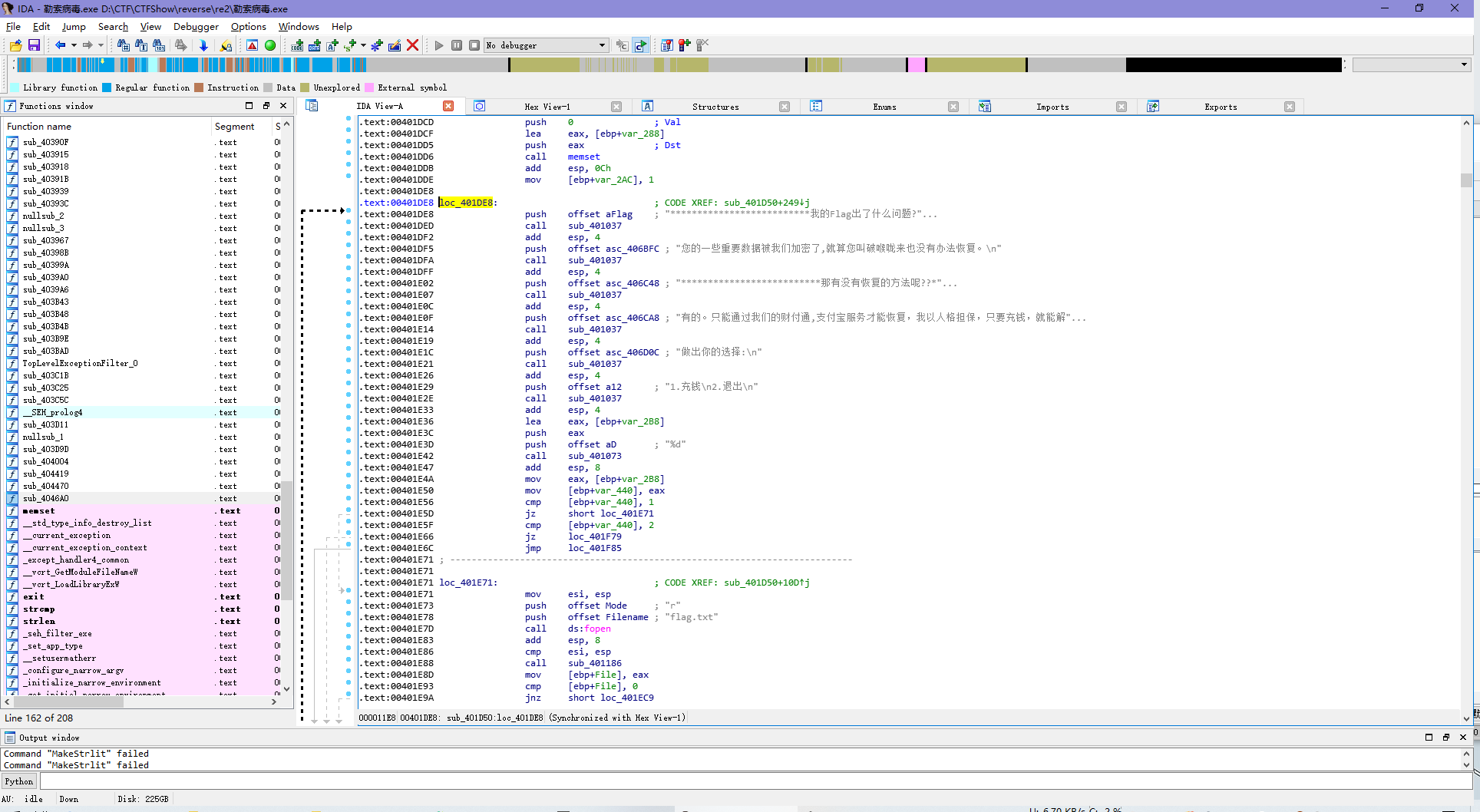
大致看一下可以知道,咱只能选1.充钱,然跳到401E71。
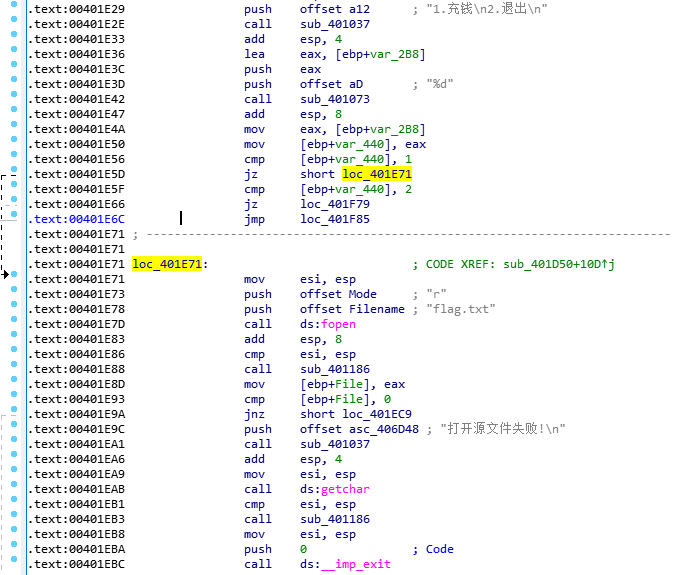
但是因为咱没有flag.txt,所以会直接over,没法到下一跳的401EC9去,但是咱不急,先继续跟着静态一波。
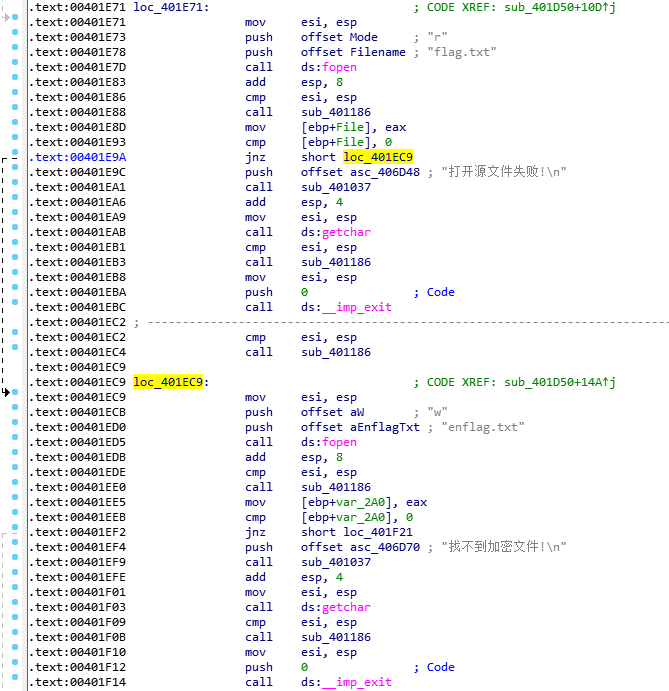
接着打开enflag.txt成功后,就会跳401F21去。
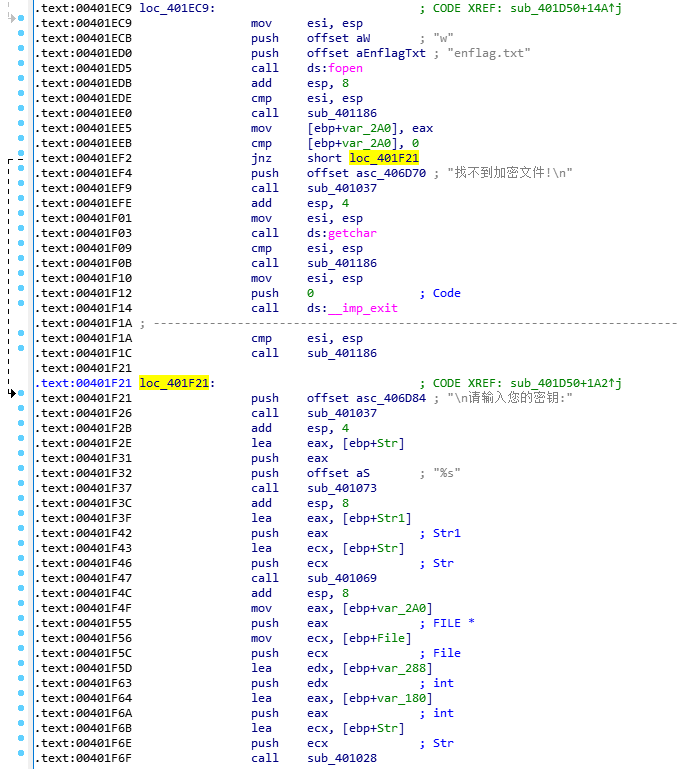
发现重点的来了,我们给几个C库函数重命名一下,方便查看,然后顺带根据文本提示猜一下两个call的用途。
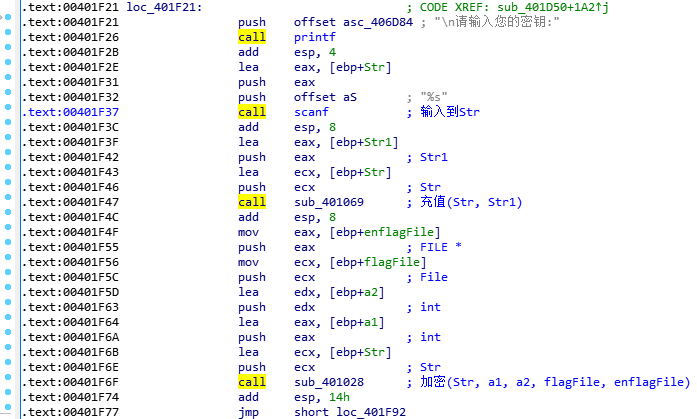
其中401069函数会跳到401A70函数;401028函数会跳到4014E0函数。看一下printf的文本是啥就知道功能了。
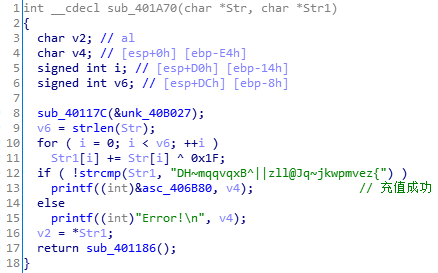
咱一个一个分析,先看充值函数,已知Str是咱输入的密钥,此处将密钥每个字符xor了0x1f后和DH~mqqvqxB^||zll@Jq~jkwpmvez{比较,那么重新xor一下就行。
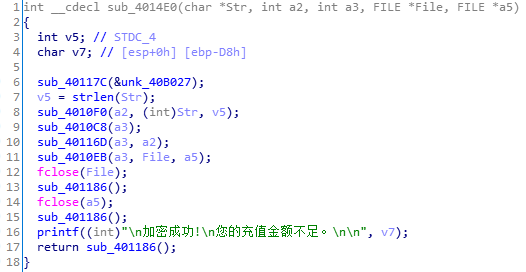
然后再看加密,4010F0总结一下就是a1 = [Str[i % n] for i in range(256)],4010C8就是a2 = [chr(i) for i in range(256)]。
40116D如下:
p = 0
for i in range(0, 256):
p = (ord(a1[i]) + p + ord(a2[i])) % 256
tmp = a2[i]
a2[i] = a2[p]
a2[p] = tmp4010EB如下:
def encode(a2, flag):
a = a2[:]
t = 0
v11 = 0
enflag = ""
for i in flag:
t += 1
v11 = (v11 + ord(a[t])) % 256
tmp = a[t]
a[t] = a[v11]
a[v11] = tmp
enflag += ( ord(a[(ord(a[v11]) + ord(a[t])) % 256]) ^ ord(i) ).to_bytes(1, 'little').hex()
return enflag所以跟flag有关的只有一句^ ord(i),那么逆一遍的话,其实代码几乎一样,就输入输出的类型需要根据自己喜好改一下而已,最后代码如下:
def encode(a2, flag):
a = a2[:]
t = 0
v11 = 0
enflag = ""
for i in flag:
t += 1
v11 = (v11 + ord(a[t])) % 256
tmp = a[t]
a[t] = a[v11]
a[v11] = tmp
enflag += ( ord(a[(ord(a[v11]) + ord(a[t])) % 256]) ^ ord(i) ).to_bytes(1, 'little').hex()
return enflag
def decode(a2, enflag):
a = a2[:]
t = 0
v11 = 0
flag = ""
for i in bytes.fromhex(enflag):
t += 1
v11 = (v11 + ord(a[t])) % 256
tmp = a[t]
a[t] = a[v11]
a[v11] = tmp
flag += chr(ord(a[(ord(a[v11]) + ord(a[t])) % 256]) ^ i)
return flag
if __name__ == '__main__':
Str = "[Warnning]Access_Unauthorized"
Str1 = ""
for i in Str:
Str1 += chr(ord(i) ^ 0x1f)
print(Str1)
n = len(Str)
a1 = [Str[i % n] for i in range(256)]
a2 = [chr(i) for i in range(256)]
p = 0
for i in range(0, 256):
p = (ord(a1[i]) + p + ord(a2[i])) % 256
tmp = a2[i]
a2[i] = a2[p]
a2[p] = tmp
print(a2)
print(decode(a2, "C382A325F64C363B59CCC4E9F1B53218B196AEBF0835"))
flag
flag{RC4&->ENc0d3F1le}





Comments NOTHING